The Certificate Library Item allows you to upload certificates and certificate identities and deploy them to your Apple devices. You might want to use this Library Item if you are configuring services that require a valid certificate trust chain or apps that support certificate-based authentication.
Create a Certificate Profile
Navigate to Library in the left-hand navigation bar.
Select Add New from the upper right-hand corner.
Select the Certificate library item and click Add & Configure.
Give your Library Item a descriptive title.
Assign the Certificate library item to a Blueprint.
Certificates
Select the certificate type you are deploying.
PKCS #1-formated certificate files have a file extension of .cer, .crt, or .der. They contain a certificate without a corresponding private key.
PKCS #12-formated certificate files have a file extension of .p12 or .pfx. They contain a certificate and corresponding private key. To configure the Certificate Library item for PKCS #12, see the PKCS #12-formatted Certificates section below.
AD CS certificates are generated from a Microsoft Active Directory Certificate Services PKI environment. To configure the Certificate Library Item for AD CS, see the AD CS Certificates section below.
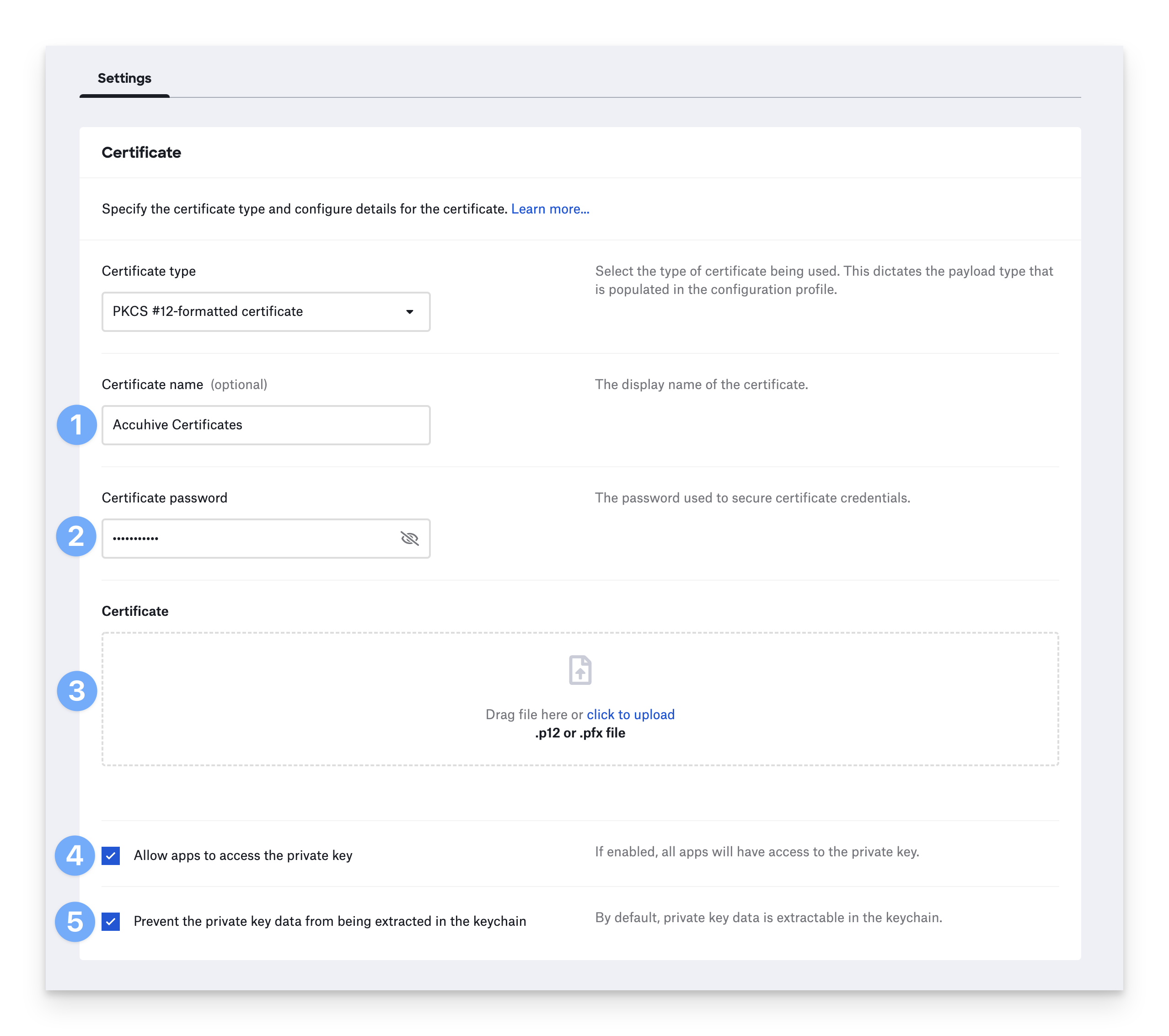
PKCS #12-formatted Certificates
If the PKCS #12-formatted certificate type was chosen, use the steps below to complete the configuration according to the needs of your environment.
