What is a Single Sign-On Extension?
A Single Sign-On (SSO) extension is a type of application for macOS, iOS, iPadOS, and visionOS that leverages Apple's Extensible Enterprise Single Sign-on framework. These applications, or extensions, let identity providers (IdPs) build applications that allow for a seamless SSO experience across native macOS applications and browsers. This allows an end user to sign in once to the extension and be authenticated across macOS, iOS, iPadOS, and visionOS. SSO extensions can also allow for synchronizing a user's local macOS password with their IdP password.
When deploying Okta Device Trust, this Single Sign-On Extension is not required separately because the functionality of the SSO Extension is included as part of the Okta Device Trust deployment.
How Can I Deploy a Single Sign-On Extension?
For iOS, iPadOS, and visionOS extensions, it is required to first deploy the app containing the SSO extension via Apps and Books from Apple Business Manager.
For macOS extensions, it is required to first deploy the app containing the SSO extension via Apps and Books from Apple Business Manager or via a custom app in Kandji.
After deploying the extension, you will then configure and deploy a Single Sign-On profile to the devices.
Configure a Single Sign-On Extension Profile
To add this Library Item to your Kandji Library, follow the steps outlined in the Library Overview article.
Give the new Custom Script Library Item a Name.
Assign to your desired Blueprints.
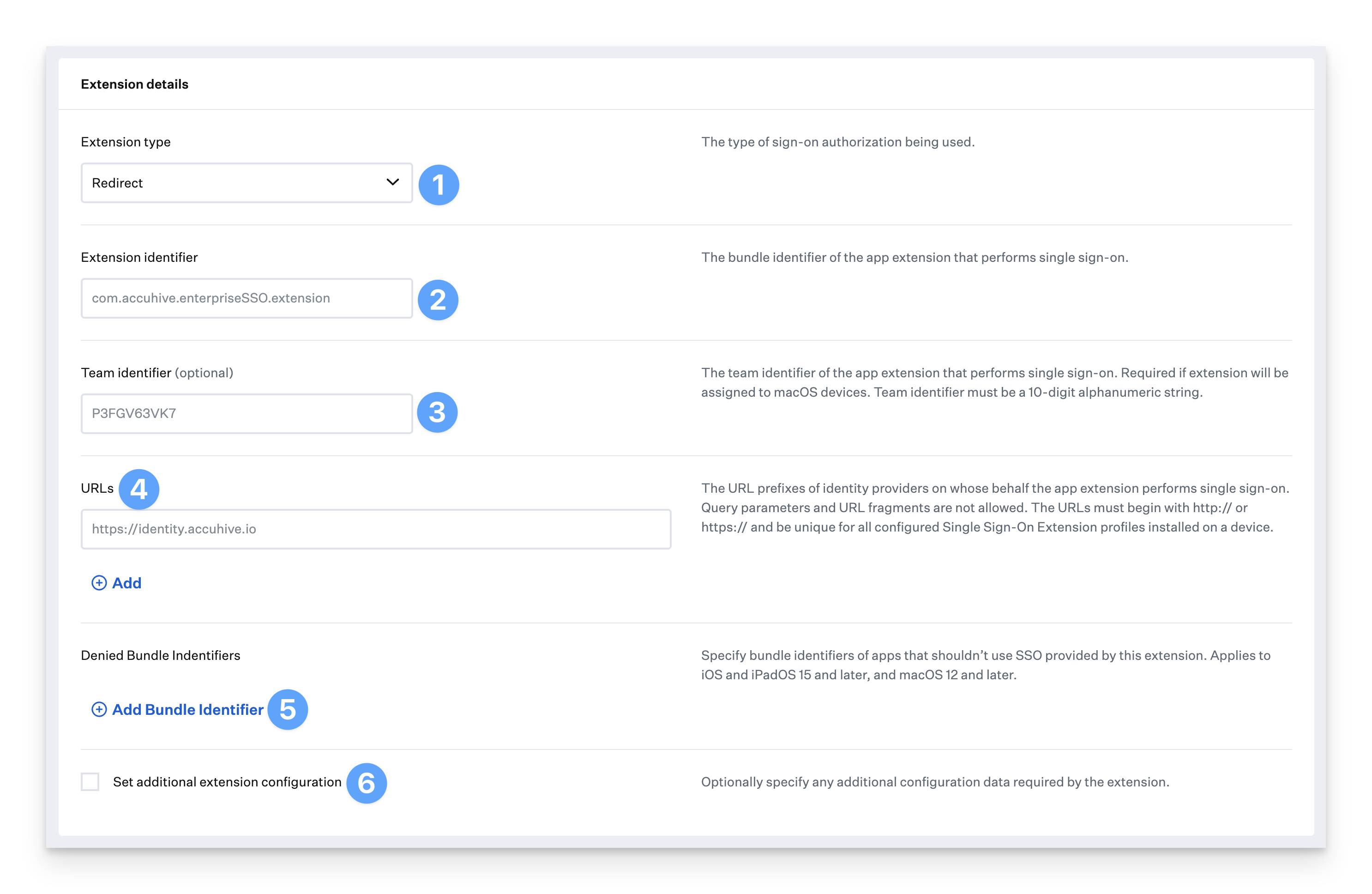
Redirect Single Sign-On Extension Profile
Extension Type: This option refers to the type of SSO extension. Choose Redirect from the drop-down menu.
Extension Identifier: In this option, you specify the Bundle ID of the SSO extension. The Bundle ID can be found by inspecting the app's info.plist file.
Team Identifier: The team identifier of the app extension that performs single sign-on. Required if the extension will be assigned to macOS devices.
URLs: This option allows you to specify the URL prefix on behalf of which the SSO extension will authenticate.
Denied Bundle Identifiers: Specify bundle identifiers of apps that shouldn’t use SSO provided by this extension. Applies to iOS and iPadOS 15 and later, and macOS 12 and later.
Set additional extension configuration: Optionally specify any additional configuration data required by the extension.
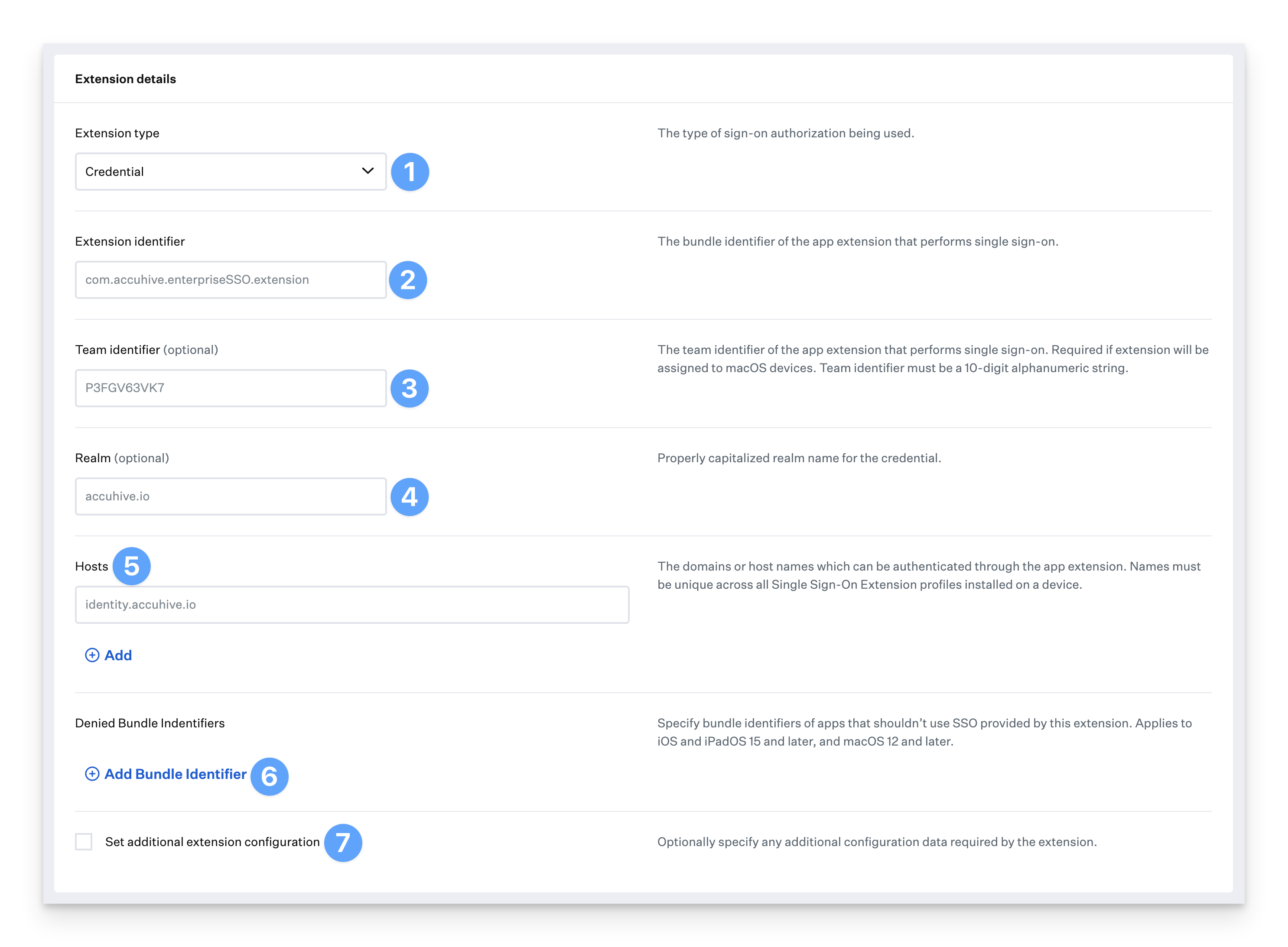
Credential Single Sign-On Extension Profile
Extension type: This option refers to the type of SSO extension. Choose Credential from the drop-down menu.
