If you experience any issues with Passport & Okta, read through our Passport Troubleshooting with Okta article for more information.
Okta Application Configuration
When configuring the Passport Library Item, you need the Client ID (Application ID) and Identity provider URL. Use these steps to configure the OIDC app and collect the required information.
In your Okta Administrator Console, in the left menu pane, expand the Applications section and select Applications.
Click Create App Integration.
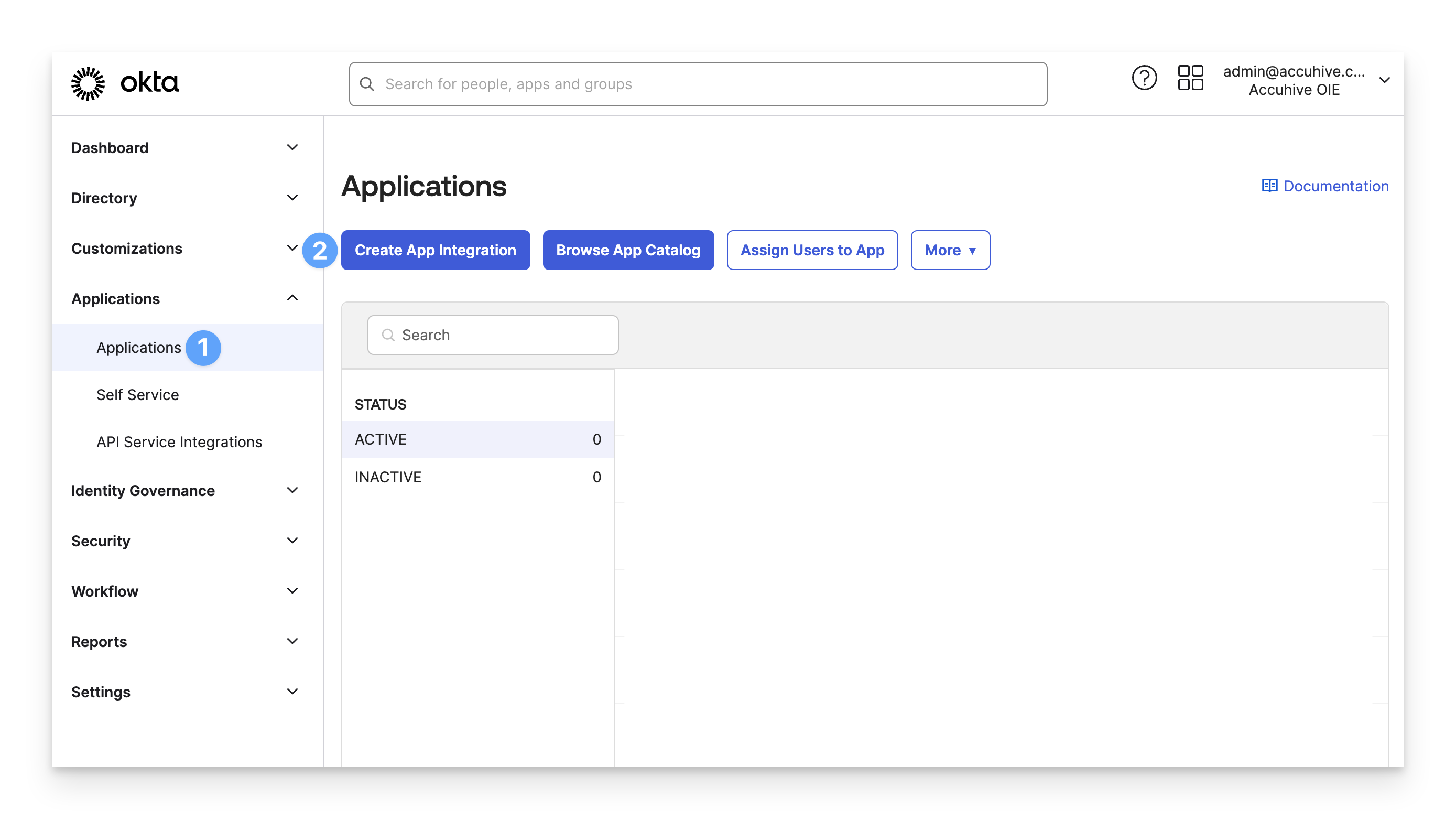
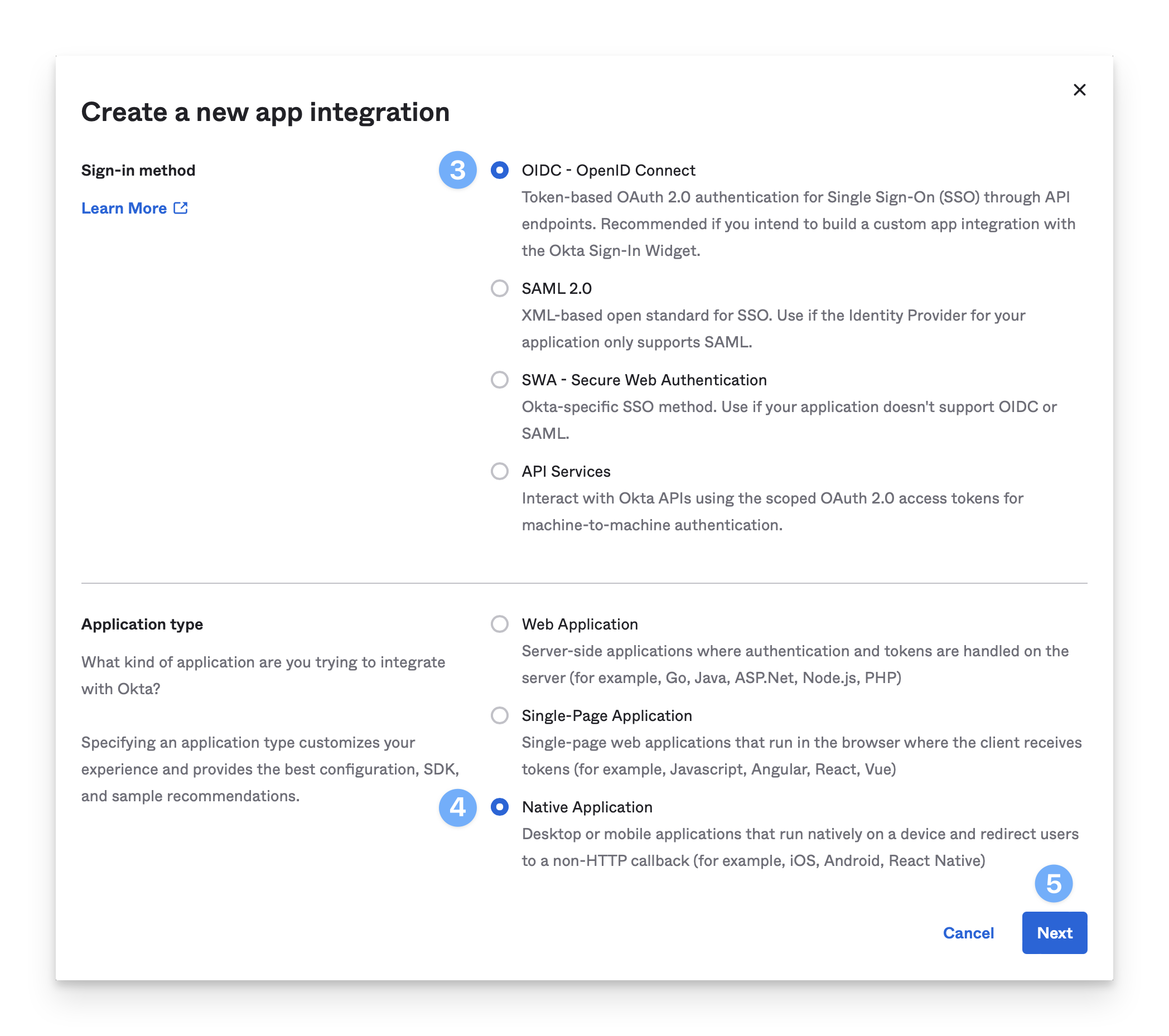
For Sign-in method, select OIDC - OpenID Connect.
