Lock Device
The Lock Device command is available on macOS, iOS, iPadOS, and visionOS. It does not require supervision.
A locked device cannot recieve an Erase Device MDM command. For more information on erasing a device, see our Erase a Device support article.
How to Lock a Mac
Navigate to the Device Record.
Open the Device Action Menu.
Select Lock Device.
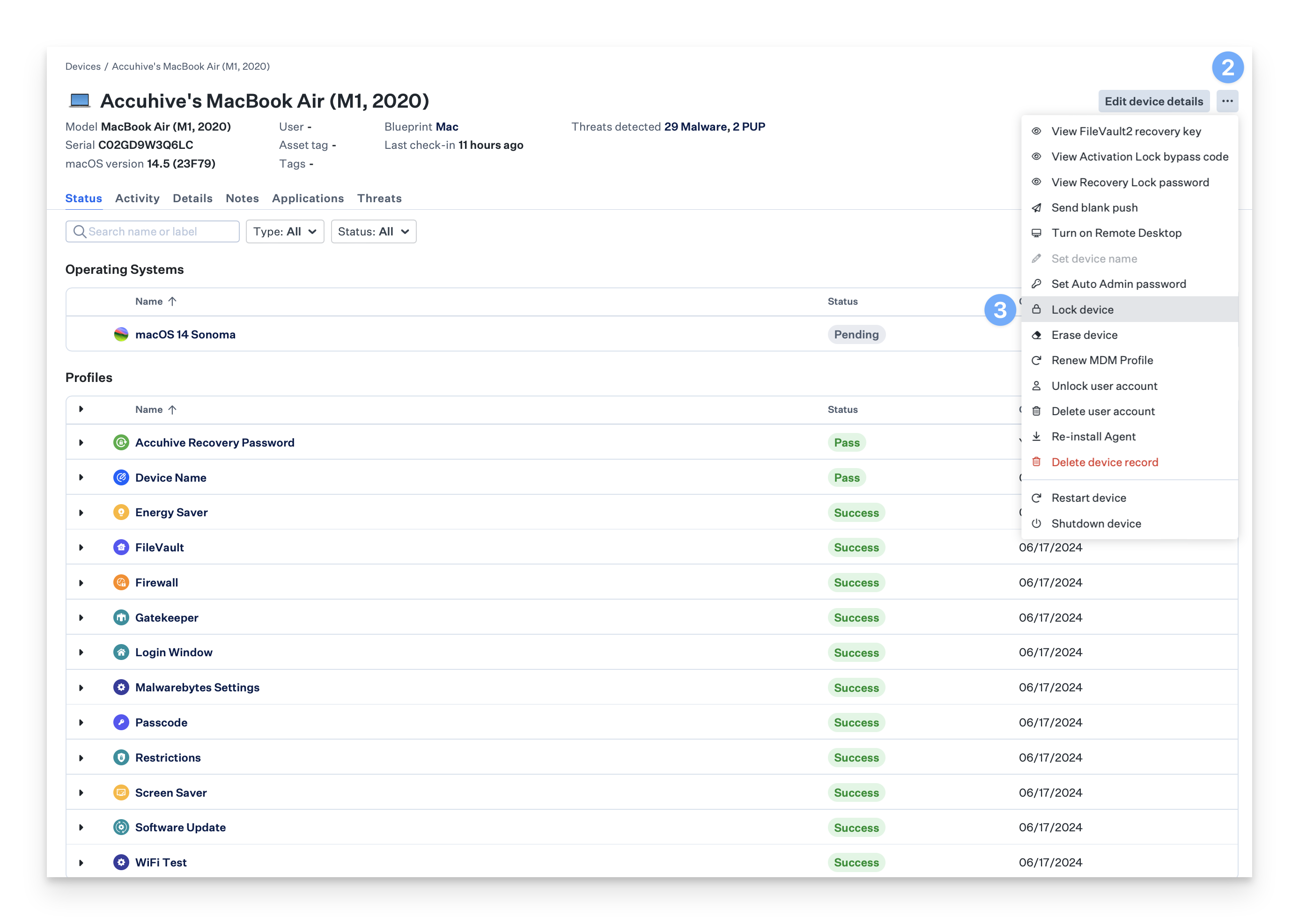
Optionally, configure a Lock message (macOS 14 or higher).
