Kandji’s Vulnerability Management feature scans your entire fleet for known vulnerabilities (CVEs) based on data from the National Vulnerability Database (NVD), providing a clear, organized way to monitor and respond to vulnerabilities across your fleet. By using the different views—Vulnerability, Application, and Devices—you can quickly assess which threats need immediate attention and act accordingly.
Defining Vulnerabilities
Vulnerability Management identifies any known Common Vulnerabilities and Exposures (CVEs) within your fleet, leveraging information from the National Vulnerability Database (NVD). From the Vulnerabilities page in the Kandji Web App, you can view all relevant CVEs for specific applications. Not every CVE poses the same level of threat—some may be critical and require immediate attention, while others might be less urgent or not relevant to your environment. Please see our Accepting CVE Risks article for more information about how to accept CVE risks.
Vulnerabilities View
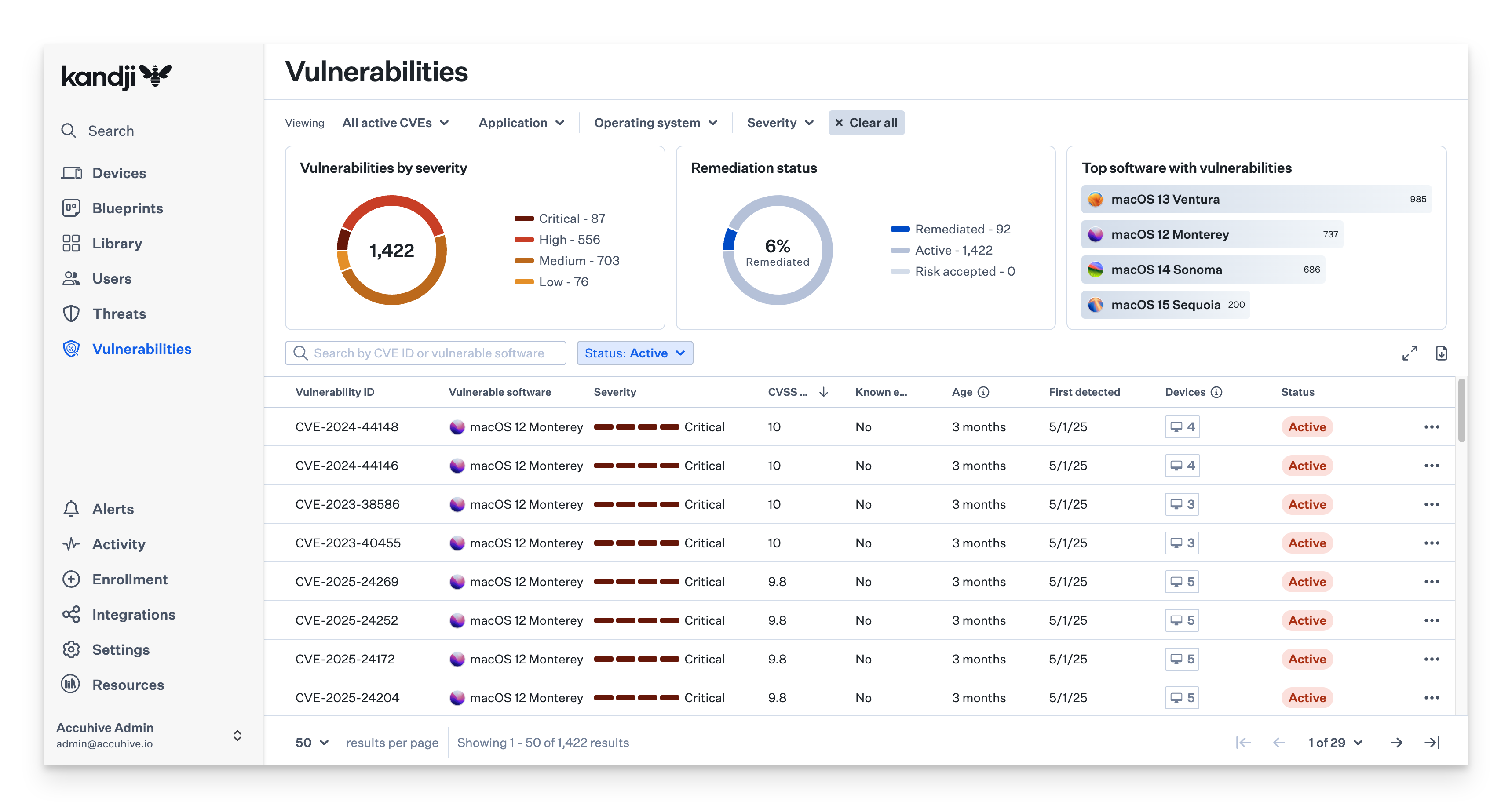
The Vulnerabilities View provides a complete list of all detected CVEs across your fleet. You can search for specific vulnerabilities by:
Vulnerability ID
Vulnerable software
Severity
First detected date
Filter by application or macOS version.
