Defining Threat Events
Endpoint Detection and Response (EDR) creates a threat event when it identifies malware or potentially unwanted programs (PUPs) on a device. This happens in either Detect Posture or Protect Posture, where the threat is also quarantined. Each threat event includes details such as the threat name, classification, process involved, detection date, and current status. You can find all Threat events on the Threats page for devices linked to Blueprints with Avert. Additionally, these events are viewable on individual device records.
Threat-Centric table view
All threat events are organized by file hash for file detections and by detection rule for behavioral detections. This structure simplifies assessing a threat's impact across your Mac fleet. Each grouped event includes a side panel that provides detailed insights into the threat.
Event Information
Each threat event in the threat-centric table view provides essential information to assist InfoSec teams in investigating threats.
Threat ID - Displays the SHA-256 hash value of the detected threat.
Process - Shows the most recently detected process responsible for the threat.
Classification - Indicates the classification category of the threat event.
Detection Date - Records the date when EDR identified the threat.
Devices - Lists the total number of Mac devices affected by the threat event.
Threat Status - Provides a comprehensive view of all threat statuses—Not quarantined, Quarantined, Resolved, and Released—across all devices for the grouped threat event.
Threat Severity Level
Kandji EDR includes severity scoring to help InfoSec teams quickly assess the criticality of detected threats. Each threat event is assigned one of five severity levels: Critical, High, Medium, Low, and Informational.
The threats table includes a Severity column that displays the corresponding severity level for each threat. You can sort and filter threat events based on severity for both file detections and behavioral detections.
The Threats page also features a threats-by-severity pie chart that provides a visual breakdown of threats organized by their severity levels..png)
Classifications
Kandji classifies threats into four categories for file detections—malware, potentially unwanted program (PUP), benign, and unknown—and two categories for behavioral detections: malicious and suspicious.
File Detection Classifications:
Malware - This term refers to malicious software designed to harm devices, individuals, or organizations.
Potentially Unwanted Program (PUP) - These are applications that might be unwanted on a device. PUPs often use high system resources, affecting performance, displaying unwanted ads, and collecting personal information. Unlike malware, PUPs are not intended to cause harm and are usually installed inadvertently with other software, often found in bundled packages.
Benign - This classification is for files initially flagged as malicious but later determined to be non-malicious after further analysis. If you encounter benign threat events, it might be because the item was in your Avert Library Item block list at the time of detection or quarantine.
Unknown - This category is for files that Kandji EDR cannot definitively classify as either malicious or benign based on the available data. If you encounter benign threat events, it might be because the item was in your Avert Library Item block list at the time of detection or quarantine.
Behavioral Detection Classifications
A malicious classification refers to a behavioral activity that intends to cause harm.
A suspicious classification refers to behavioral activity that does not immediately indicate harm but warrants attention for further investigation.
Statuses
All threat events will have a status associated with them. The various statuses that a threat event may have are:
File Detection Statuses:
Quarantined - A detected threat that was automatically quarantined in Protect posture.
Not Quarantined - A detected threat that was not quarantined in Detect posture.
Released - A threat that was initially quarantined but later released and restored to its original location.
Resolved - A detected threat that is no longer at the last detected file path and was not quarantined by the agent.
Behavioral Detection Statuses:
Detected - Malicious behavioral activity was identified but not blocked (Detect posture).
Blocked - Malicious behavioral activity was identified and blocked (Protect posture).
Informational - Suspicious behavioral activity was detected and flagged for visibility.
Quarantining of Malware and PUP will be determined by the posture mode as configured in the Avert Library Item. Please see Endpoint Detection and Response: Configuring the Avert Library Item for more information on how to configure the posture modes in your environment.
Viewing File Detections
In the left-hand navigation bar, navigate to Threats.
Ensure File detections is selected. By default, the Threats page opens to the File detections view.

Viewing Behavioral Detections
In the left-hand navigation bar, navigate to Threats.
Click on Behavioral detections in the top right corner to view behavioral detection events.