Extension Identifier: In this option, you specify the Bundle ID of the SSO extension. The Bundle ID can be found by inspecting the app's info.plist file.
Team Identifier: The team identifier of the app extension that performs single sign-on. Required if the extension will be assigned to macOS devices.
Realm: This option will be displayed only if the credential type is Credential. Typically, this is in reference to a Kerberos realm when leveraging the Kerberos extension.
Hosts: This option allows you to specify which host can be authenticated through the SSO extension. An example would be an ADFS instance.
Denied Bundle Identifiers: Specify bundle identifiers of apps that shouldn’t use SSO provided by this extension. Applies to iOS and iPadOS 15 and later, and macOS 12 and later.
Set additional extension configuration: Optionally specify any additional configuration data required by the extension.
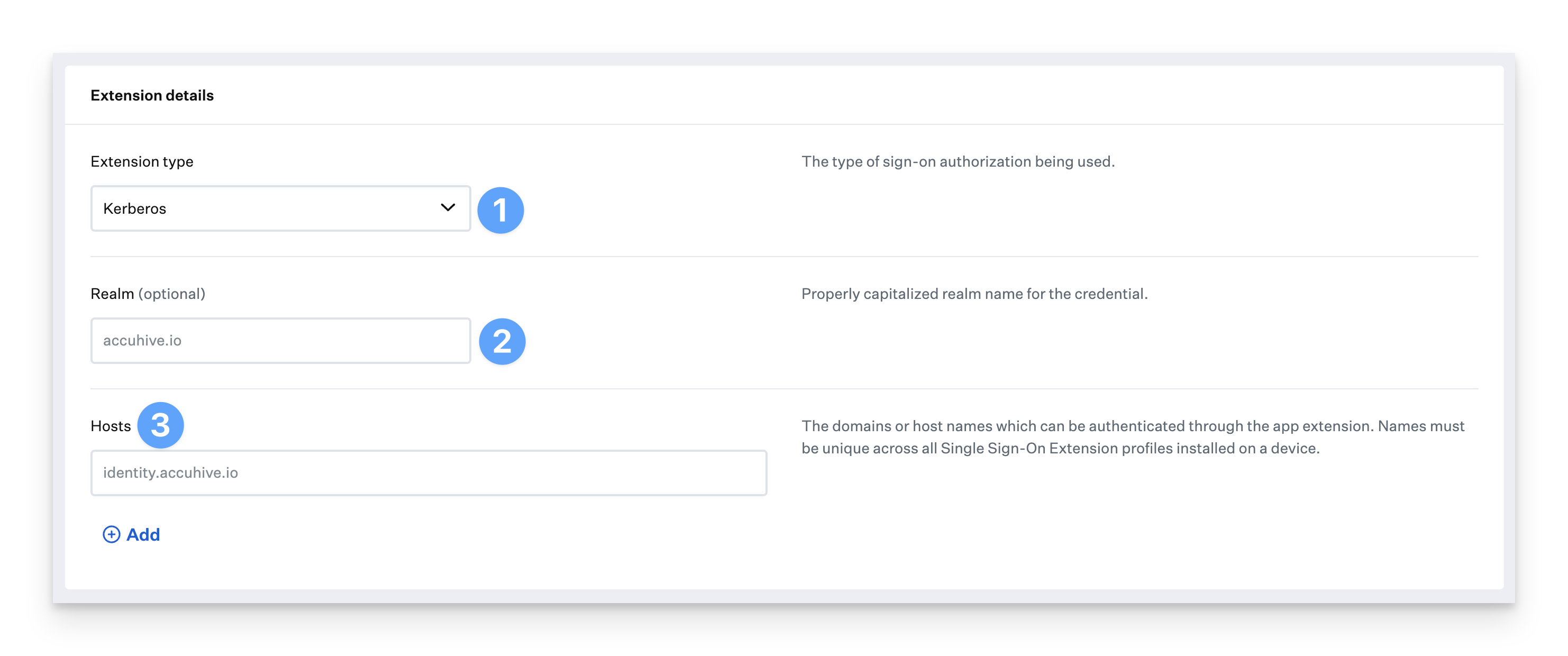
Configure a Single Sign-On Extension Profile for Apple's Kerberos Extension
Extension type: This option refers to the type of SSO extension. Choose Kerberos from the drop-down menu.
Realm: Set the Realm to the capitalized form of your Active Directory domain name (i.e. accuhive.io becomes ACCUHIVE.IO)
Hosts: This can be left empty. If you have enterprise applications leveraging ADFS, and ADFS is configured to accept Kerberos authentication, you can add the host to your ADFS server here. (i.e. adfs.accuhive.io)
Under the Password Options section, you can configure all of the available Kerberos extension options (such as syncing the local user password).
What is Platform SSO?
Platform SSO allows Single Sign-On Extensions to extend their functionality to the macOS login window. This will allow users to unlock their Mac using an IdP password and, just-in-time creation of local accounts on a shared Mac using credentials from an organization’s Identity Provider (IdP). The local account password is automatically kept in sync, so the cloud password and local passwords match. Permissions and local group memberships can be managed, and this also extends to IdP users who don't have a local account, so those credentials can be used at authorization prompts.
Platform SSO requires macOS 14 Sonoma or later, and in addition to the Platform SSO profile payload deployed by Kandji, a properly configured Single-Sign On Extension App from your Identity Provider.
Configure Platform SSO
If you selected Kerberos as the extension type, the Platform SSO section will be unavailable, as they are not complimentary technologies.