Click Lock device.
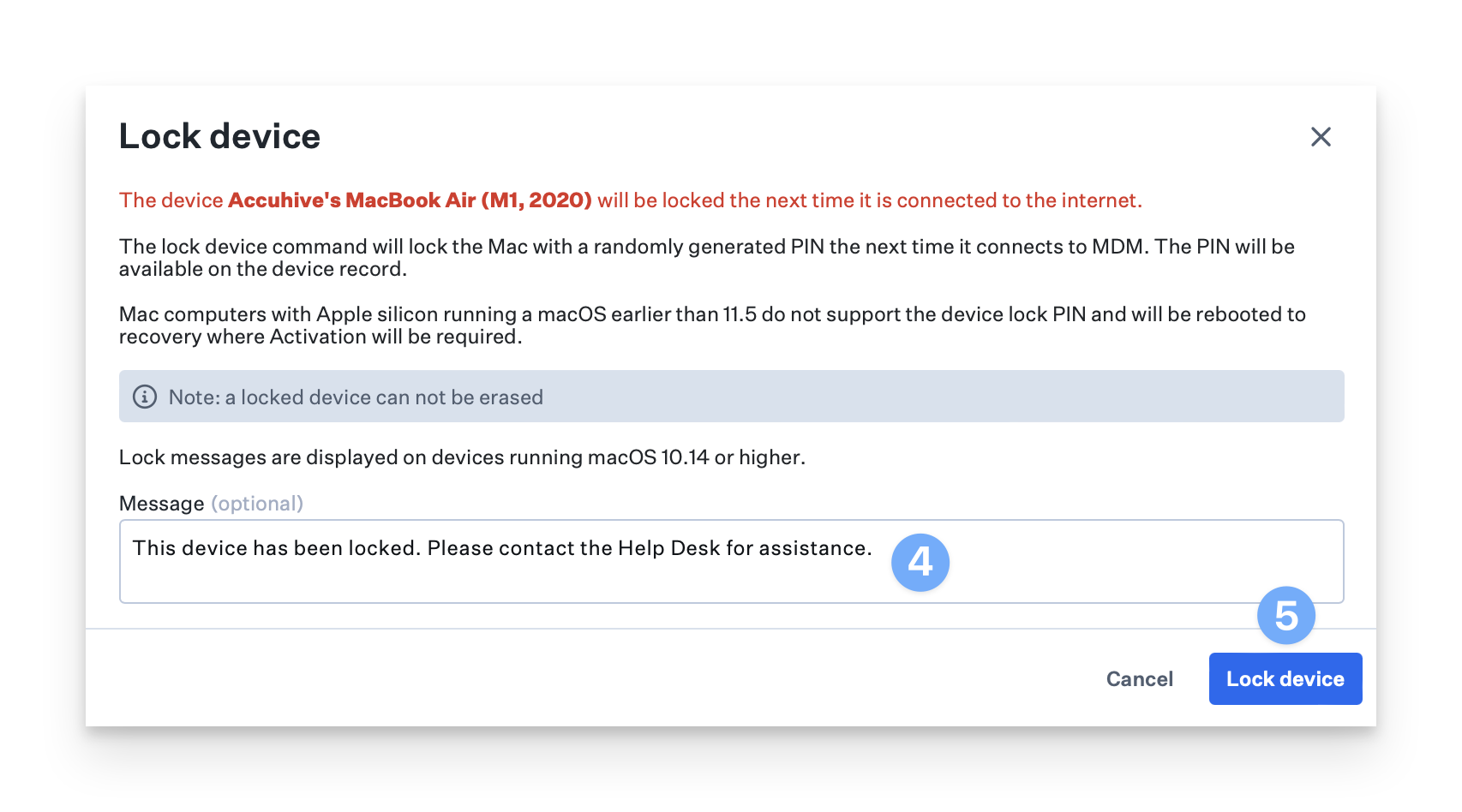
How to Lock an iPhone or iPad
Navigate to the Device Record.