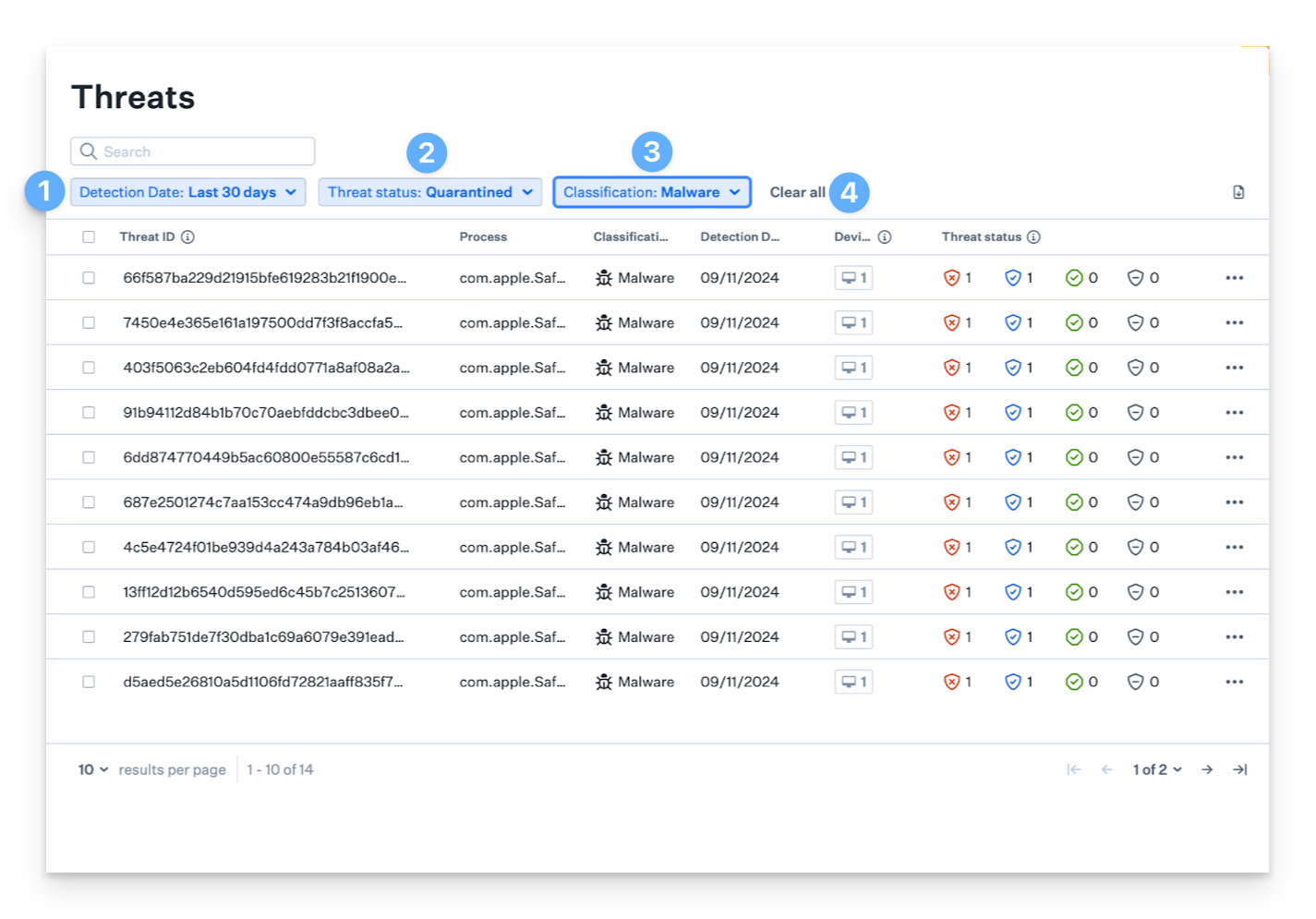
Filtering Threat Events
You can filter threat events for both file and behavioral detections based on their status for easier visualization and remediation.
Select the Detection Date range for which you'd like to view threat events.
Choose the Threat status you want to see in the list; you can select one or multiple.
Pick the Classification type.
When you're finished, click the Clear all button to return to the default view, which shows all statuses for the last 30 days.
Side Panel
The threat-centric table view features a side panel for each grouped event, which can be opened by clicking on a threat event row to access detailed information about that specific threat.
For file detections, the side panel includes:
Latest file name associated with the threat
A global view of all threat statuses—Not quarantined, Quarantined, Resolved, and Released—for the grouped threat event across all devices
First and last detection dates across all devices.
Insights on all unique file paths found related to the threat
For behavioral detections, the side panel includes:
The latest process name associated with the grouped event
A global view of all threat statuses—Detected, Blocked, and Blocked (killed parent)—across all devices.