These filters help you prioritize what needs attention first based on the severity and timing of the vulnerabilities.
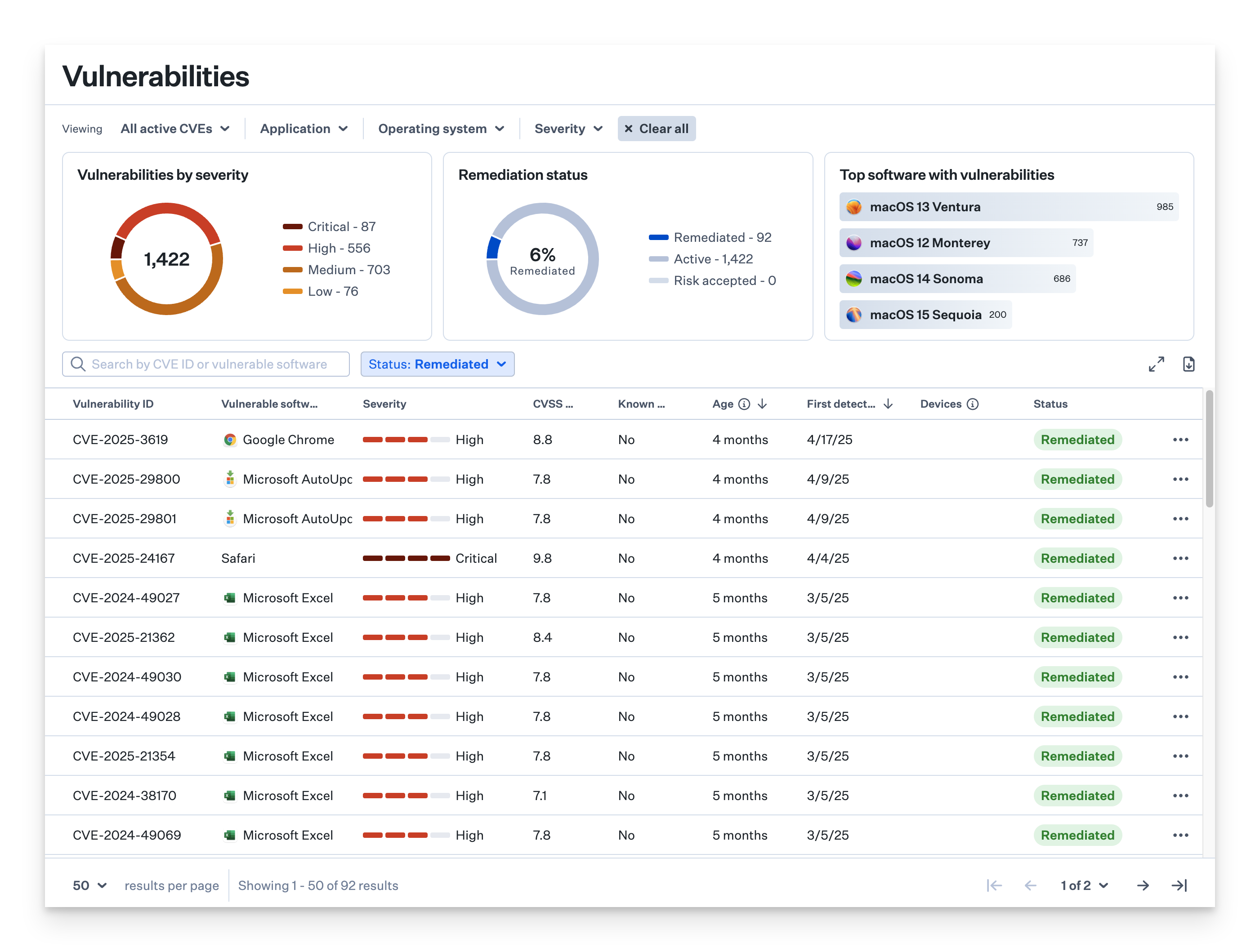
Remediation Filtering
When all vulnerable software and devices impacted by a CVE are patched, the CVE will have a Remediated status.
Use the Status filter and select Remediated.
The list will be filtered to display only CVEs for which the CVE was fully remediated.
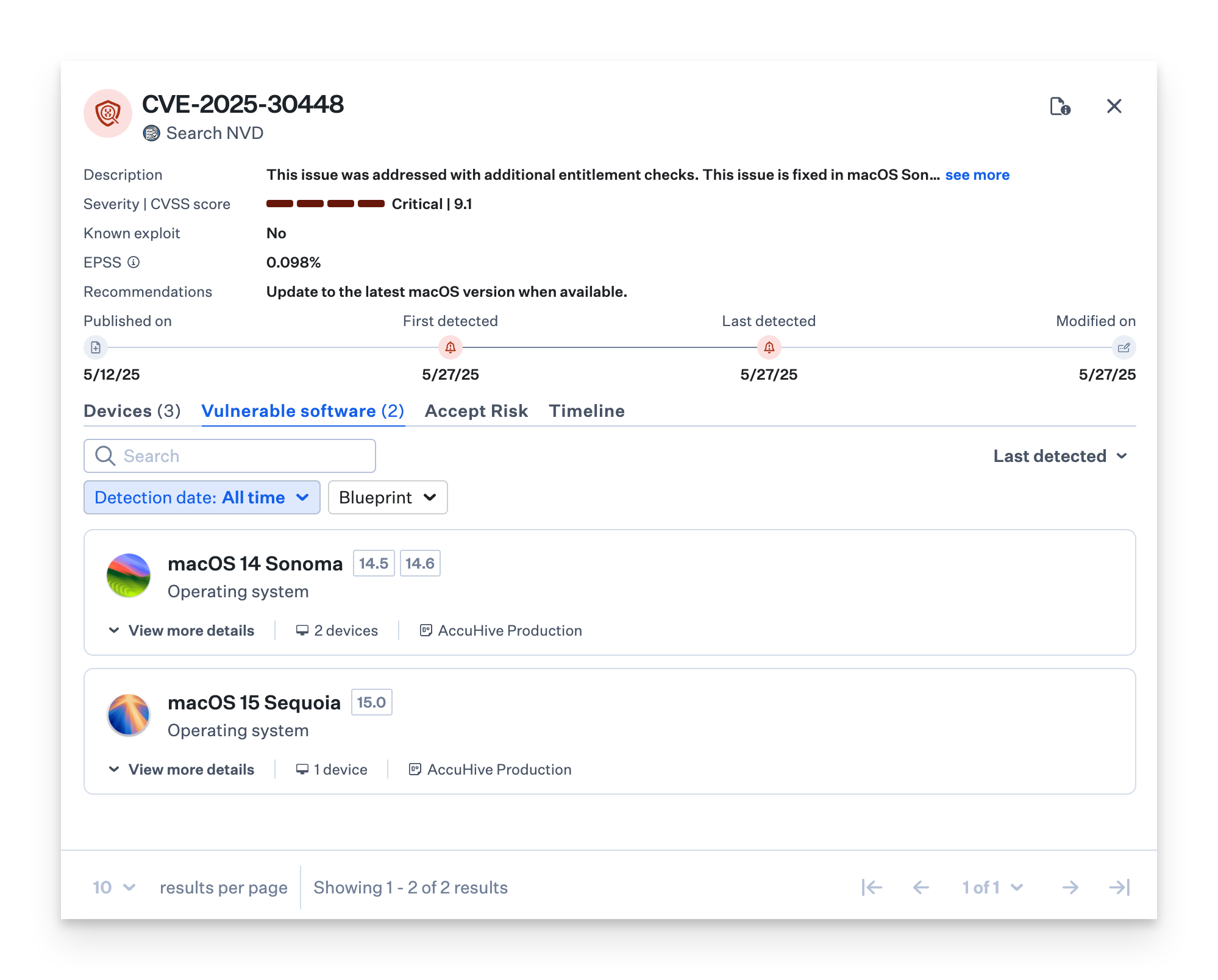
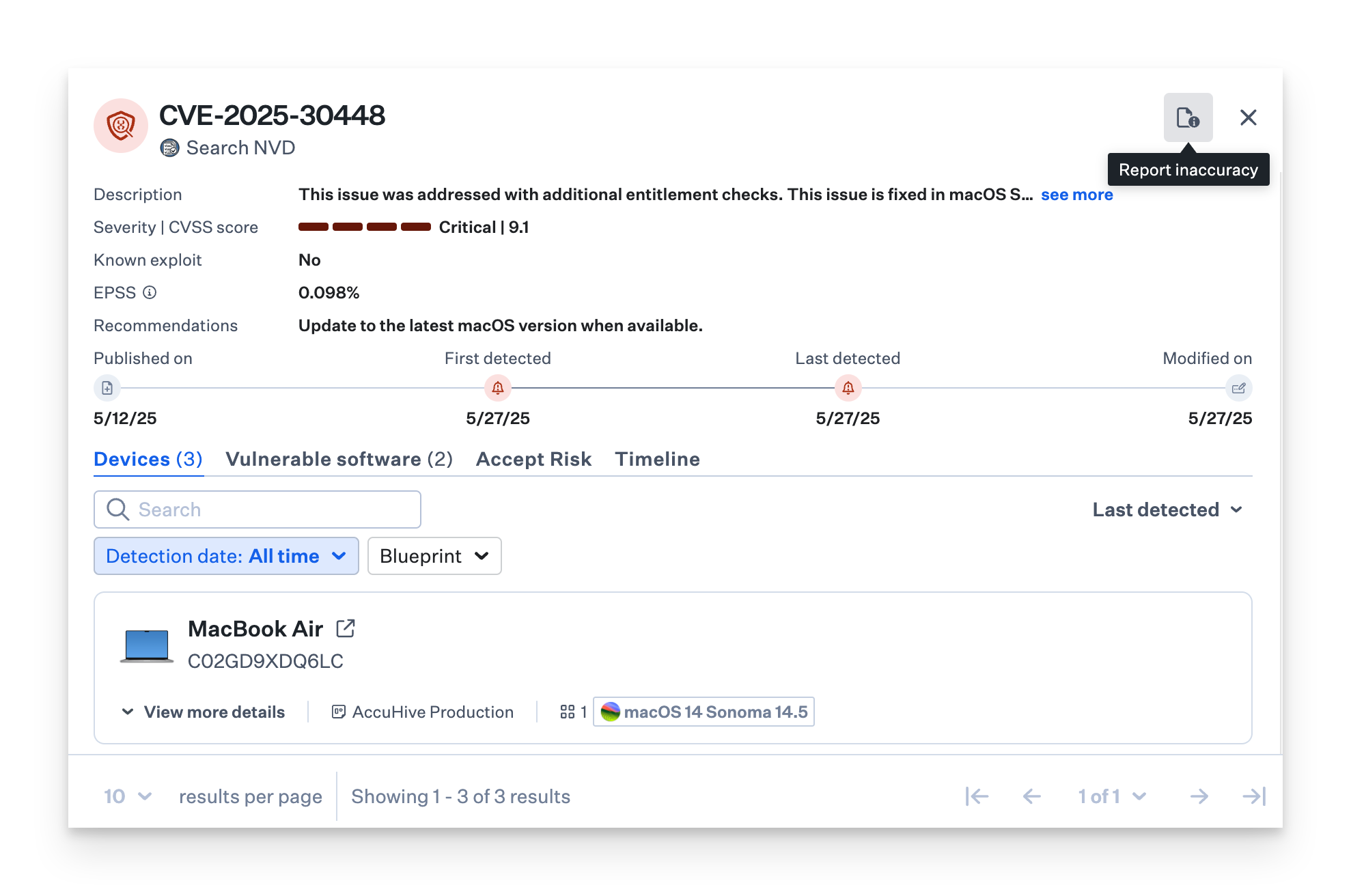
CVE Information
When you select a CVE, a detailed drawer will appear, giving you an in-depth look at:
The vulnerability's description
Impacted applications
Severity level
Known exploit (whether it has been exploited in the wild)
EPSS (probability of being exploited in the 30 days)
Links to official CVE reports for more information
