What is Vulnerability Response?
Vulnerability Response enables you to automate the handling of security vulnerabilities (CVEs) for macOS apps that exist in the Auto App catalog. You can set up rules that tell Kandji how to respond based on the severity of each CVE; when Kandji identifies an app with a known vulnerability, it can automatically update that app according to the rules you’ve put in place. This helps keep your apps secure without requiring an administrator to manually intervene each time a vulnerability is discovered.
How Vulnerability Response Works
Vulnerability Response scans and remediates all installed applications with a matching bundle ID in the Auto App catalog, even if the Auto App Library Item is not currently in your Library or assigned to a Blueprint. If an app is affected by multiple vulnerabilities with different severities, Vulnerability Response will perform the selected remediation action only for the highest applicable severity.
On each Kandji Agent check-in, Vulnerability Response compares the applications installed on your Mac fleet against existing CVEs in the NVD. If a match is found between a CVE and an installed app, Vulnerability Response will flag that match and perform the selected Remediation Action against the app to mitigate the vulnerability, if a matching bundle ID is found in the Auto App catalog.
Vulnerabilities in apps not supported as Auto Apps must be updated directly by the app developer. Requests for additional Auto App support can be submitted through the Kandji Web App using the Feature Requests button.
Remediating Vulnerabilities
Available Remediation Actions
Vulnerability Response supports a variety of remediation actions to choose from when deciding how a security vulnerability in an Auto App is handled:
Enforce update upon detection
When a vulnerability is found, Kandji immediately updates the affected app to the latest version.
Enforce update on a timeframe
When you choose a timeframe, Kandji will update the app based on the selected enforcement timeframe.
No Action
If a vulnerability at this severity level is found, Kandji won’t take any action.
The Kandji Agent respects the user’s local time zone for update enforcement.
Viewing Remediated CVEs
When all affected software and devices associated with a CVE are patched, the CVE is assigned a Remediated status.
Navigate to the Vulnerability Management tab.
Use the Status filter and select Remediated.
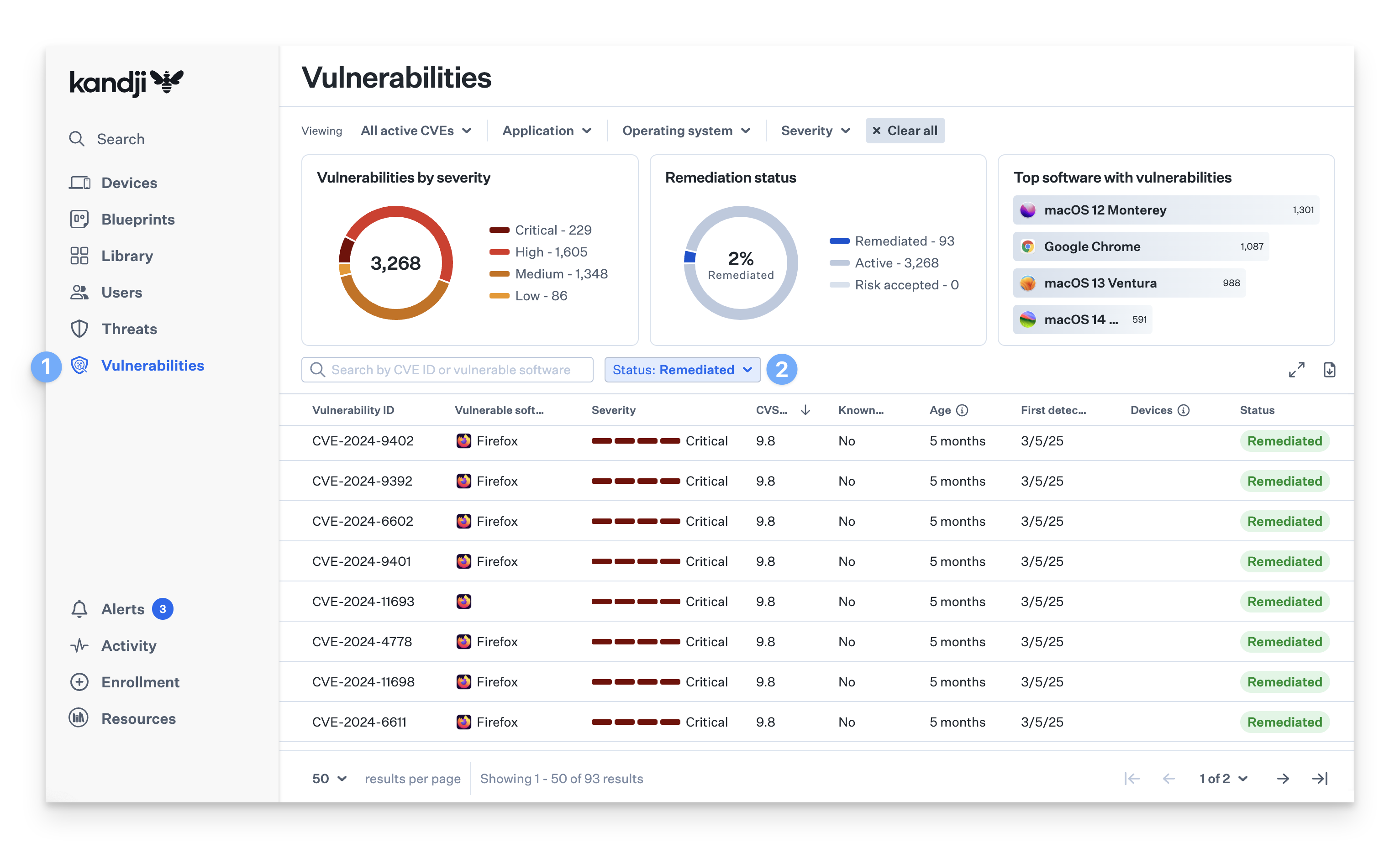
The Remediated status includes any CVE where all detections related to that CVE are no longer present on any monitored device. Use the Remediation Status data card to view the overall percentage of CVEs that have been fully remediated in your environment.
CVE Detail View
Selecting a specific CVE opens its detail view, where you can monitor progress and review device status related to that vulnerability.
.png)
