The Recovery Password library item allows you to configure and apply recovery passwords to Mac computers with Apple silicon and EFI firmware passwords to Intel-based Mac computers, all from within the same library item.
Kandji supports automatically generating per-computer passwords with optional configurable time-based rotation, or you can set a manual static password. You can also provide existing known firmware passwords for Intel-based Mac computers to update them using Kandji automatically.
Create a Recovery Password Library Item
To add this Library Item to your Kandji Library, follow the steps outlined in the Library Overview article.
Configure the Recovery Password Library Item
Name your library item, and choose an icon if desired.
Select your desired Blueprints.
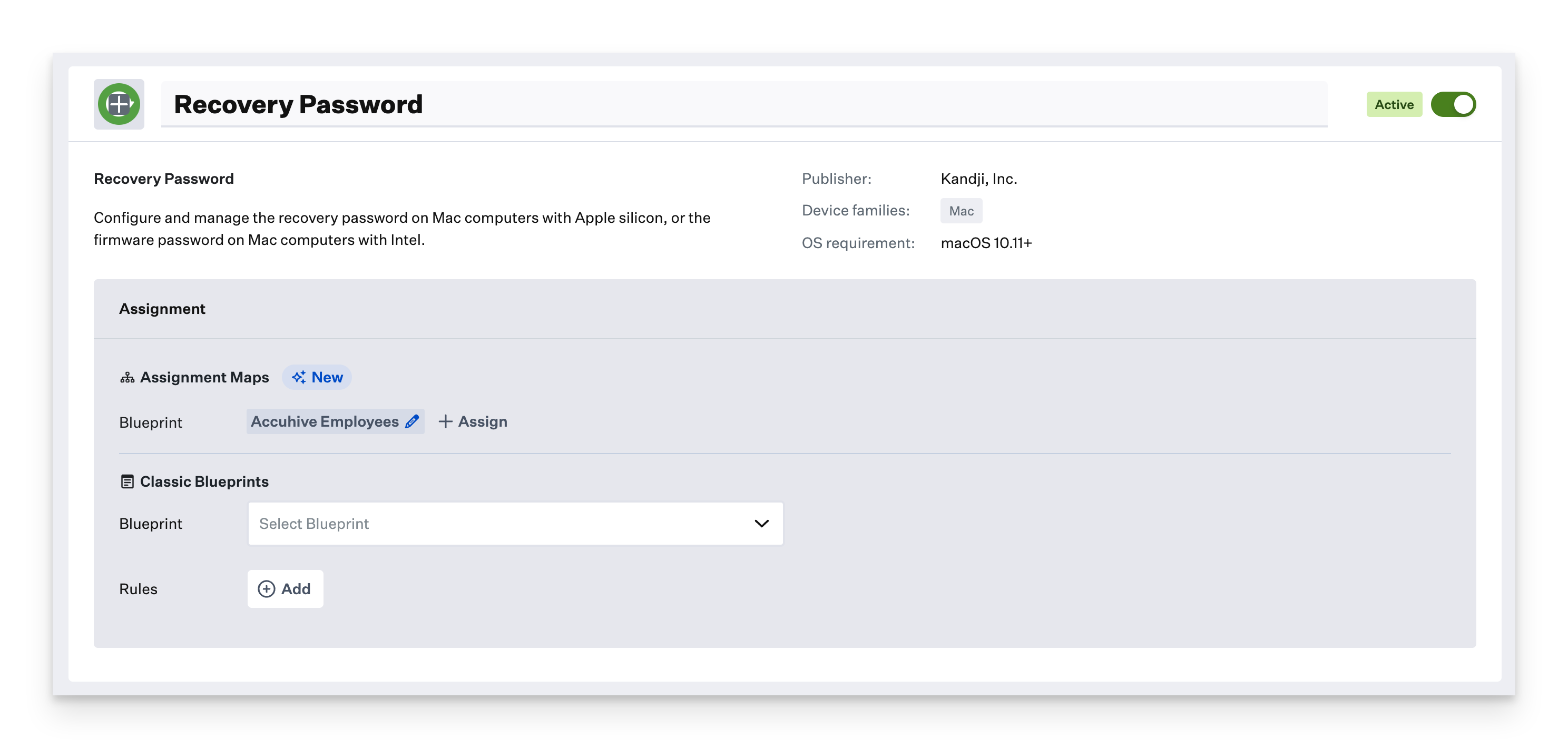
Choose whether to have Kandji automatically generate computer-specific passwords or to specify a static password manually.
If you have Kandji automatically generate computer-specific passwords, choose whether Kandji should automatically rotate the password and specify how often.
