Occasionally, resolving Passport login issues might necessitate more in-depth troubleshooting. This guide will provide you with extra requirements, common errors, and advanced troubleshooting methods that can assist you when dealing with Passport.
Login Best Practices
Log in with the full email address - When logging in at the Passport Login Window, the full email address should always be used in the username field to ensure the authentication session is connected to the IdP and not local authentication. To avoid confusion when using email addresses at the FileVault Login Window, ensure the Managed user visibility box is unchecked on the Login Window Library Item. You can read more about this in our Passport Compatibility article.
Ensure your account has a familyName/surname in your IdP - The familyName attribute is required when using Passport to log in with IdP credentials. Ensure that even if you're using a service account, this field is populated in the User attributes within your identity provider.
Passport Supported IdPs
The current Kandji Passport supported IdPs are Google Workspace, Microsoft Entra, Okta, and OneLogin.
Passport Requirements when using Other IdPs
Passport configuration requires OIDC and ROPG workflows to function. Please check with your IdP to verify if they support these features.
While we do offer the option to choose Mac Login or Web Login, we recommend setting up Passport first using Mac Login as there can be additional factors when configuring Web Login. You can reference the supported configurations using Google Workspace, Microsoft Entra, Okta, or OneLogin as a resource.
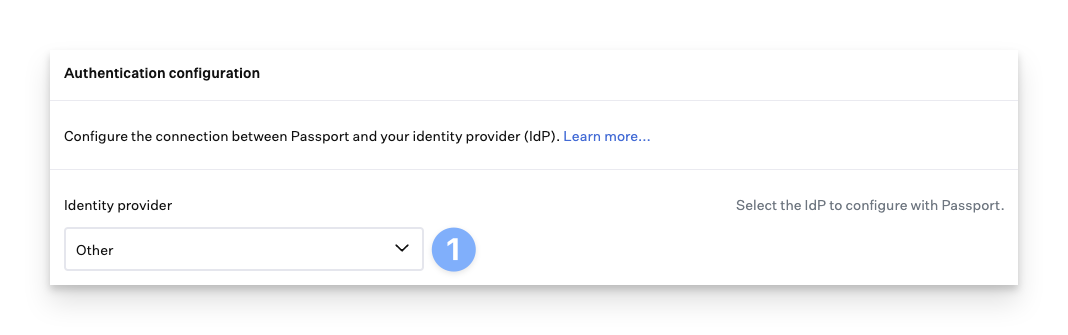
If you’re not using one of the identity providers above, you may still be able to configure Passport using the “Other “option.
Configure Other IdP
Authentication Configuration
When configuring an IdP other than Google Workspace, Microsoft Entra, Okta, or OneLogin, select the Other option from the Identity provider drop-down.
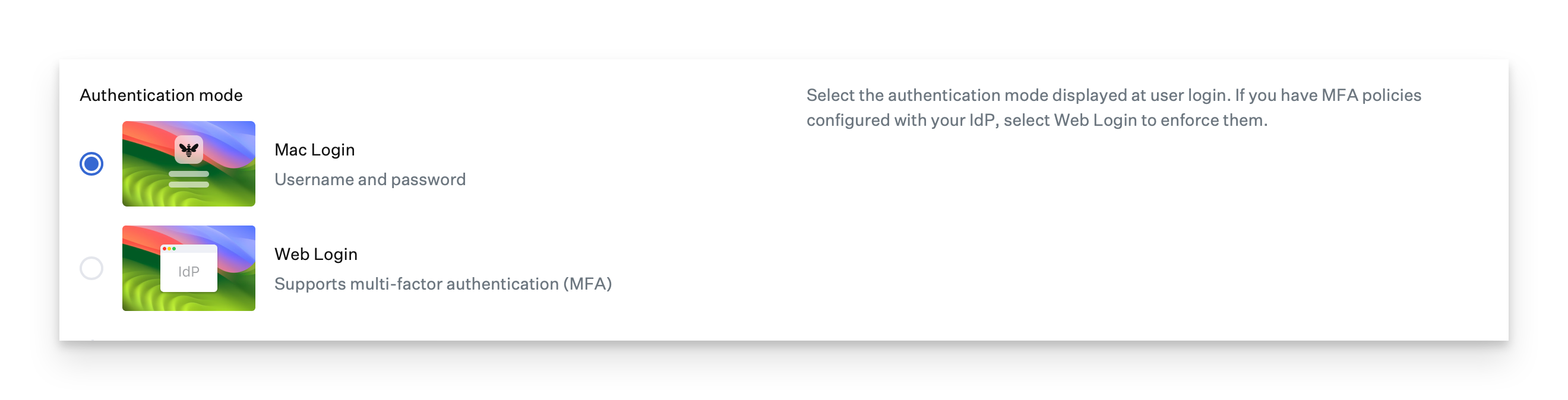
Authentication Mode
If you do not use multi-factor authentication (MFA), you need to choose Mac Login.