For Application Type, select Native Application.
Click Next.
In the App integration name field, enter a name such as Kandji Passport.
In the Grant type section, confirm that the checkbox for Refresh Token is deselected. This option must be turned off to ensure that Passport prompts users to update their Mac password while logged in if their Okta password changes.
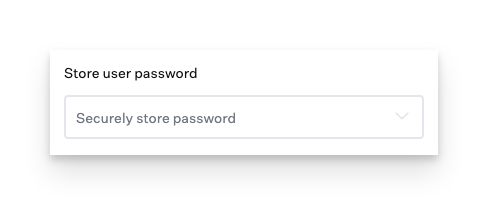
The Store user password setting in the Passport Library Item needs to be set to Securely store password for users to receive the password update prompt.
If you’re using Okta Identity Engine, click Advanced to show additional options.
In the Other grants section, select the checkbox for Resource Owner Password.
Note: If your Okta instance hasn’t yet been updated from Classic to Okta Identity Engine (OIE), the Interaction Code grant type and other options, will not be displayed.
.png)
In the Sign-in redirect URIs section, click Add URI.
In the new field that appears, enter the following:
https://localhost.redirect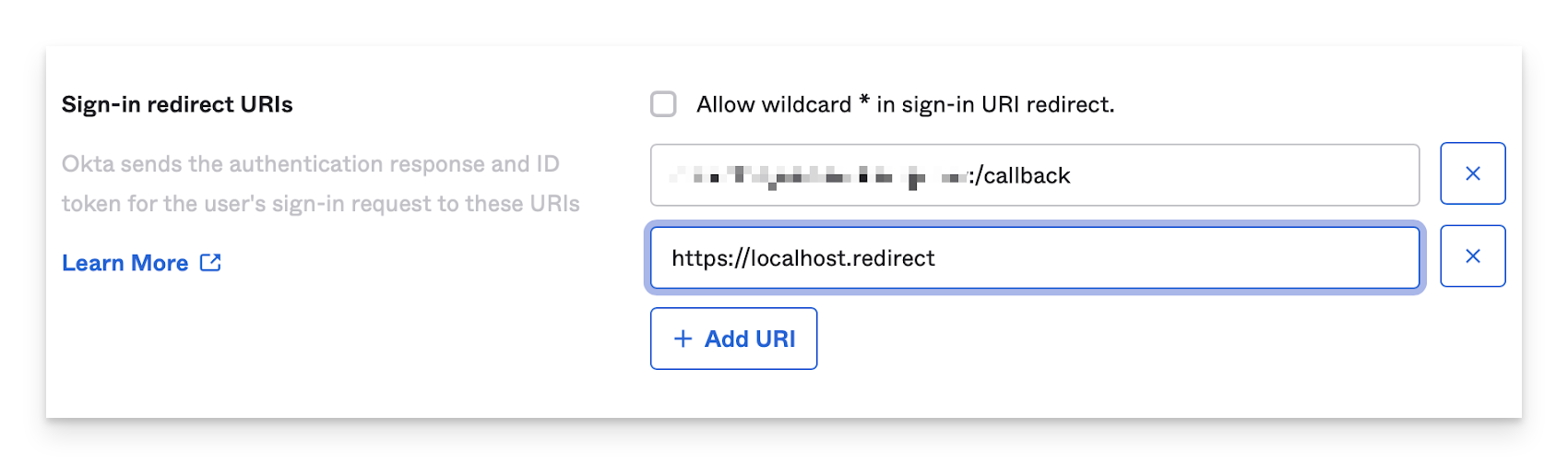
The same Sign-in redirect URI must be used in the Passport Library Item in the Redirect URI field in the Authentication mode section.
In the Assignments section, select whether to assign the app integration to everyone in your org, only selected group(s), or skip assignment until after app creation.
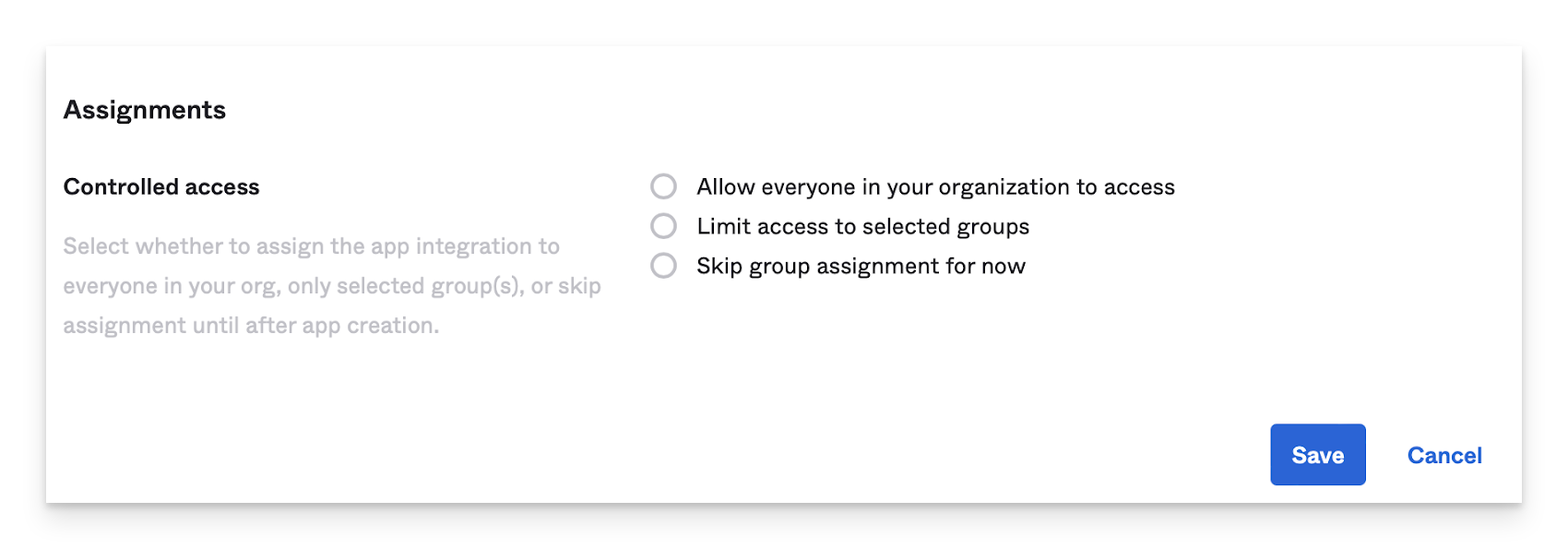
Click Save.
Open a secure text document that you can use to store values for this OIDC app. You will need these details when you configure the Passport Library Item.
In the General tab of the OIDC application you just created, on the right side of the Client ID field, click the copy icon (looks like a clipboard).