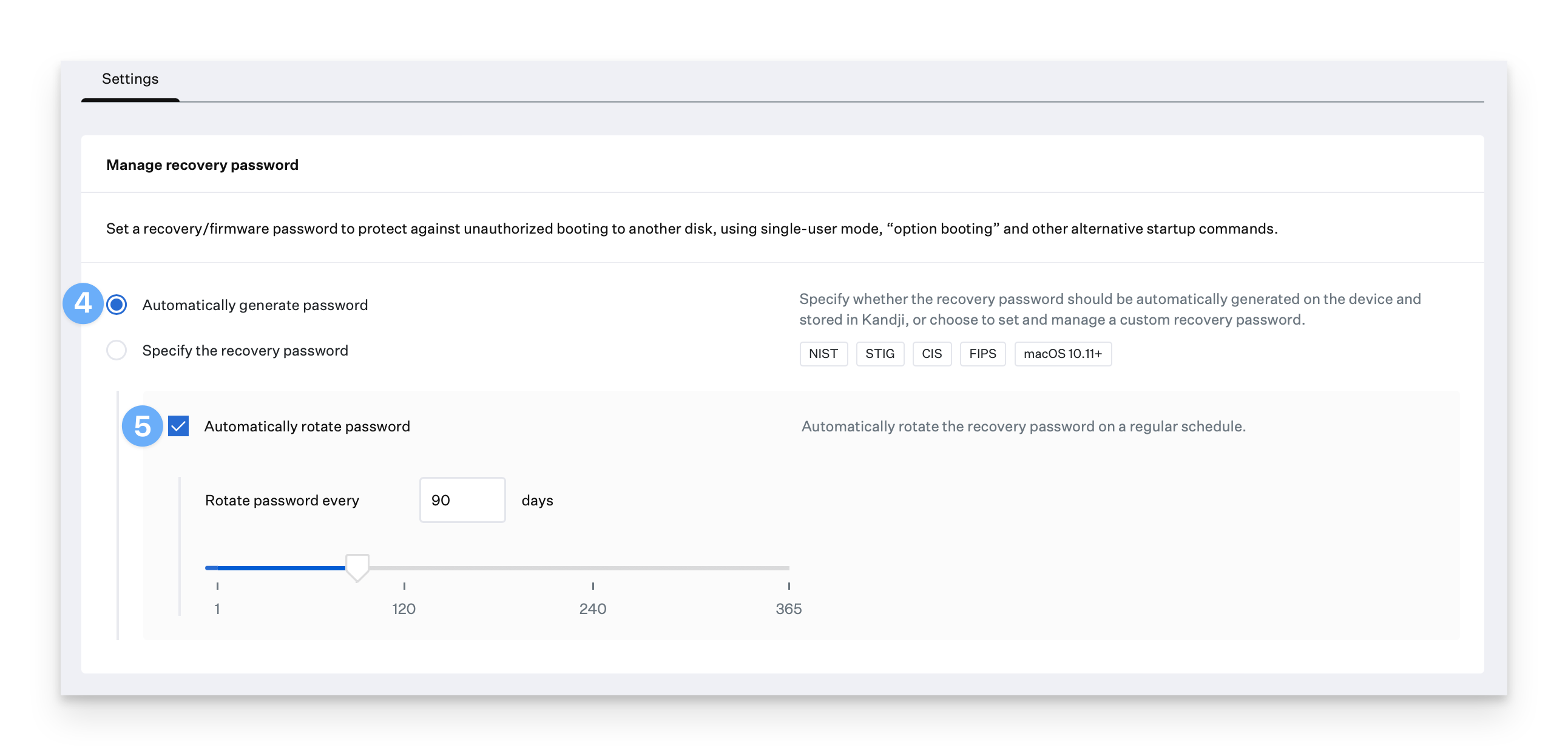
If you have firmware passwords already deployed to Intel-based Mac computers, enable the Legacy Firmware passwords option so Kandji can update them.
Add a Legacy password already deployed to Intel-based Mac computers
Optionally add up to 19 more legacy passwords(20 total) for Kandji to use when updating them.
Click Save.
Kandji cannot update existing deployed firmware passwords on Intel-based Mac computers unless the currently in-use password(s) are provided to Kandji in the Legacy Firmware passwords section.
Device Experience
Mac computers with Apple silicon: The recovery password is applied and no user interaction is required.
Intel-based Mac computers: Users are prompted by the Kandji Agent to restart within 30 minutes after a legacy firmware password is applied, whether for the first time or when being rotated. As with the FileVault library item, this counter can not be deferred.