Certificate name - Give the certificate a name that will appear on the configuration profile shown in System Preferences.
Certificate password - This option appears when you select the PKCS #12-formatted certificate type. Enter the password used to decrypt the certificate identity.
Certificate - Click to upload your certificate or certificate identity file. You can also drag it onto the Certificate box.
Allow apps to access the private key - This option appears when you select the PKCS #12-formatted certificate or AD CS Certificate types. By selecting it, all apps on the Mac will automatically be able to use the certificate identity. This is useful if you use the identity with apps or services that support certificate-based authentication. If you deselect this option, users with administrator privileges will need to use the Keychain app to allow the use of the certificate identity.
Prevent the private key data from being extracted from the keychain - This option appears when you select the PKCS #12-formatted certificate or AD CS Certificate types. It prevents the certificate identity’s private key from being exported from the macOS keychain and ensures the identity is only used on the Mac it was deployed to.
Click Save.
AD CS Certificates
If the AD CS certificate type was chosen, use the steps below to complete the configuration according to the needs of your environment.
To deploy AD CS certificates via Kandji, the AD CS Integration must first be set up and configured.
Enter a Certificate name. This will appear on the configuration profile shown in System Settings.
Enter a Certificate subject. The Certificate subject is typically used to identify the device within the Certificate Authority. This can be anything that you would like, such as the Kandji Global Variable $SERIAL_NUMBER. Using the $SERIAL_NUMBER global variable will insert the device serial number into the profile before sending it to the device.
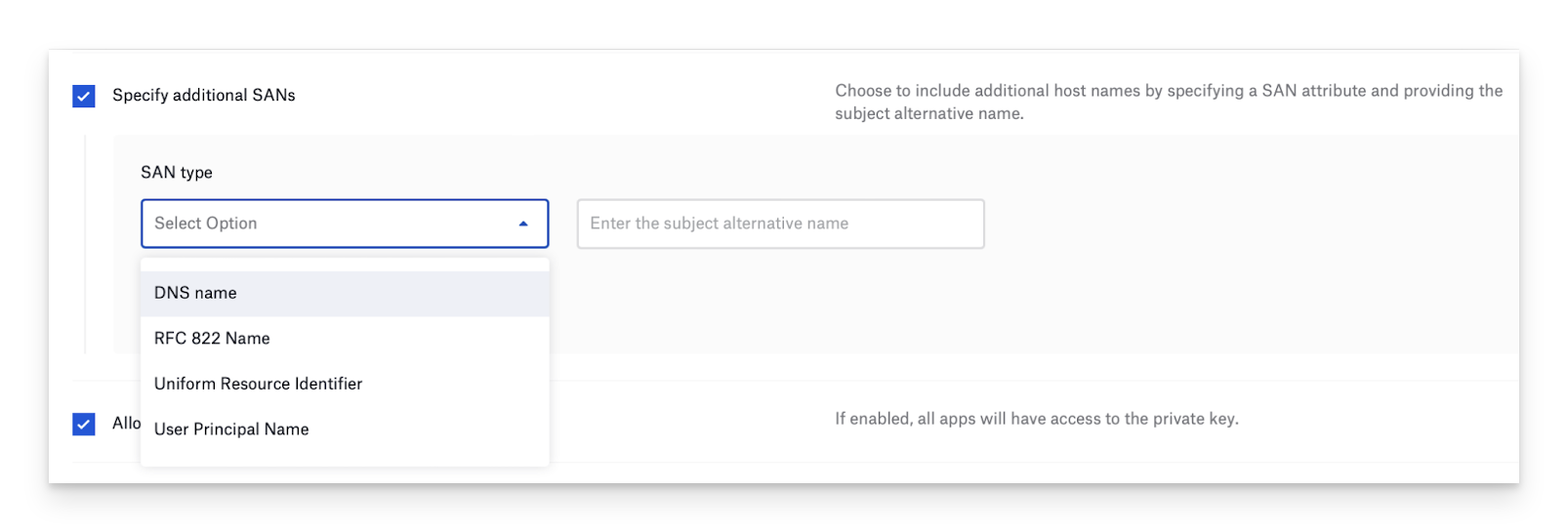
Optionally, if your environment requires it, you can Specify additional Subject Alternative Names (SANs) to be sent in the request.
Enter a Template name. This is the name of the AD CS computer certificate template used to generate AD CS certificates.
Select an AD CS server from the drop-down menu. AD CS servers are added during the setup of the AD CS integration.
Select a Key size for the certificate.
Optionally, select Allow apps to access the private key.This can be useful for apps that support certificate-based authentication.
Optionally, select Prevent the private key data from being extracted from the keychain.
Click Save.