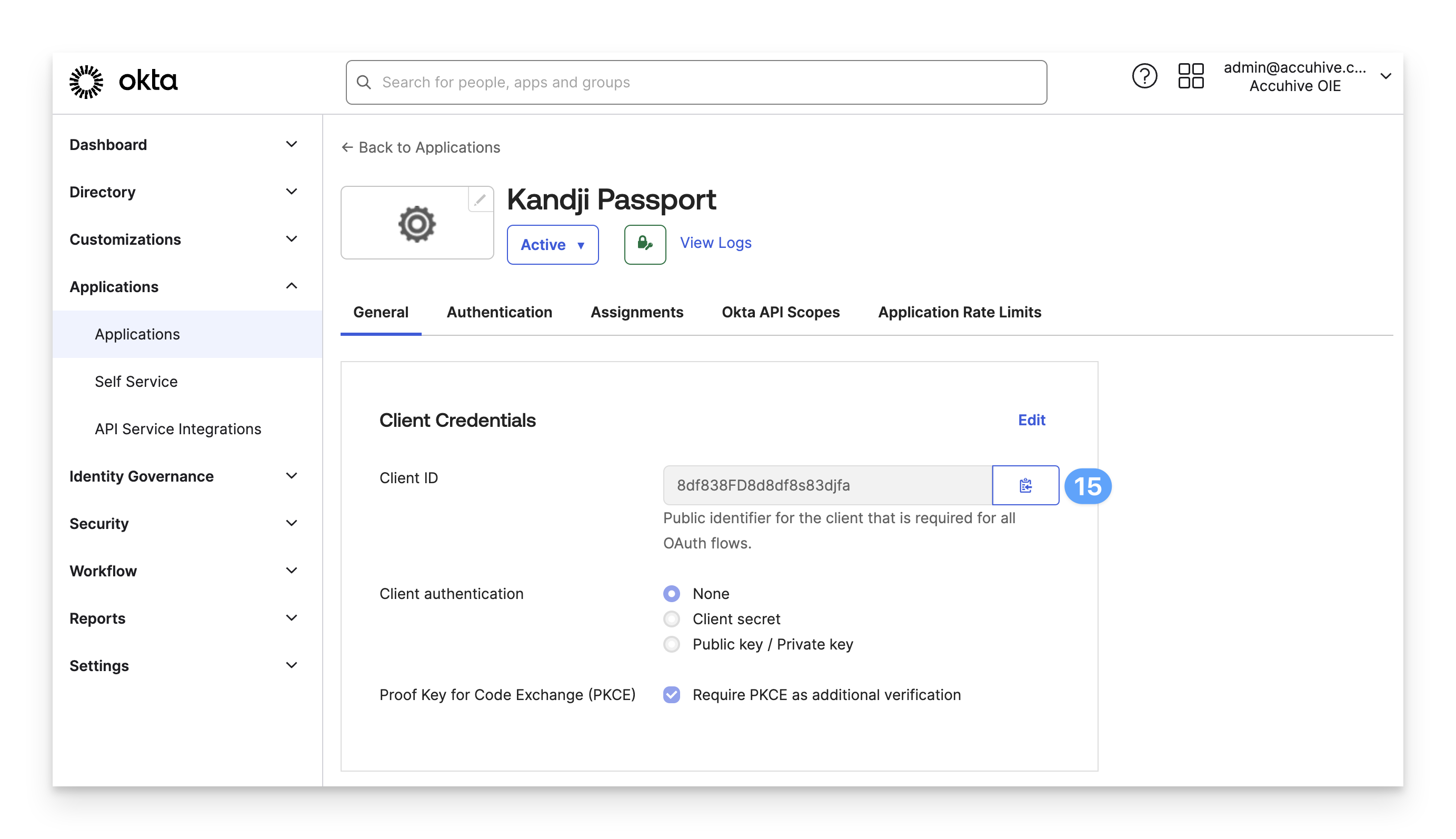
Paste the value into your secure text document.
Copy the formula for your Identity provider URL from the following text:
https://yourOktaDomain/.well-known/openid-configurationPaste the text into your secure text document.
In your secure text document, replace yourOktaDomain with your Okta domain.
You do not need a custom Sign-On Policy Rule, but if you add one, ensure MFA is disabled.
With the Okta configuration complete, assign the app to the users using Passport to sign in to their Mac systems, and go to the Kandji web app to configure the Passport library item.
Enable Multi-factor Authentication (MFA)
The MFA policy in Okta should be applied to Users or Groups, not to the Passport Application in Okta.
When using MFA with Passport, a few settings need to be modified in Okta, and in the Passport Library Item in your Kandji web app. Below are MFA instructions for Okta Identity Engine (OIE) and Classic Engine.
Okta Identity Engine
Okta Authenticators
Expand the Security section from the lefthand navigation.
Click Authenticators.
Ensure that at least one multifactor authentication method, such as Okta Verify, is listed.
If no multifactor method is listed, click the Add authenticator button.
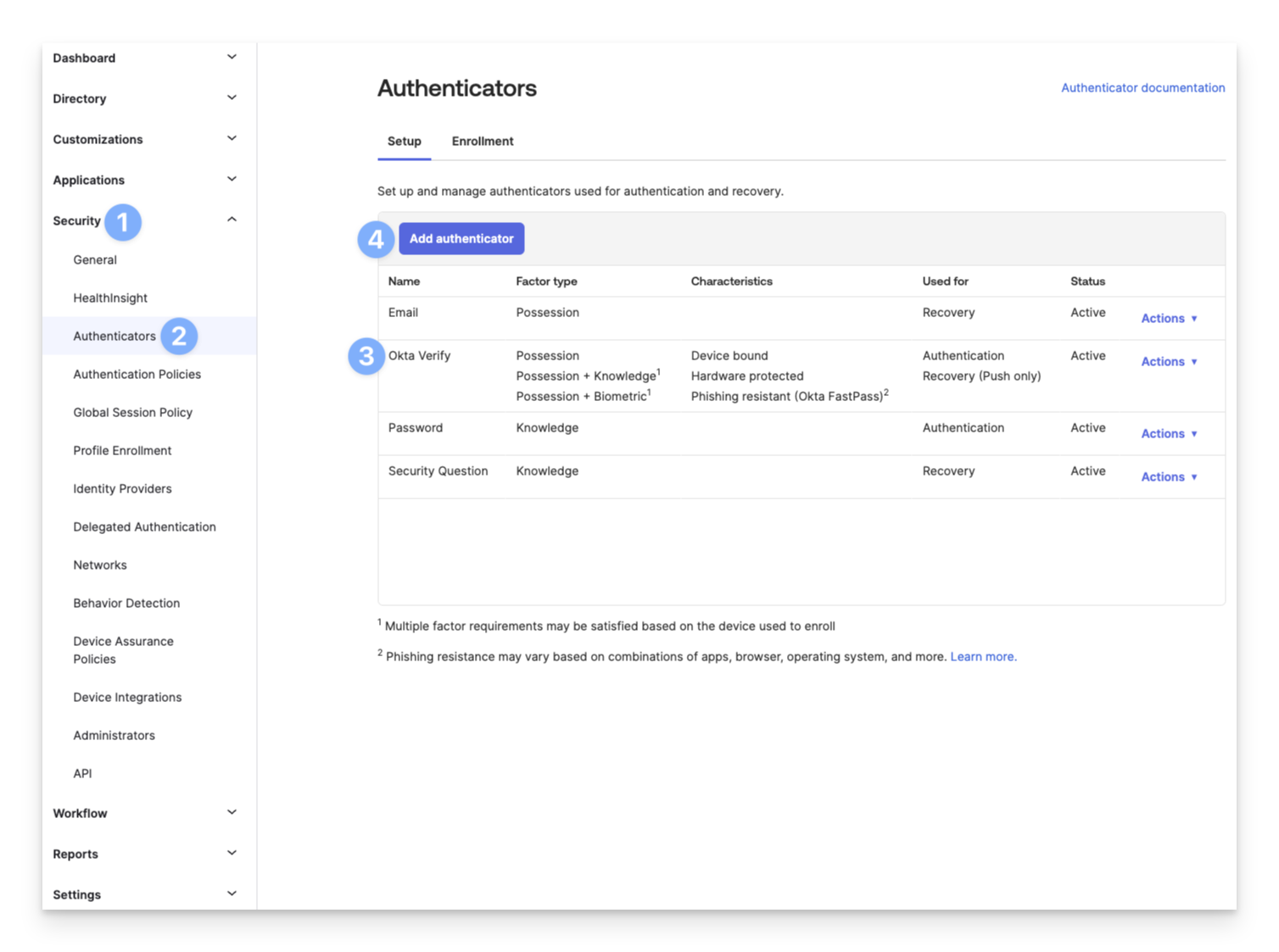
Click the Add button below the authenticator(s) that are needed.