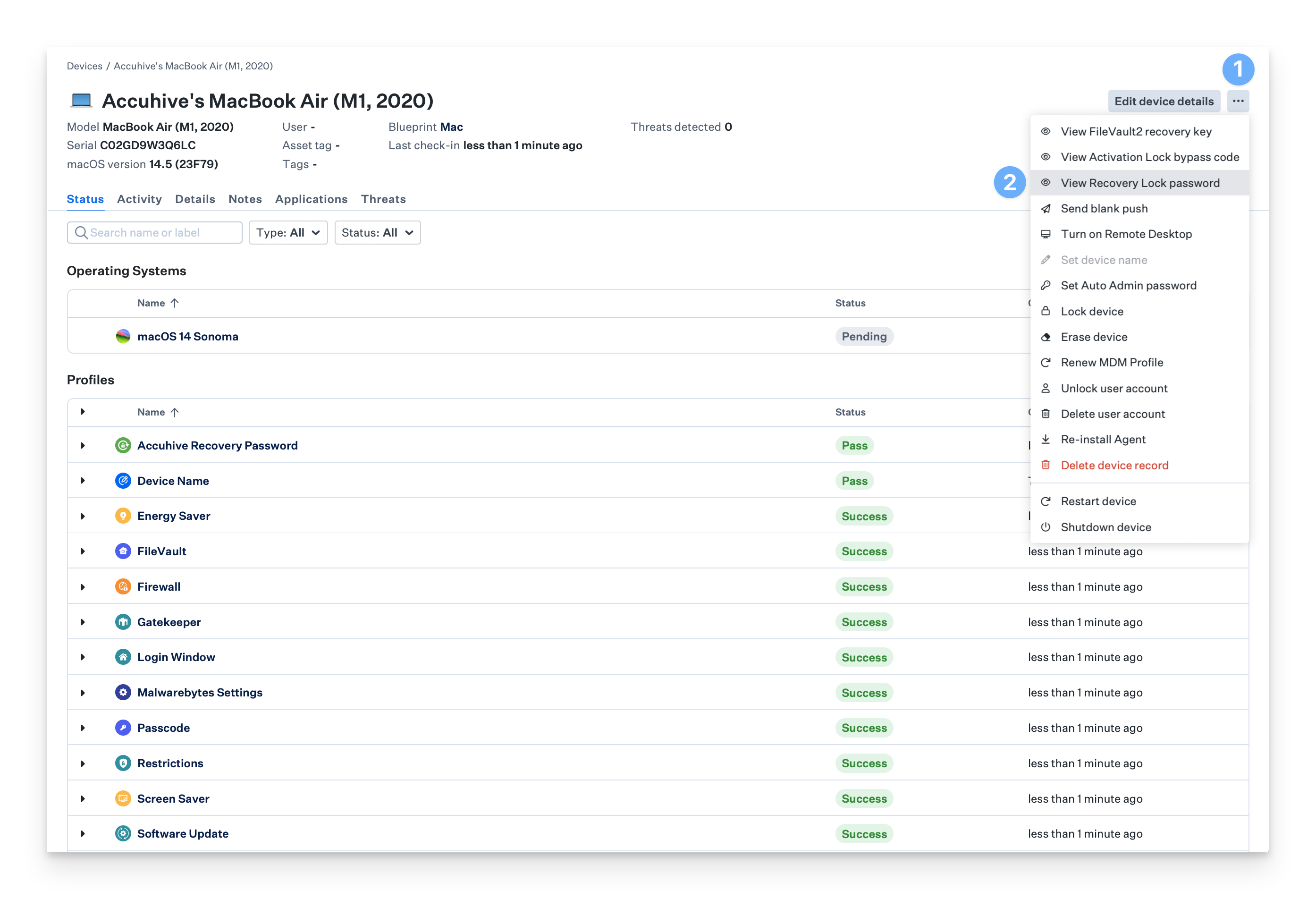
View Recovery Password for a Device
After the recovery password has been set, this option becomes available when the device's next daily check-in completes.
Open the Device Action Menu.
Click View Recovery Lock password.
When removing the Recovery Password library item, the recovery password will still show on the device record, even though there won’t be a visible password. This will be removed from the device record at the next daily check-in.
Additional Considerations
When changing Blueprints, Kandji will attempt to use the last-known recovery password or legacy firmware password to adjust the device's settings so they align with settings applied to the new Blueprint. For example, if Blueprint 1 has a Recovery Password library item with a randomized recovery password, but Blueprint 2 has a fixed recovery password, moving a device from Blueprint 1 to Blueprint 2 will change the device's recovery password to the fixed password automatically.
When removing a Recovery Password library item from a Blueprint or moving the device to a Blueprint without a Recovery Password library item, Kandji will attempt to remove the last-known recovery password or legacy firmware password from the device.
When deleting a device record, which unenrolls the device from Kandji, any applied recovery password is automatically removed by macOS. Legacy firmware passwords are not automatically removed.
When Automatically generate password is selected in the Recovery Password library item and the recovery password is then used to unlock a device, please be sure to enter the recovery password exactly as it appears- in all capital letters and with hyphens.
Intel-based Mac computers with the Apple T2 Security Chip will perform an Erase All Content and Settings (EACS) when receiving an Erase Device command from Kandji. If a legacy firmware password is still present on the device when it receives the command, it will instead completely erase and require reinstallation of macOS, as in macOS 11. To preserve the EACS behavior on an Intel-based Mac, first, move it to a Blueprint without a Recovery Password library item before sending the Erase Device command. This step is not required for Mac computers with Apple silicon.