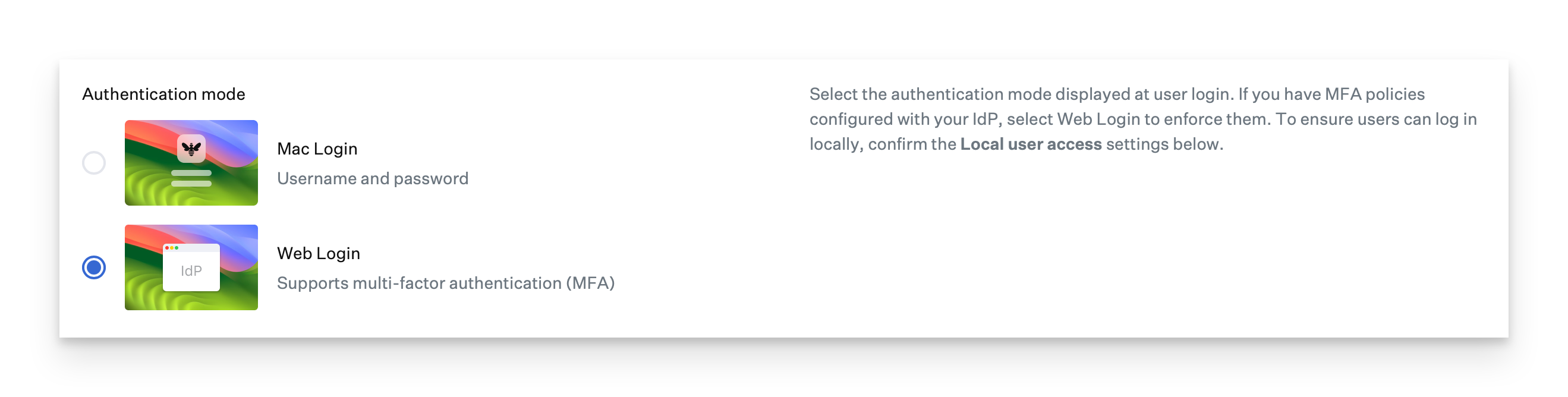
If you do use multi-factor authentication (MFA), you need to choose Web Login.