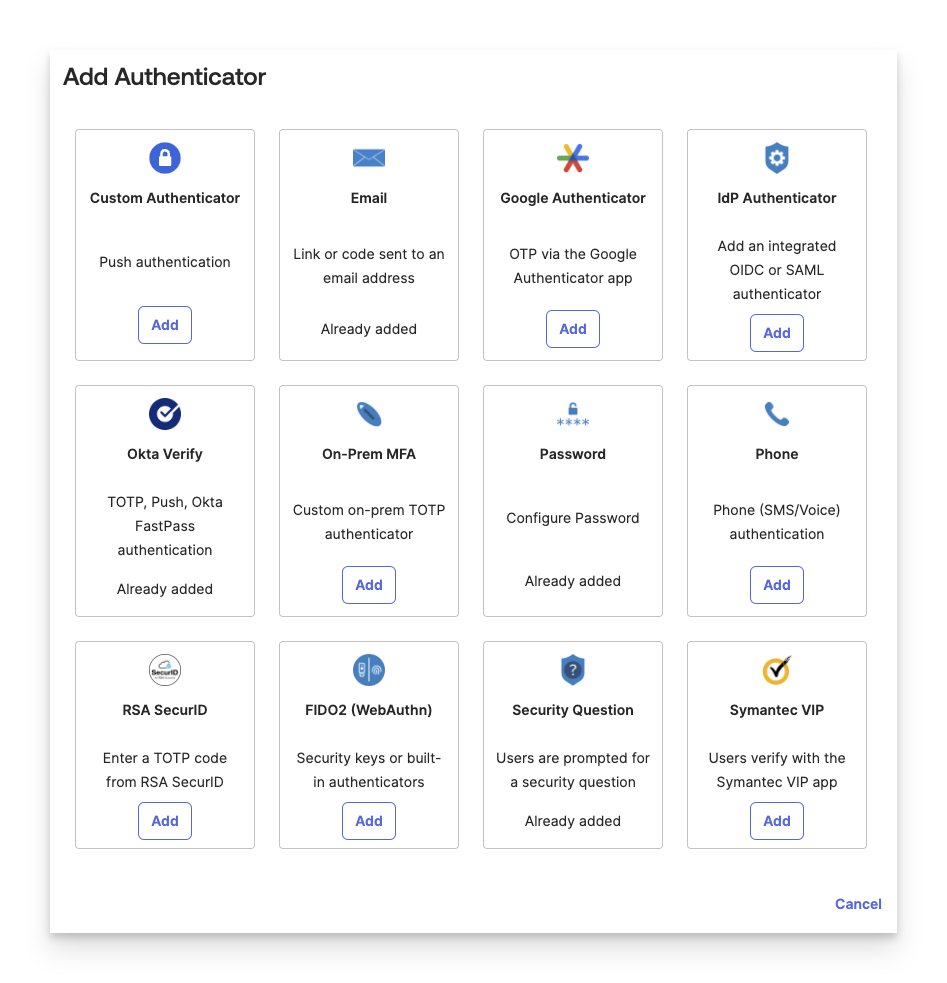
Complete any additional steps for the authenticator.
Click Add.
Okta Global Session Policy
Expand the Security section from the lefthand navigation.
Click Global Session Policy.
Click Add policy.
Or click the pencil to edit the existing Default Policy.
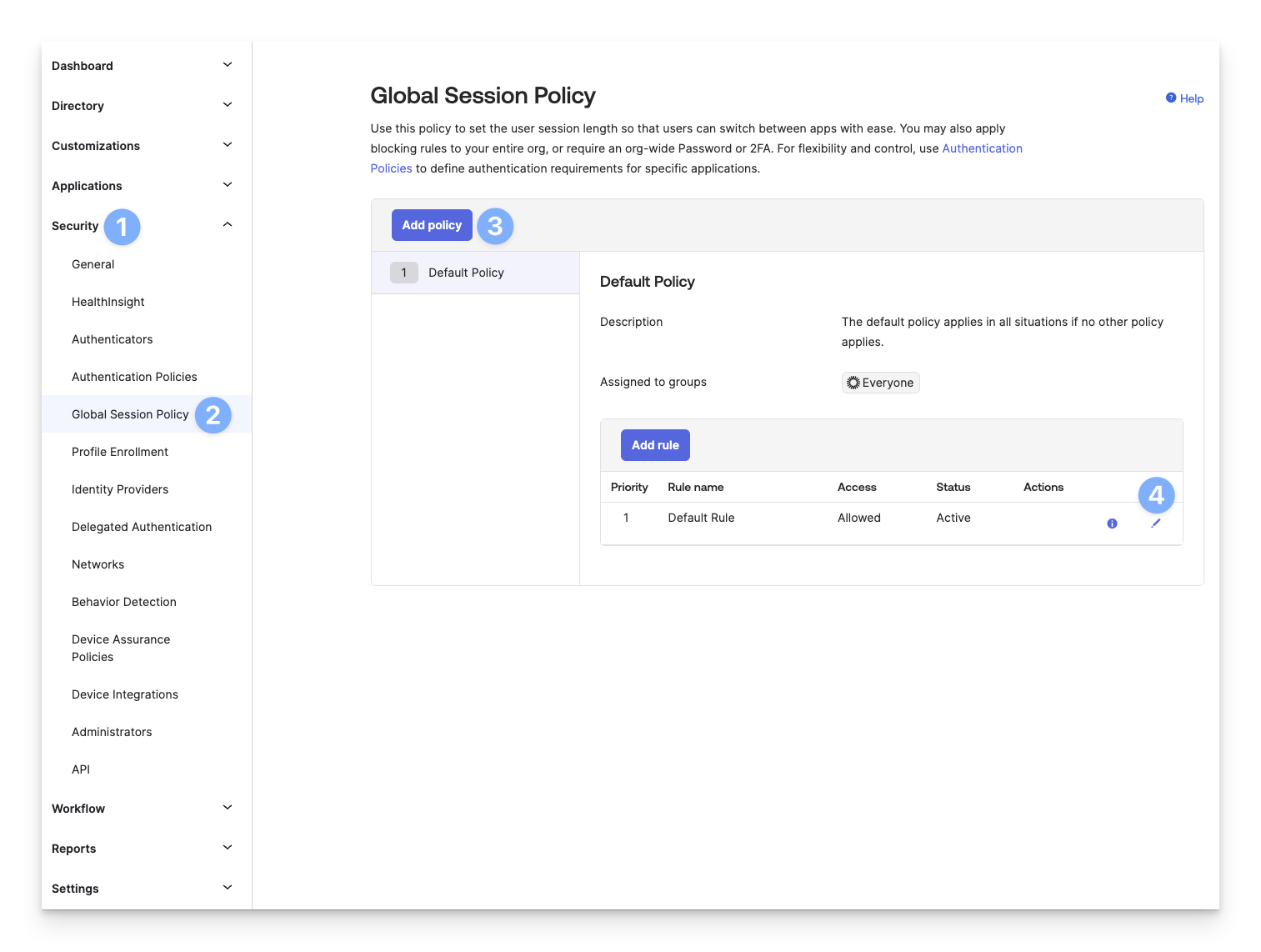
Set Multifactor authentication (MFA) is to Required.
Set Users will be prompted for MFA to At every sign in.