The Platform SSO section is inactive by default. Toggle the radio button to expand and configure it:
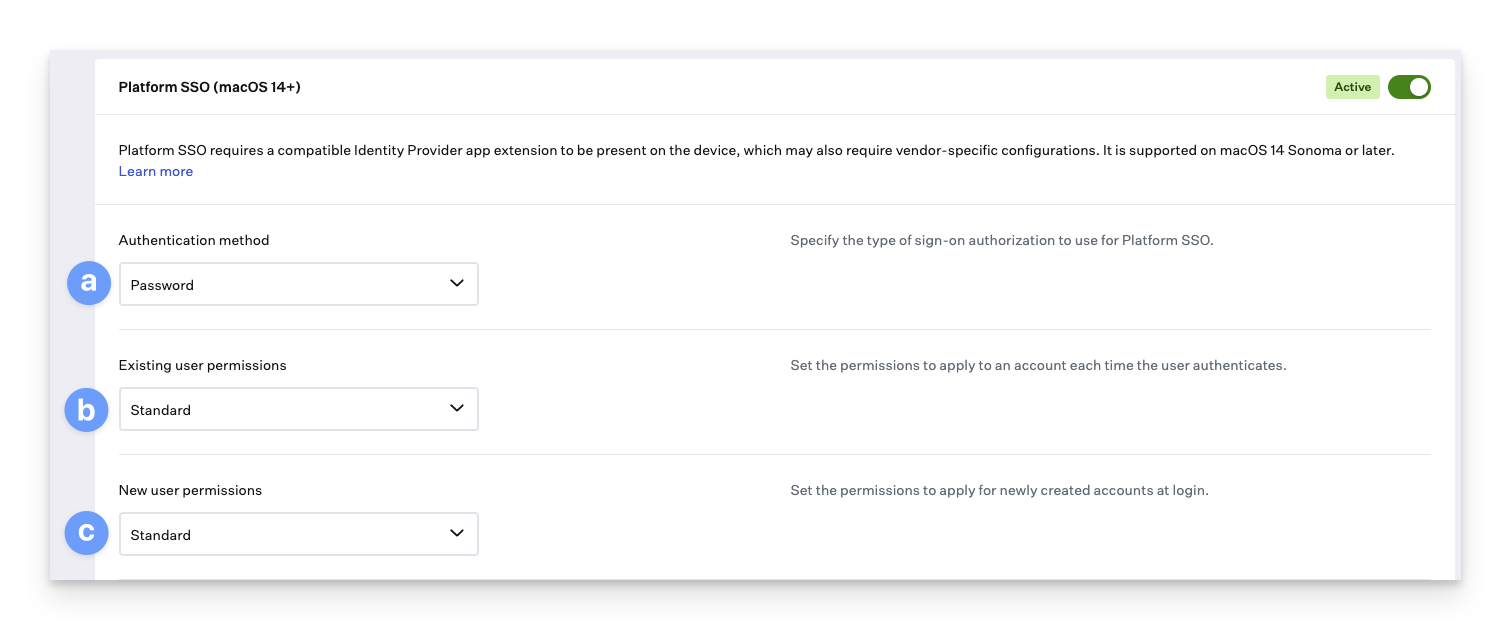
Select the authentication method. The SSO Extension must support this authentication method.
Select the permissions group that existing local user accounts should have at login: Standard, administrator, or groups that will be specified in later steps.
Select the permissions group that new accounts created at the login window should have.
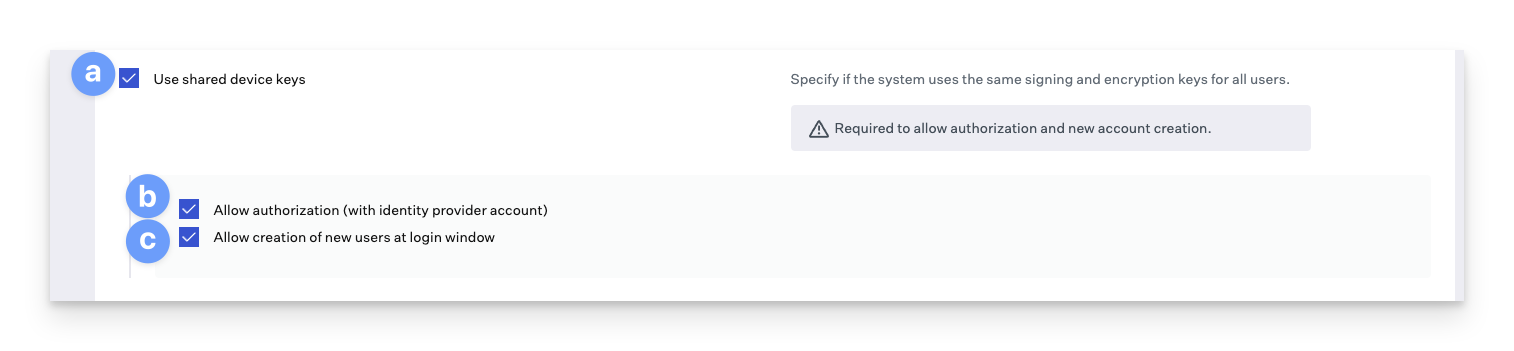
If you would like to allow account creation at the login window, which is helpful for shared devices, configure shared device key usage:
Select Use shared device keys.