Mac Login
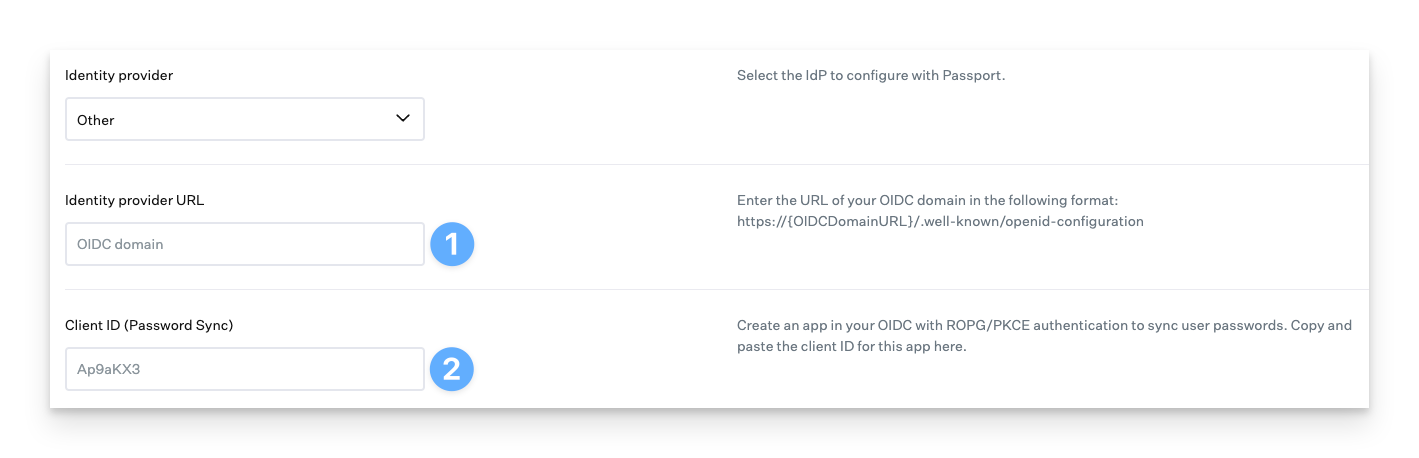
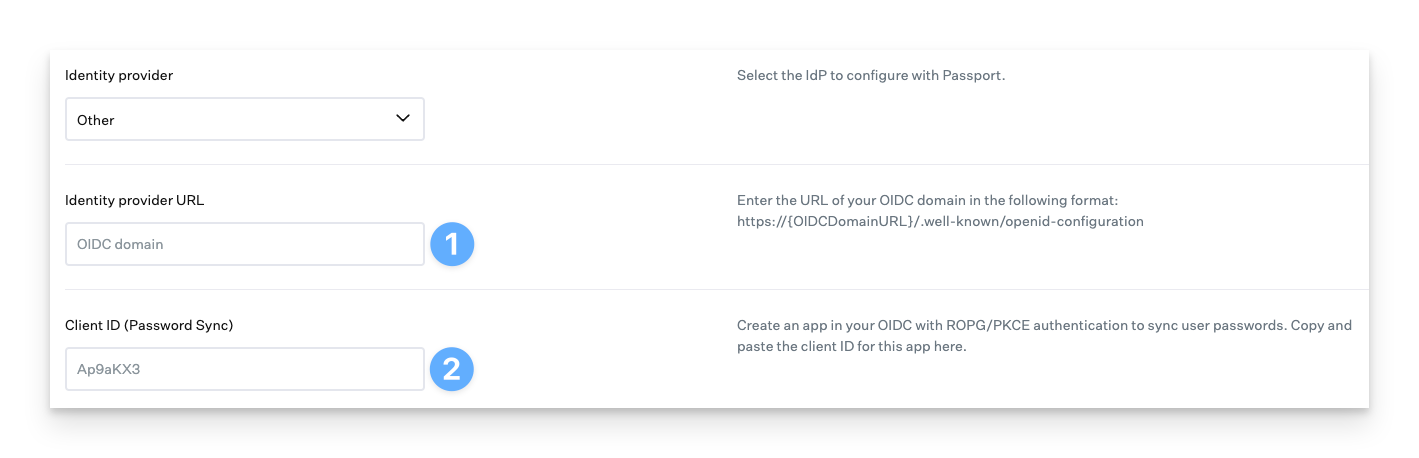
Enter the Identity provider URL.