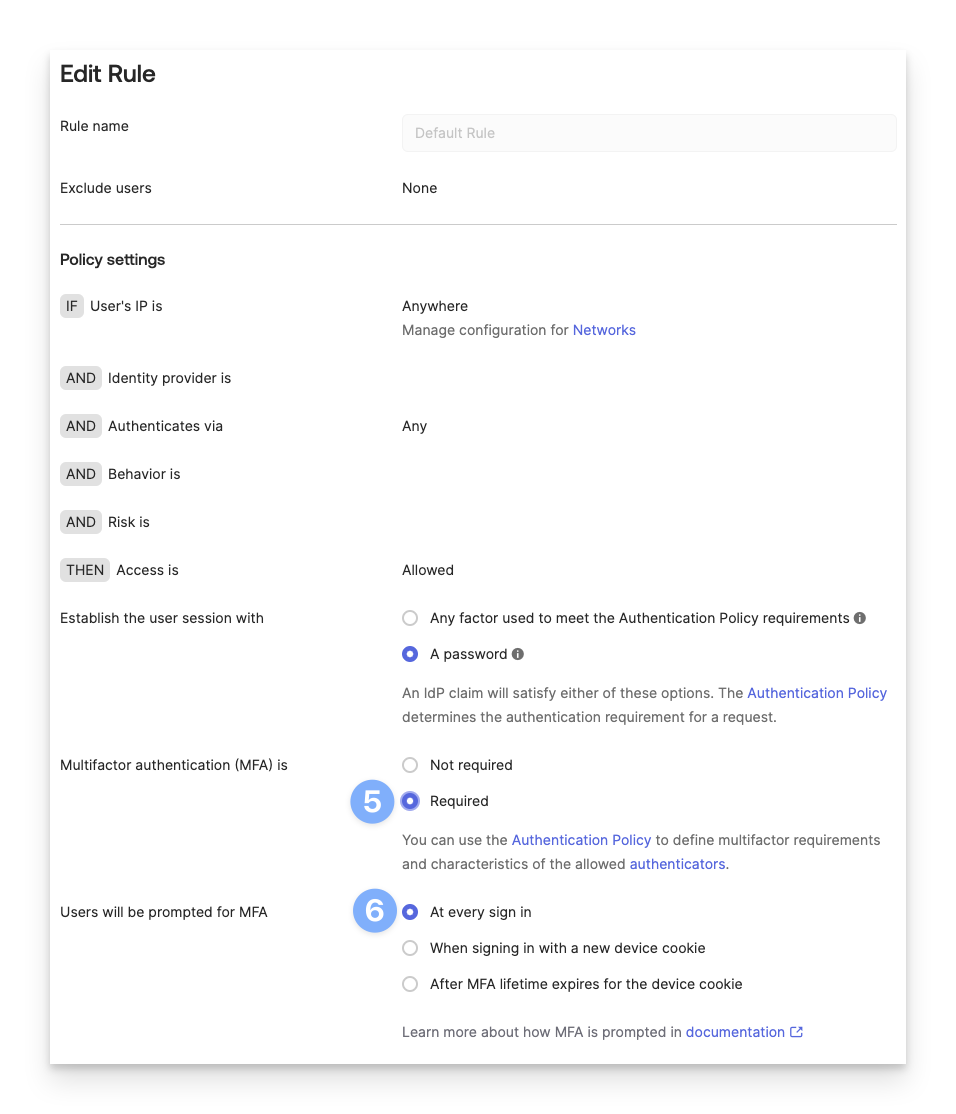
Scroll down and click Update rule or Create rule.
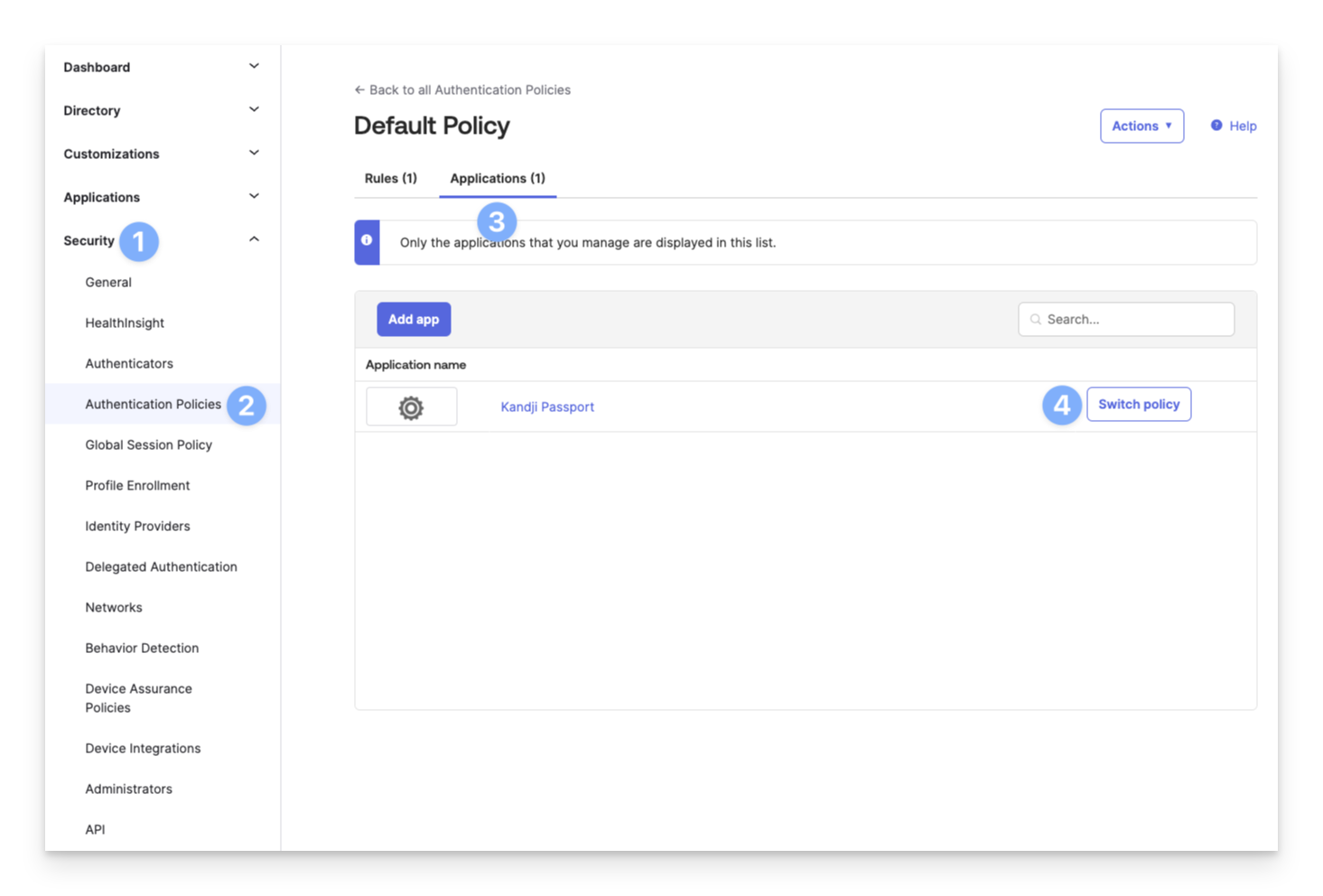
Authentication Policies
Expand the Security section from the lefthand navigation.
Click Authentication Policies.
Click Applications.
Click Switch policy next to your Kandji Passport application.
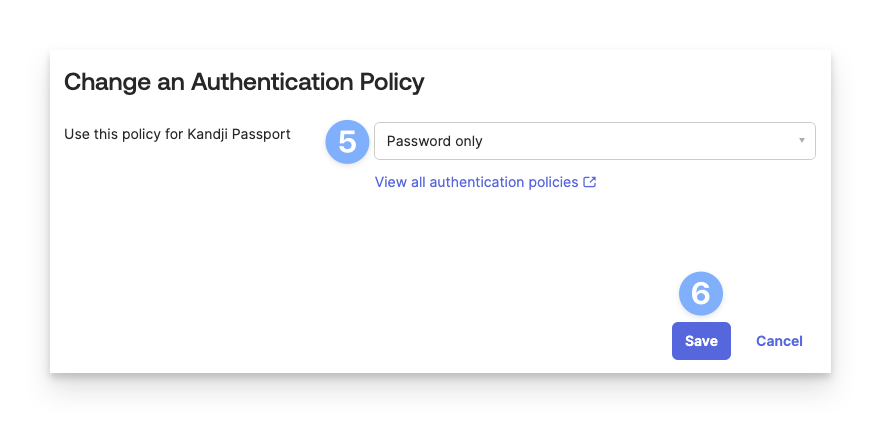
Select Password only for the Use this policy for Kandji Passport policy.
Click Save.