A description of the malicious or suspicious activity
The malware family associated with the behavioral activity
Informational tags providing additional context
The first and last detection dates across all devices
Device cards
Device cards in the side panel represent devices where the malicious file was found.
For file detections, these cards will display information such as:
Device Name
Serial Number
Blueprint and Library Item.
Malware and PUP Posture Mode
Actionable Events
Threat Event Details:
Threat Status - The current status of the threat on the device.
Path - The file path where the threat was detected.
User - The user associated with the process when the threat was detected.
Detection Date - The date when EDR identified the threat.
Quarantine Date - The date when EDR quarantined the threat.
Resolved Date - The date when the threat was marked as resolved in the web app.
Release Date - The date when the threat was released from quarantine on the device.
Application Bundle Path - The path to the application bundle.
For behavioral detections, these cards will display information such as:
Device name
Serial number
Blueprint and Library Item
Malicious behavioral detection posture mode information
Threat event details:
Threat Status - The current status of the threat on the device.
Detection date - The date when EDR identified the threat.
Rule version - Current rule version
Parent and target process information:
Parent and target process name
Parent and target process ID
Process owner
Image paths for parent and target processes
Command line arguments for parent and target processes
SHA265 hash of the parent and target processes
Viewing a Device's Threat Events in the Side Panel
For file detections:
On the left-hand navigation bar, navigate to Threats.
Click on any threat event to open the side panel.
In the Devices tab, view the device cards for all devices where the malicious hash was detected. Click any device card to expand it and view associated threat events.
For behavioral detections:
In the left-hand navigation bar, navigate to Threats.
Click on Behavioral detections in the top right corner to view behavioral detection events.
Click on any threat event to open the side panel.
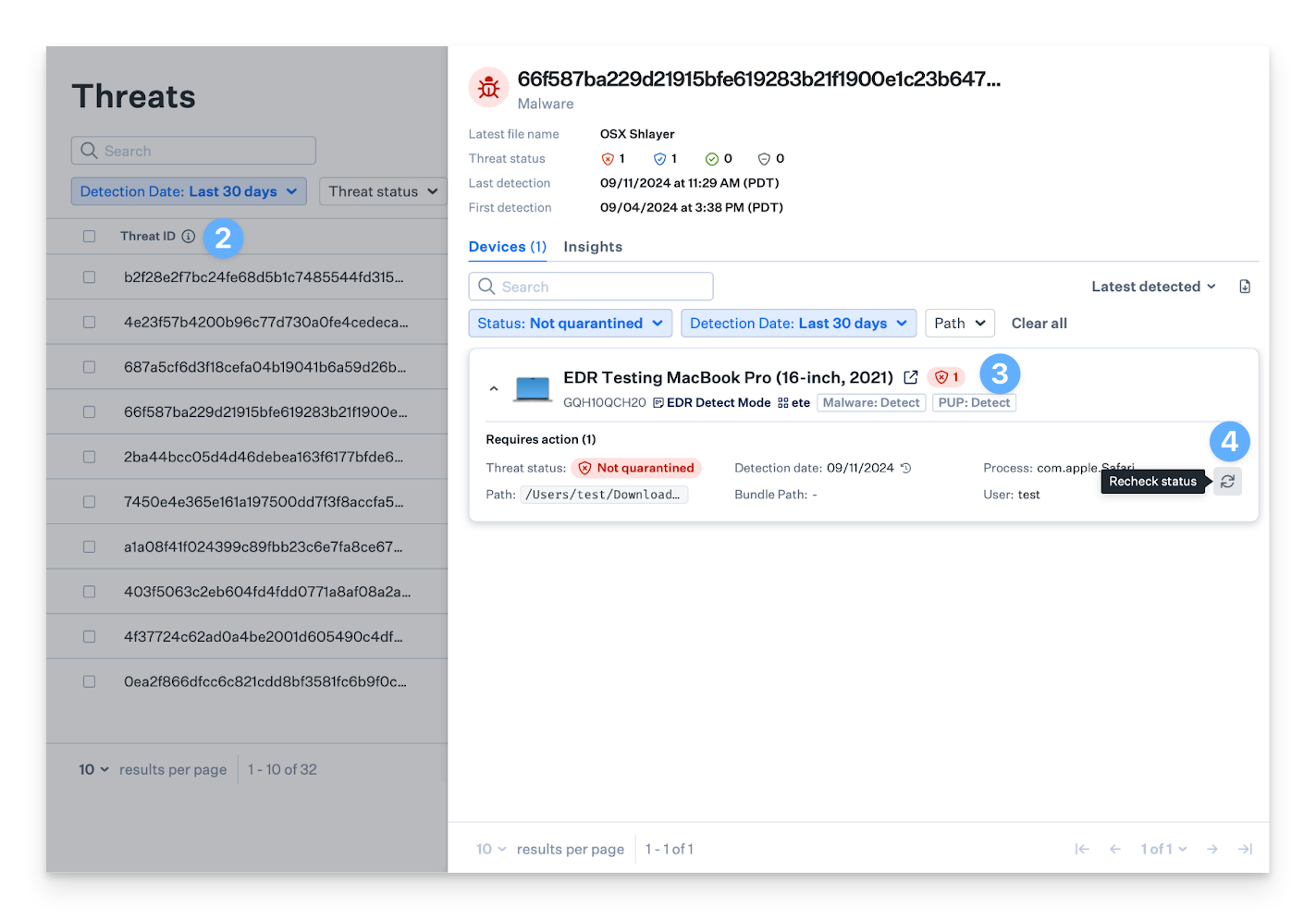
Rechecking the Status of a Threat
When the Malware or PUP posture modes are set to Detect, you can manually check a threat's status in the side panel to see if it's still present at the file path. If the threat is no longer there, its status will update from 'Not quarantined' to 'Resolved.' If the threat is still present, its status will remain unchanged.
On the left-hand navigation bar, navigate to Threats.
Click on any threat event to open the side panel.
Click the desired device card to expand it and view the device's threat events.