Enter the Client ID of the Passport App that you created in your IdP (may also be called App ID)
Web Login
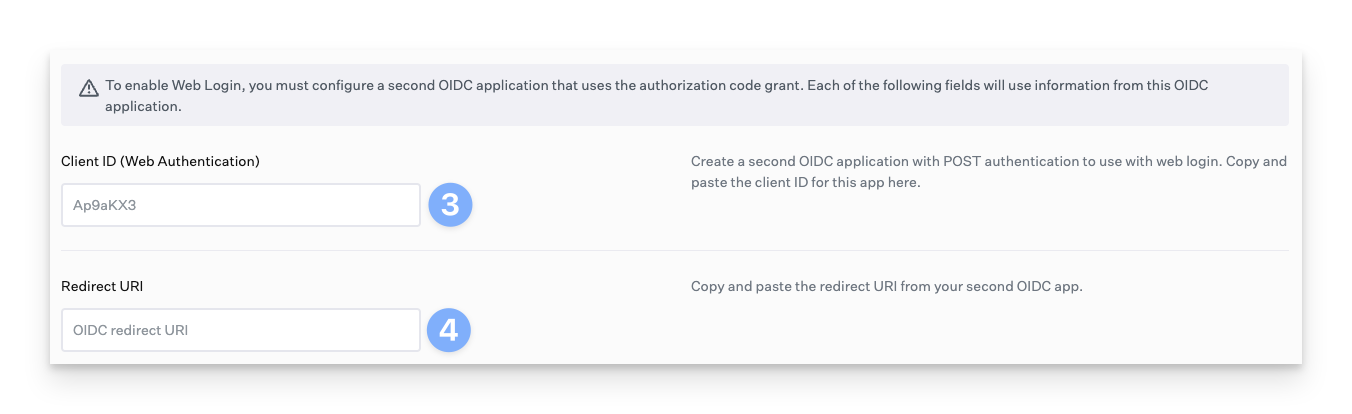
Enter the Identity Provider URL
Enter the Client ID of the Passport App that you created in your IdP (may also be called App ID)
When using Web Login, your app will need to support both PKCE auth as well as Post auth. Some IdPs may require configuring two different apps.
The Redirect URI should be your IdP's default Redirect URI in most cases.
Troubleshooting
There are many factors to consider when troubleshooting Passport issues when selecting the Other option for the Passport IdP. This section assists with obtaining errors and finding the context to understand the errors in order to apply configuration changes.
Kandji Passport Diagnostics
If a user can't log in at the Passport login window, you can bring up Kandji Passport Diagnostics by pressing Command-Shift-K-L on the keyboard. You will see helpful information, such as error messages from your IdP.
If you continue to experience issues with Passport, please reach out to Support for assistance.
Network Connectivity
Passport requires network connectivity to check user credentials against the IdP. When customizing the login window in Passport, show the network manager so users can join a Wi-Fi network as necessary. The network manager respects AirPort security settings in macOS. As a troubleshooting step to rule out network issues, you can connect a test device to a mobile hotspot at the Passport Login Window.
Common Errors
Error: POST token 401 "error":"Unauthorized","error_description":"Authentication Failed: Invalid user credentials"This error indicates a mismatched password, and the password should be verified to work on the identity provider side. A 200 response on the GET request for openid-configuration would suggest that the Identity provider URL and Application ID (aka Client ID) in the Passport Library Item are configured correctly for communication to the IdP.
Error: POST token 403 ”error”:”access_denied”,”error_description”:”End-user does not have access to this application”This error indicates the account may not have access to the Passport OIDC app on the identity provider side, and we should verify said access there. A 200 response on the GET request for openid-configuration would suggest that the Identity provider URL and Application ID (aka Client ID) in the Passport Library Item are configured correctly for communication to the IdP.
Ticket Decode failedTicket decode failedFailed to login with possible error: UnknownThis is typically an issue with the optional client secret. For troubleshooting purposes, completely remove the optional client secret from the Passport library item, and make sure the device checks in. After it has checked in, log out of the local user and log back in with Passport. This error could also be related to a network condition. To rule that out, try connecting to a mobile hotspot as part of troubleshooting to see if the error is still present.
An error occurred fetching user info: No key was found matching "familyName"
This error is returned for an account lacking a Last Name property, also known as a surname, a required user information key for Passport.
Error Code Lookup
Many IdPs will generate their own specific error codes. Check with your IdP to see if they have a lookup page for reading more about the specific error you are receiving from them. An example of this is the error code form from Microsoft for looking up Entra errors.
Helpful Passport Support Articles
These supplemental Passport support articles have useful information for additional troubleshooting.