Classic Engine
Okta MFA Settings
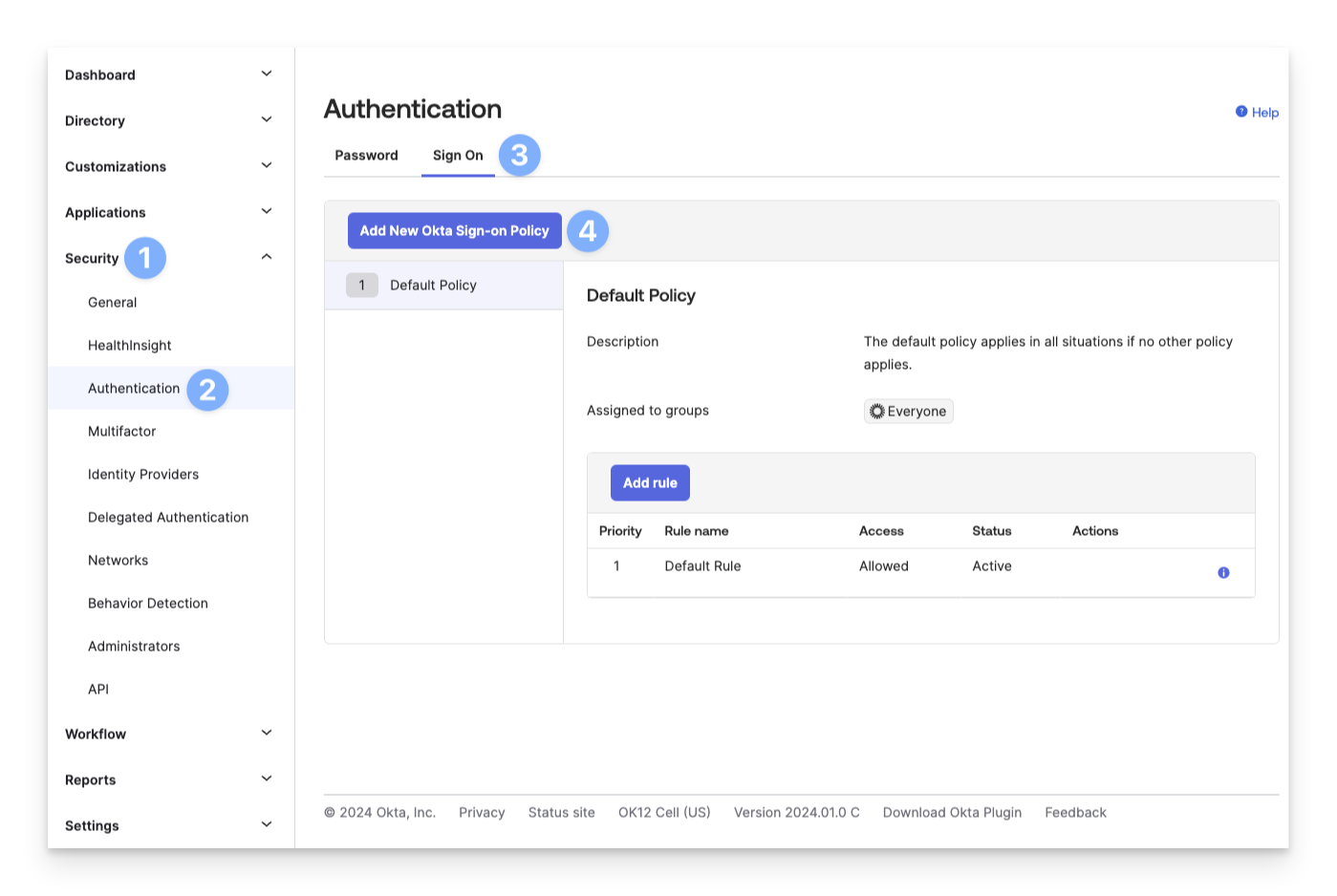
Expand the Security section from the lefthand navigation.
Click Authentication.
Click Sign On.
Click Add New Okta Sign-on Policy
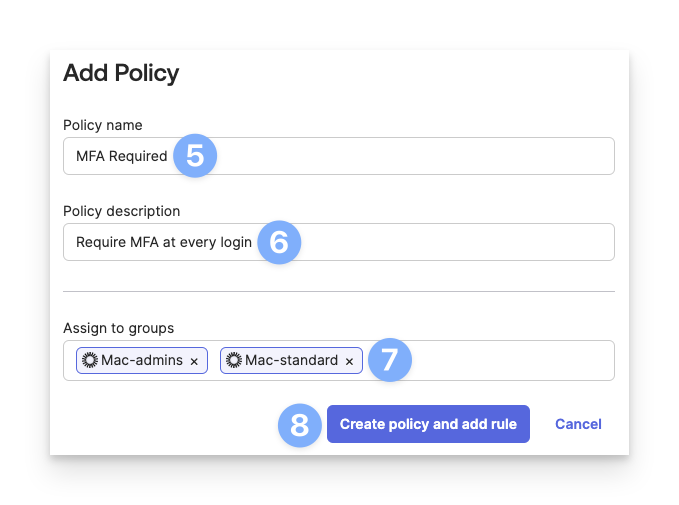
Enter a Policy name similar to MFA Required.
Enter a Policy Description.
Select the groups that will be assigned to this MFA requirement.
Click Create policy and add rule.
Enter the Rule name.
Select Required for the Multifactor authentication (MFA) is setting.
Select At every sign in for the Users will be prompted for MFA setting.
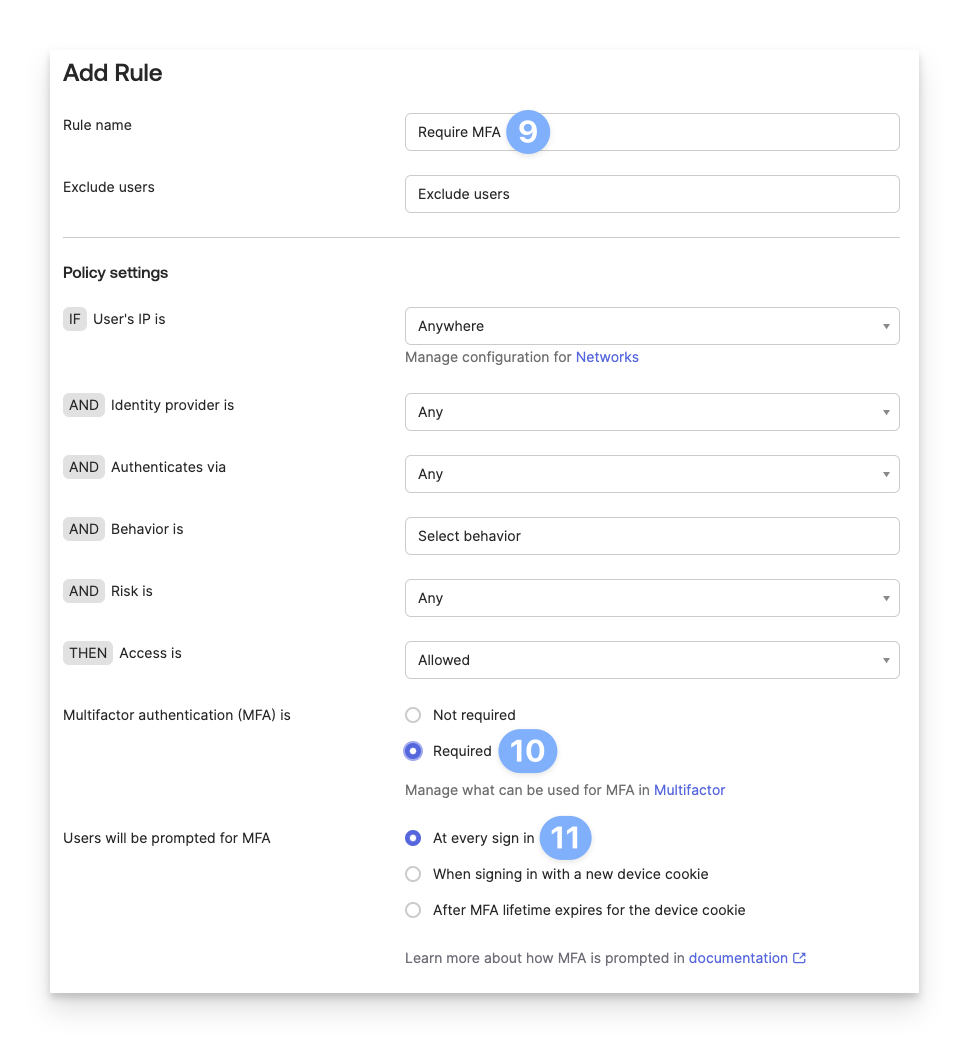
Click Create rule at the bottom of the window.