Click Recheck status.
When threats are initially detected and removed from a device, their status will change from Not quarantined to Resolved once the Malware or PUP posture modes in the Avert Library Item are set to Protect mode. This update also occurs when a new Blueprint with these settings is applied to the device.
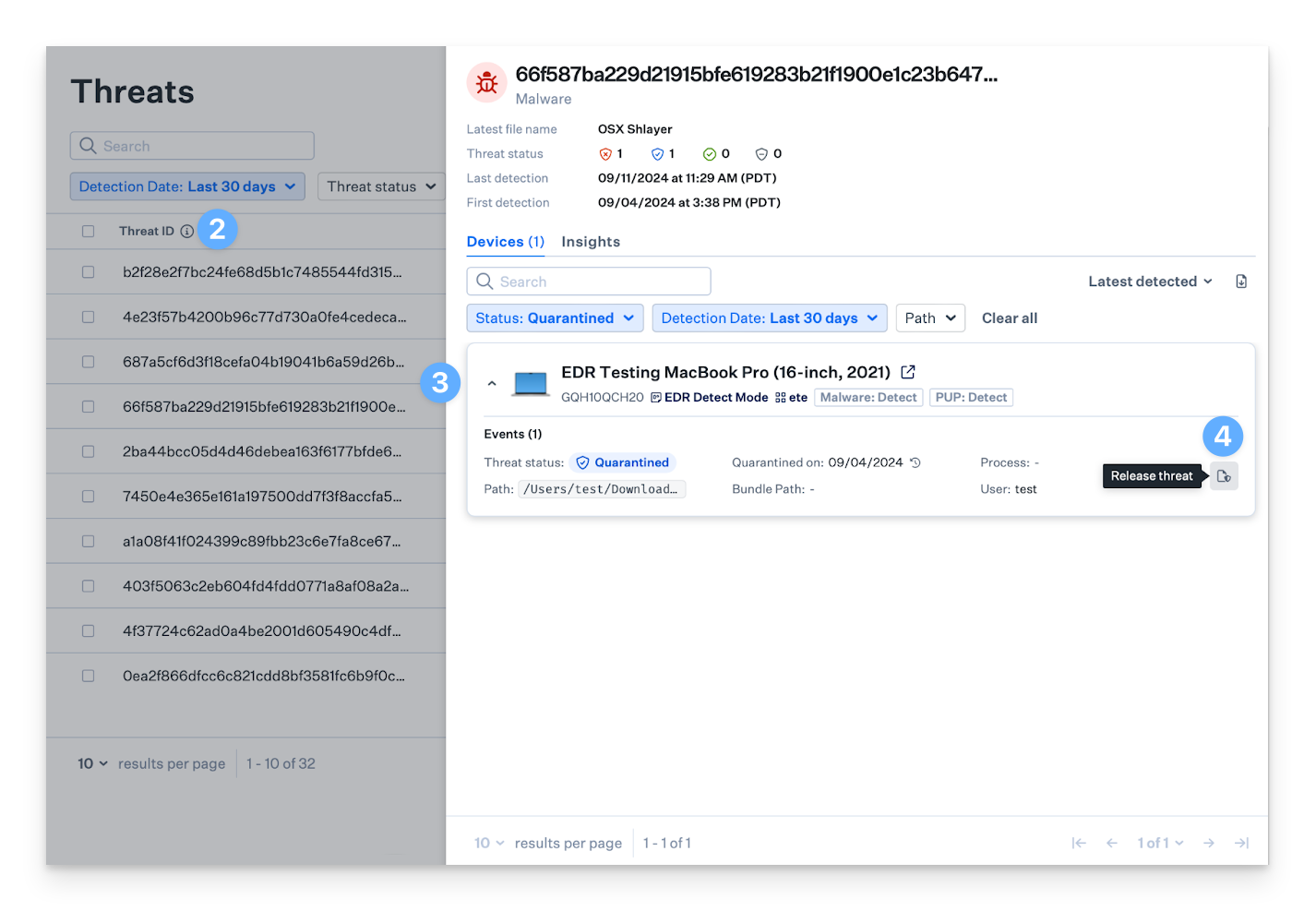
Releasing a Threat Event
There might be situations where InfoSec teams need to release a threat event for specific files or applications that were mistakenly quarantined, such as a security tool or application used by the organization. Releasing a threat event involves adding the item to the Allow list for the associated Avert Library Item.
The threat event release action will only apply to the Blueprints assigned to the Avert Library Item. Releasing a threat will release it from all Mac computers where the threat has been detected.
On the left-hand navigation bar, navigate to Threats.
Click on any threat event to open the side panel.
Click the desired device card to expand it and view the device's threat events.
Click Release threat.
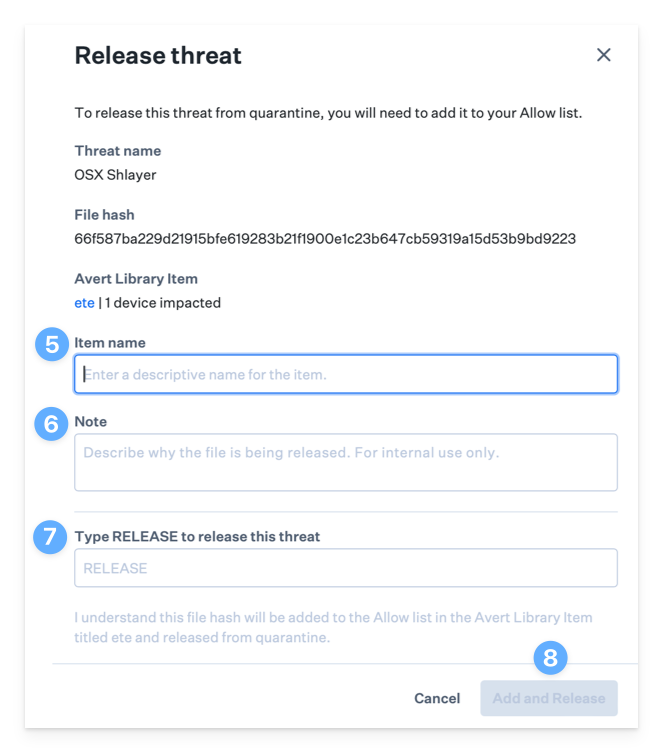
Enter an Item Name.
Optionally, enter an internal note stating why the threat event is being released.
Type RELEASE to release the threat.
Click Add and Release to add the threat to your Allow list and release the threat.