This information helps you understand the scope of the threat and its potential impact on your devices.
Vulnerable Software
The vulnerable software tab allows you to view all the application and macOS versions affected by a particular vulnerability.
Devices view
Use the devices tab to view the devices affected by the vulnerability. Filter by Blueprint.
CVSS Score
The Common Vulnerability Scoring System (CVSS) is a method for calculating a qualitative measure of severity. Kandji Vulnerability Management utilizes the CVSS score to prioritize vulnerabilities and measure the severity of the vulnerability.
The National Institute of Standards and Technology (NIST) maintains the National Vulnerability Database (NVD), which provides CVSS enrichment for all published CVE records.
KEV Score
The Cybersecurity Infrastructure Security Agency (CISA) maintains the authoritative source of vulnerabilities that have been exploited in the wild. Kandji Vulnerability Management utilizes the Known Exploited Vulnerabilities (KEV) catalog to prioritize vulnerabilities.
Vulnerable Software View
In the Vulnerable software view, you can see all the software affected by a particular CVE. This allows you to focus your remediation efforts on the software that’s most at risk.
Report Inaccuracy
If there are any issues with a detected CVE, click the Report Inaccuracy button.
Select an issue from the drop-down menu.
Optionally, enter a description of the issue.
Click the Report button to complete the report.
.png)
Application Directories
Vulnerability Management scans the following directories for Applications (.app files only):
/Applications/Library/Users
Update Frequency
Device App Inventory: Every 15 minutes
App Vulnerability Matching: Hourly
Vulnerability CVE Database: Hourly
Devices View
The Devices View shows you which devices are impacted by the CVE. You can filter this view by Blueprint, which makes it easier to pinpoint affected devices within specific configurations or groups.
Device Details
For each affected device, you’ll see additional details to help you take action, including:
Threat ID: The unique SHA-256 hash of the detected threat
Process: The most recent process associated with the threat
Classification: The type of threat (e.g., malware, phishing)
Detection Date: When the threat was first identified
Devices: The number of impacted Mac devices
Threat Status: The current state of the threat—whether it’s quarantined, resolved, or still active
You can click the Open Device Record button for the full details.
Click the disclosure triangle to View more details.
You can view and copy the path of the application, as well as view version information.