Library Item Settings
Select the radio button next to Web Login in order to support multi-factor authentication (MFA).
In the Redirect URI field, enter the following:
https://localhost.redirect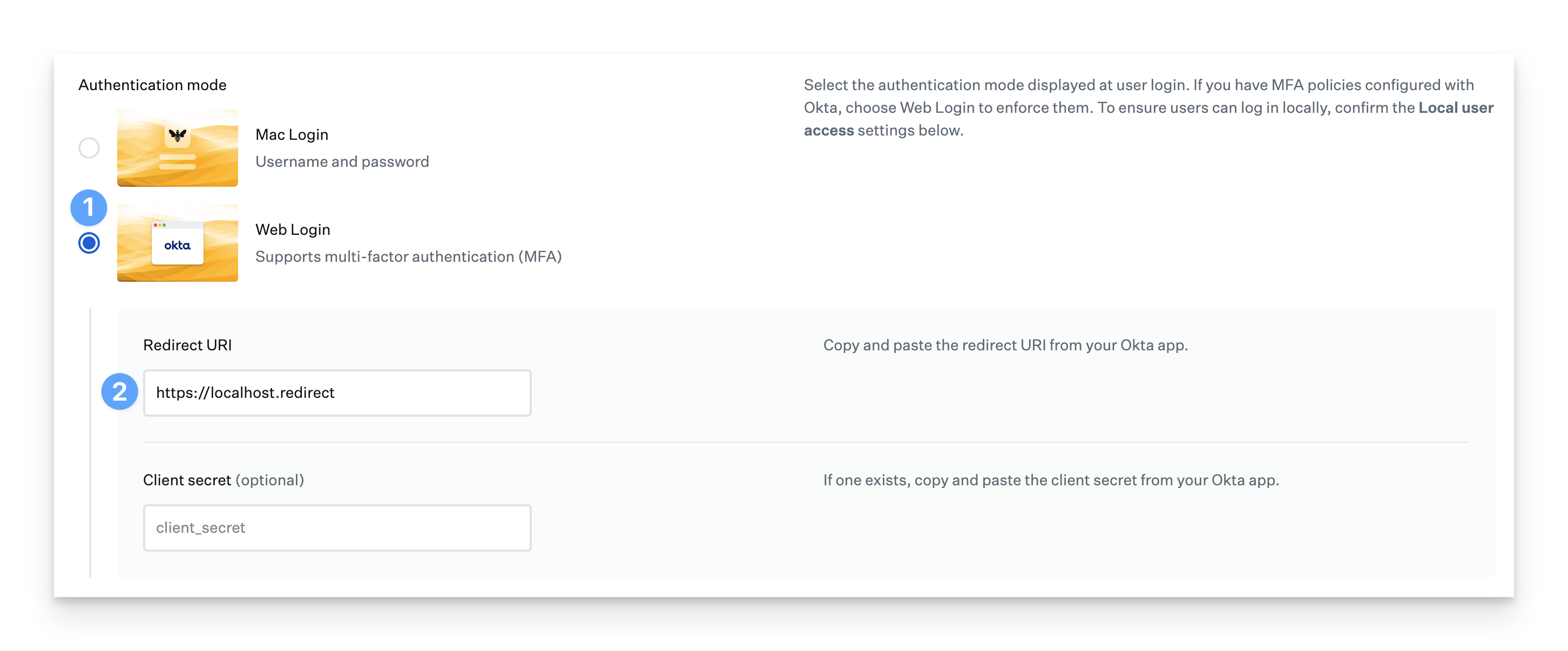
Click the Save button.
User Provisioning
Follow these steps if you plan to use the Group information in Okta to determine the user account type. The groups you use in Okta don't have to start with Mac- but these steps use Mac- as an example.
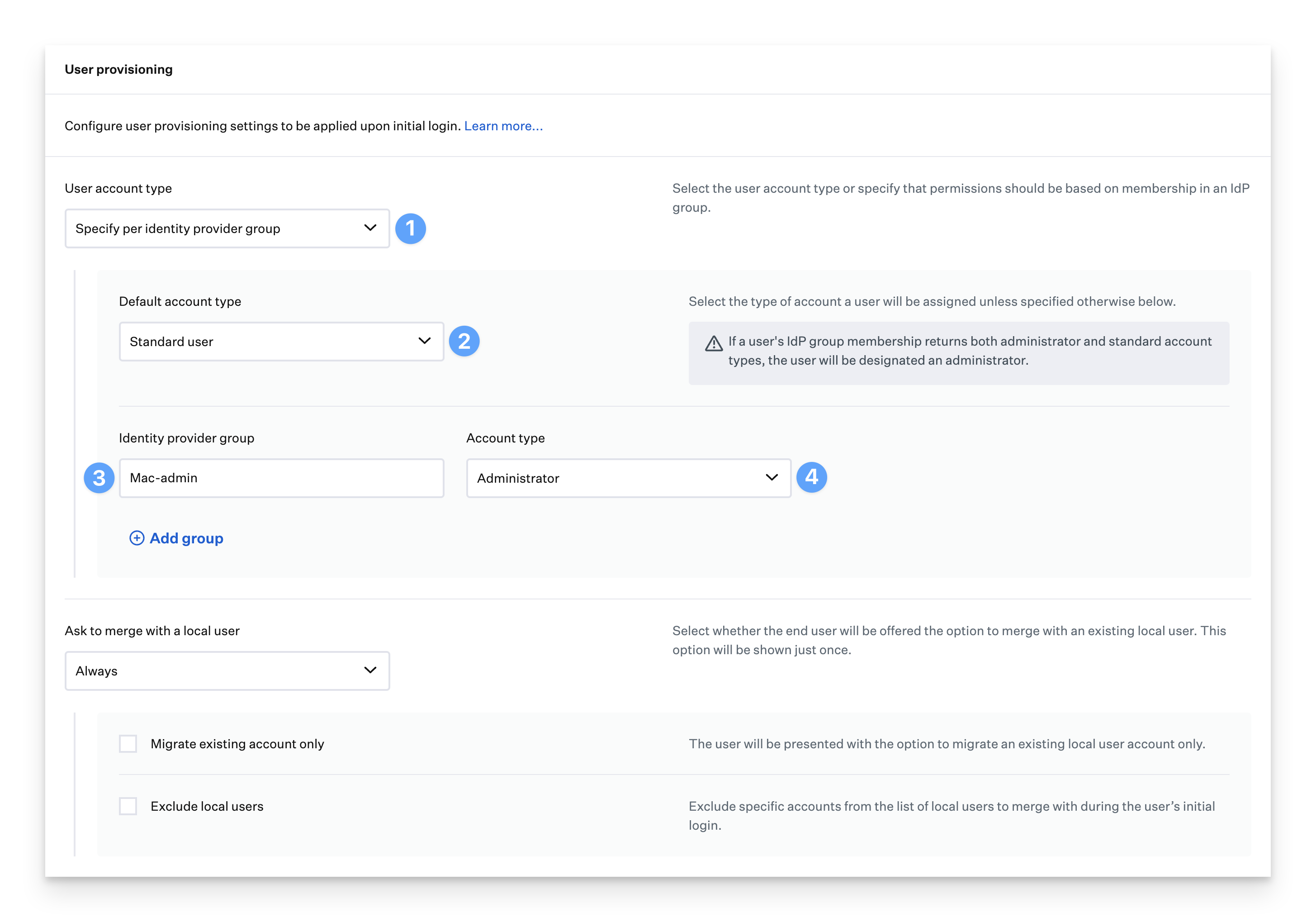
In the Passport Library Item, click the User account type menu in the User provisioning section and select Specified per identity provider group.
Select the Default account type from the drop-down.
In the Identity provider group fields, enter your Okta group names. This article uses groups that start with Mac- as an example.
For each Identity provider group row, set the Account type as appropriate.
Next, In Okta, in your Passport OIDC application, use the following steps to configure the Group claim filter to start with Mac- as an example.
In your Okta Administrator Console, in the left menu pane, expand the Applications section if necessary, then select Applications.
Select the Kandji Passport application that you previously created.
Click the Sign On tab.