Open the Device Action Menu.
Select Lock Device.

Optionally, configure a Lock message and Phone number to display on the locked device.
Click Lock device.
How to Lock a Vision device
Navigate to the Device Record.
Open the Device Action Menu.
Select Lock Device.
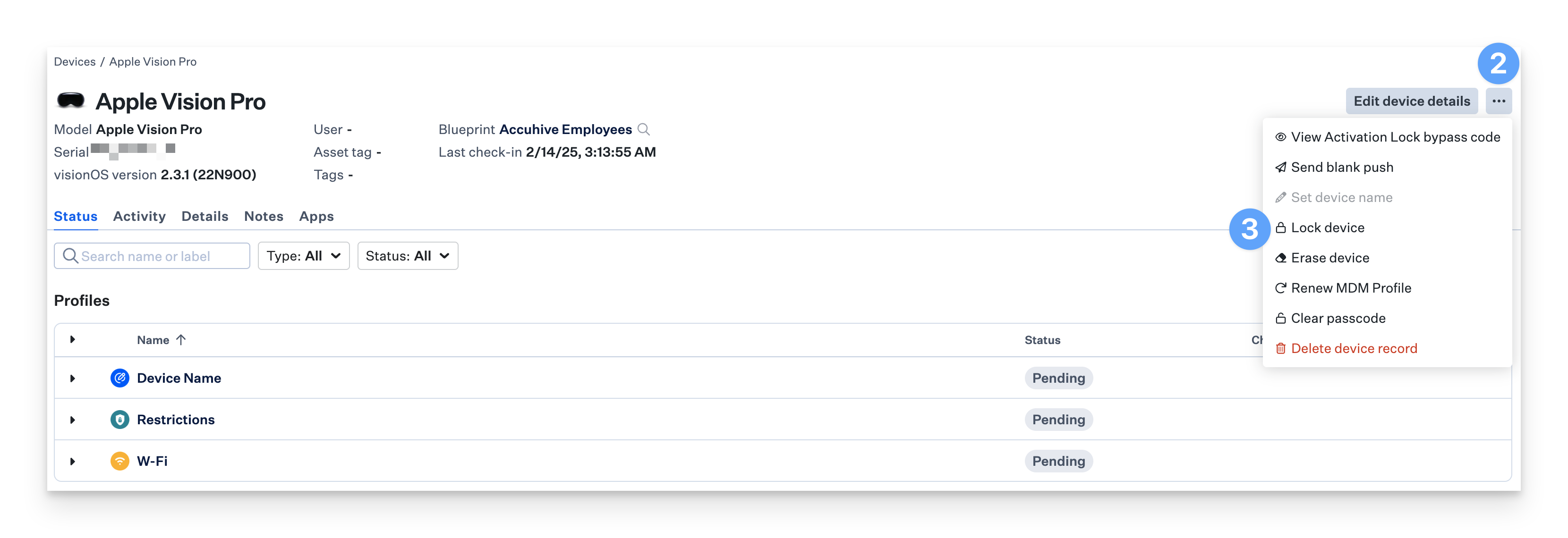
Click Lock device.
Command Behavior for macOS
For macOS devices, the device will be locked with an EFI/Find My PIN code. Some conditionals, whose behavior is unique to the hardware and macOS version, are outlined below. Once the device receives the command, a 6-digit pin will automatically be generated and available on the device record.
Mac computers with Apple silicon running macOS 11.5 or earlier.
Lock device PINs are not supported on Mac computers with Apple silicon before macOS 11.5.
The device will restart to recoveryOS, where an admin must authenticate, and activation will be required.
Mac computers with Apple silicon running macOS 11.5 or later.
The device will restart and be locked with a randomly generated PIN once the device receives the command.
Mac computers with Intel running any supported macOS version.
The device will restart and be locked with a randomly generated PIN once the device receives the command.
Command Behavior for iOS, iPadOS, and visionOS
For iOS, iPadOS, and visionOS devices, once the command is received, the screen will automatically be locked, and you can optionally specify a lock message. The device will be locked with the existing passcode.