Within the detail view, you’ll see the percentage of devices remediated out of the total detections for the selected CVE. Hovering over this percentage reveals the exact device counts for both remediated (no longer vulnerable) and active (still vulnerable) devices.
If the CVE has achieved a Remediated status, the Timeline tab is available by default, allowing you to track the history and remediation events associated with the CVE.
Add and Configure the Vulnerability Response Library Item
To add this Library Item to your Kandji Library, follow the steps outlined in the Library Overview article.
Give the Vulnerability Response Library Item a name.
Select the Blueprint(s) you want to assign this Library Item to.
Select the Remediation action for each CVE severity level.
Click Add application in order to exclude an application from the auto-remediation rules. You can select apps you wish not to be auto-remediated from the library. If a vulnerability is detected on an application you have excluded, Vulnerability Response will take no action.
Click Save.
.png)
User Experience with Vulnerability Response
Updates are delivered silently to the end user, following the same workflow as Auto Apps.
When an enforcement deadline is reached and the affected app is open, users will see a prompt with a 5-minute countdown to close the application and save work. If the app is not closed, it will be forcibly closed and updated. After updating, the app will reopen.
Considerations
Only app-based vulnerabilities are remediated, and only when Kandji provides a supported Auto App for the application.
Deployment occurs via the Kandji Agent, which is pre-installed on all enrolled Mac computers. No additional installation or configuration is needed; simply assign the Vulnerability Response Library Item to your Blueprints.
Vulnerability Response can update supported apps even if you are not also using the Auto App Library Item for that app.
Vulnerability Response updates vulnerable apps; it does not block them at launch. The App Blocking Library Item can be used to block apps if required.
If both an Auto App and a Vulnerability Response Library Item are targeting the same application, Vulnerability Response will update the app if the vulnerability is detected before the Auto App enforcement deadline.
If a Mac is assigned both Vulnerability Response and Auto App Library Items with different enforcement deadlines for the same app, the earliest enforcement deadline will apply.
Multiple Vulnerability Response Library Items can be configured within a Blueprint for different groups, but only one may be assigned per device. If a device qualifies for more than one, the last (furthest right in the Assignment Map) is applied.
If a CVE previously marked as "Risk Accepted" is patched, its status will change to "Remediated." If the vulnerability is detected again and the policy isn't updated, its status will revert to "Risk Accepted."
Please see our Vulnerability Management Overview article for more information about vulnerabilities.