In the OpenID Connect ID Token section, click Edit.
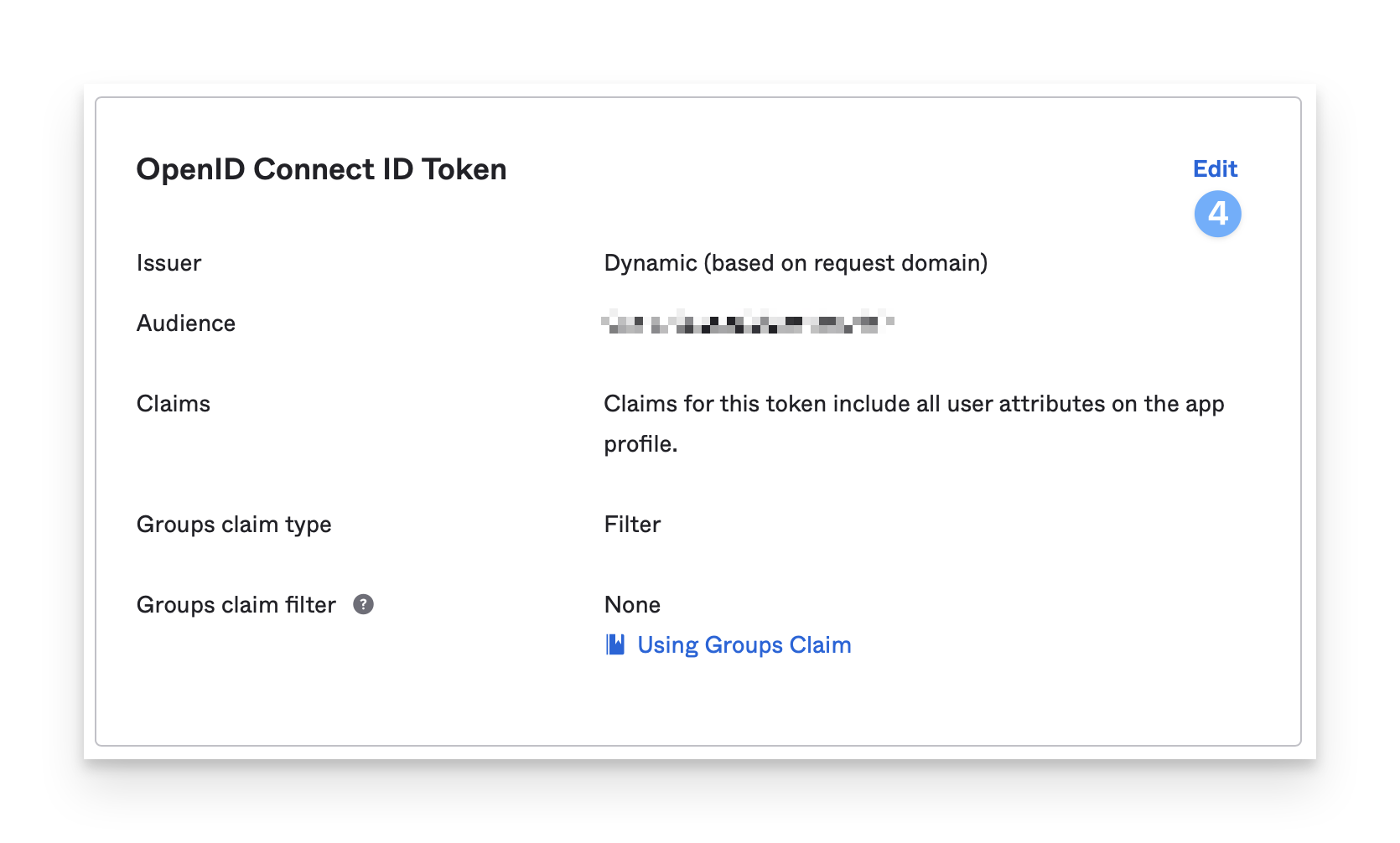
In the Groups claim filter section, leave the default value: groups.
Leave the middle field at the default: Starts with.
In the right-most field, enter Mac (assuming the Okta groups you use or will use start with Mac).
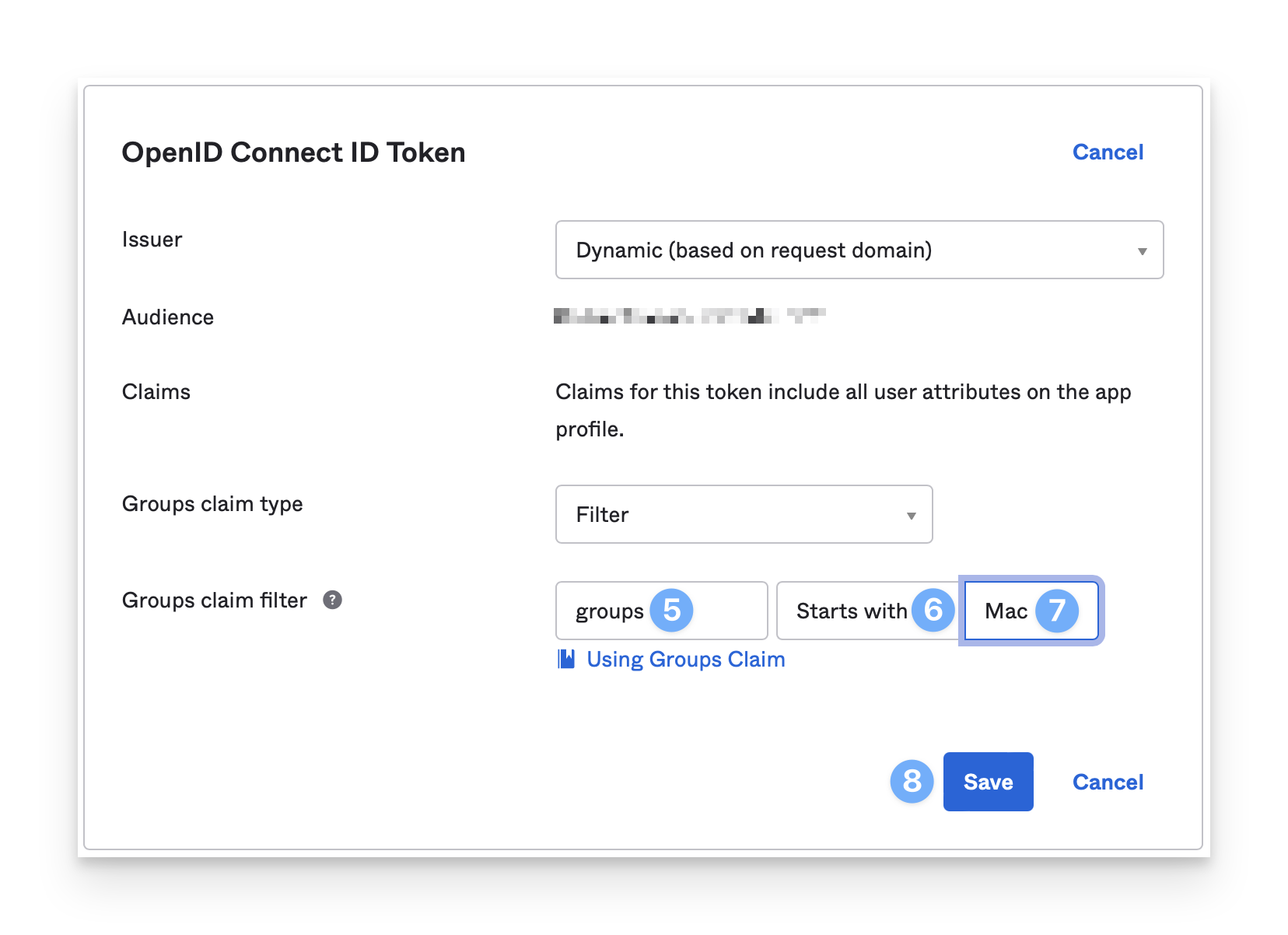
Click Save.
Troubleshooting Issues with Passport & Okta
If you experience any issues with Passport & Okta, read our Passport Troubleshooting with Okta article for additional information.