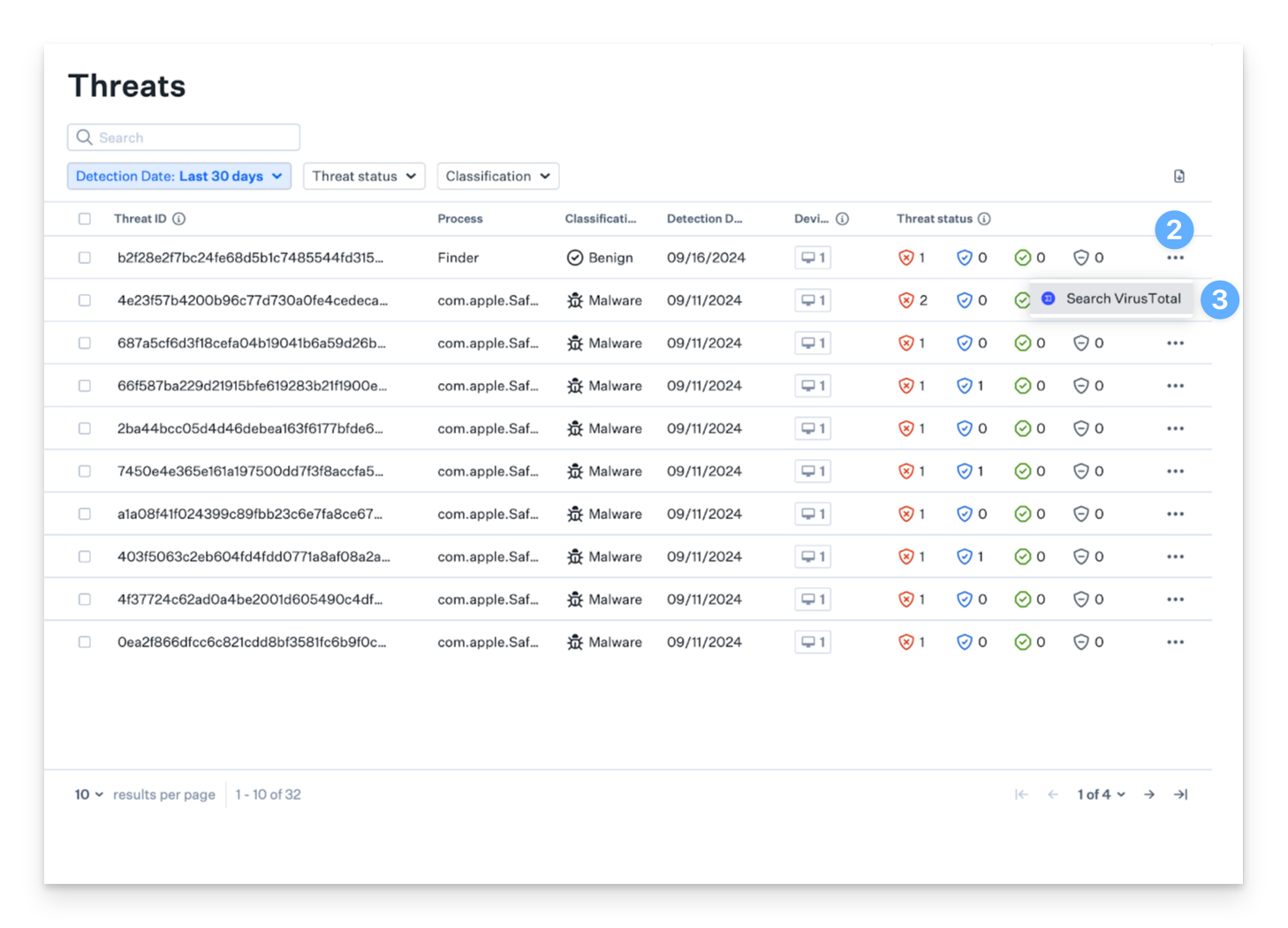
Performing a VirusTotal Search
VirusTotal is a powerful tool that provides in-depth analysis and insights into files and URLs. The web app includes a convenient feature for searching hashes within VirusTotal, allowing you to access additional contextual information directly from a threat event entry without leaving the app.
On the left-hand navigation bar, navigate to Threats.
Click the ellipsis located on the far right of the desired threat event.
Click Search VirusTotal to search the hash in VirusTotal.
Kandji EDR may classify certain hashes as malware or PUP, even if VirusTotal has no detections on them or considers them non-malicious; this is expected due to Kandji EDR’s utilization of multiple threat sources.
Exporting Threat Events in CSV
In addition to using the Kandji API, InfoSec and IT teams can export the list of threat events directly from the admin console. The export icon in the threat-centric view applies the current filter settings and generates a CSV file with detailed information about each Threat event in separate columns. This feature is available in both the main Threats module view and the Threats tab under Device Record.
On the left-hand navigation bar, navigate to Threats.
Select either File detections or Behavioral detections.
Click the Export icon on the far right of the threat events list view. A CSV export file will download automatically.