Allow authorization (with identity provider account) will let users interact with system authorization prompts using their IdP credentials.
If you want to have local accounts created automatically for users, select Allow creation of new users at login window.
Local account creation requires the device to be online, at login window with FileVault unlocked and for Kandji to have a valid Bootstrap token for the device.
Login Options & Groups
Next, you'll configure a few more login options:
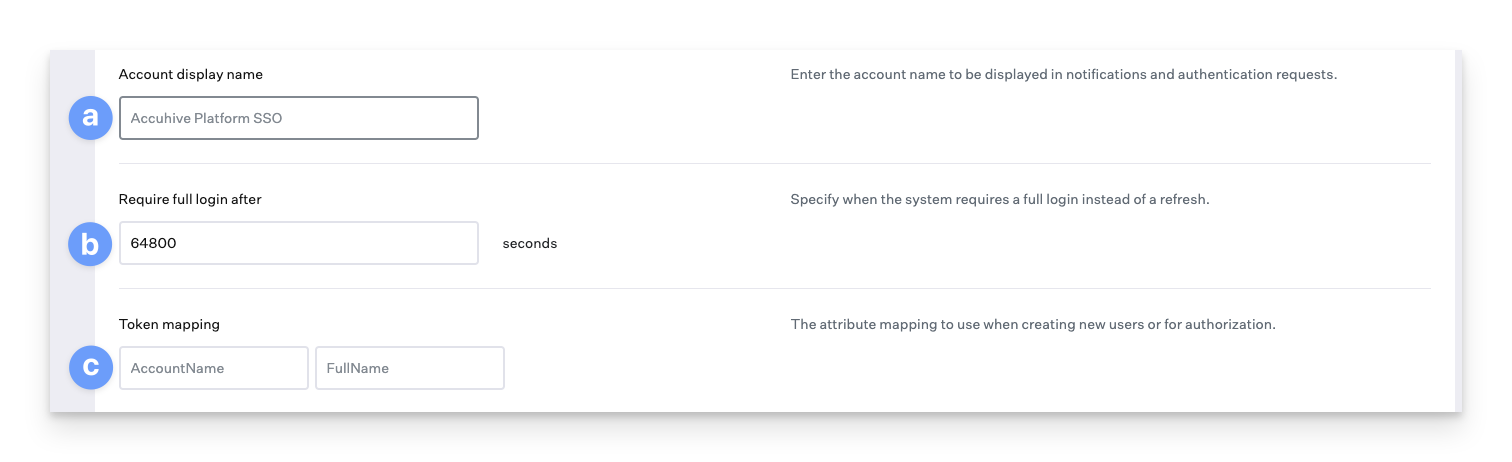
The account display name will typically be your organization's name or something your users will recognize as it appears in notifications and authentication requests.
A full login can be required after a certain amount of time. The default is 18 hours (64800 seconds), and the minimum value is 1 hour (3600 seconds).
The attribute mapping to use when creating new users or for authorization.
Finally, you can configure authorization groups which will allow users or IT staff to have specific permissions on the device. There are three different types of groups:
Admin groups are groups from your IdP that should have administrator access on the device.
Additional groups are ones you would like to see created in the device's local directory.
User groups are most useful: They allow you to map specific macOS systems rights to arbitrary groups that will be created in the local directory. For example, to grant 'sudo' or printer management access.