What is covered in this guide:
(EDR) functionality is available for Mac devices assigned to Blueprints containing Avert. This new library item turns on EDR functionality in a Blueprint — you don't need to install additional software. You can view identified threats in the Kandji web app on the Threats page and the device record page.
The Endpoint Detection and Reponse add-on is required to use the Accessory & Storage Access Library Item. However, the Avert Library Item is not required to be assigned to the device Blueprint in order to deploy this Library Item.
Threats Page
Access the Threats page by clicking Threats in the left-hand navigation bar of the Kandji web app. This page lists the total number of Threat events affecting your Mac devices across the designated Blueprints containing Avert, along with information such as device impacted, threat name, classification, the process responsible for the Threat event, detection date, and status. Kandji Avert categorizes Threat events as “Malware” or “Potentially Unwanted Programs” (PUP).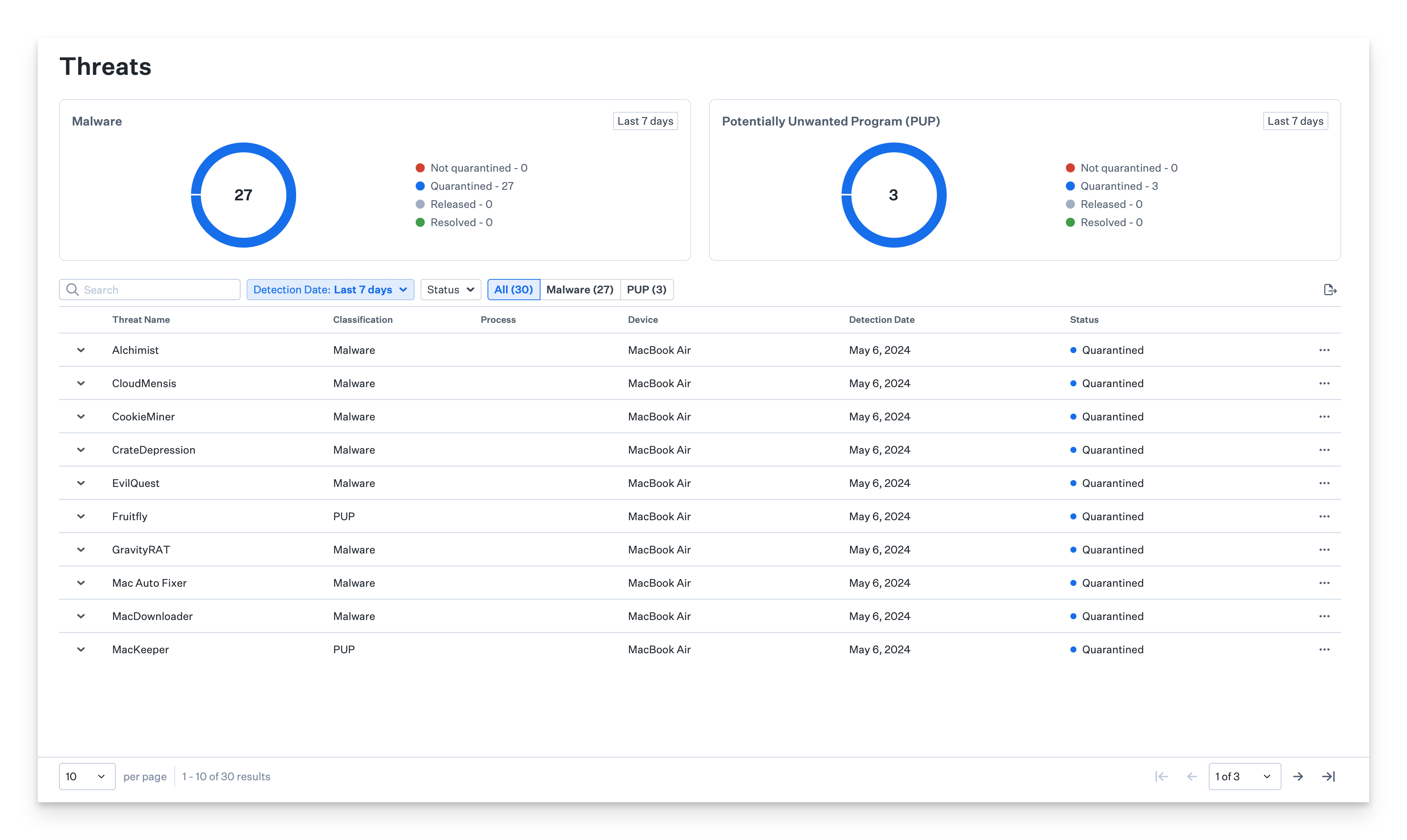
The Threats page also provides quick filters by Classification and Status. Click the disclosure triangle to the left of a Threat event to reveal additional information, including detection and quarantined dates, path, hash, and user information. A similar view is available on the device record page for individual devices.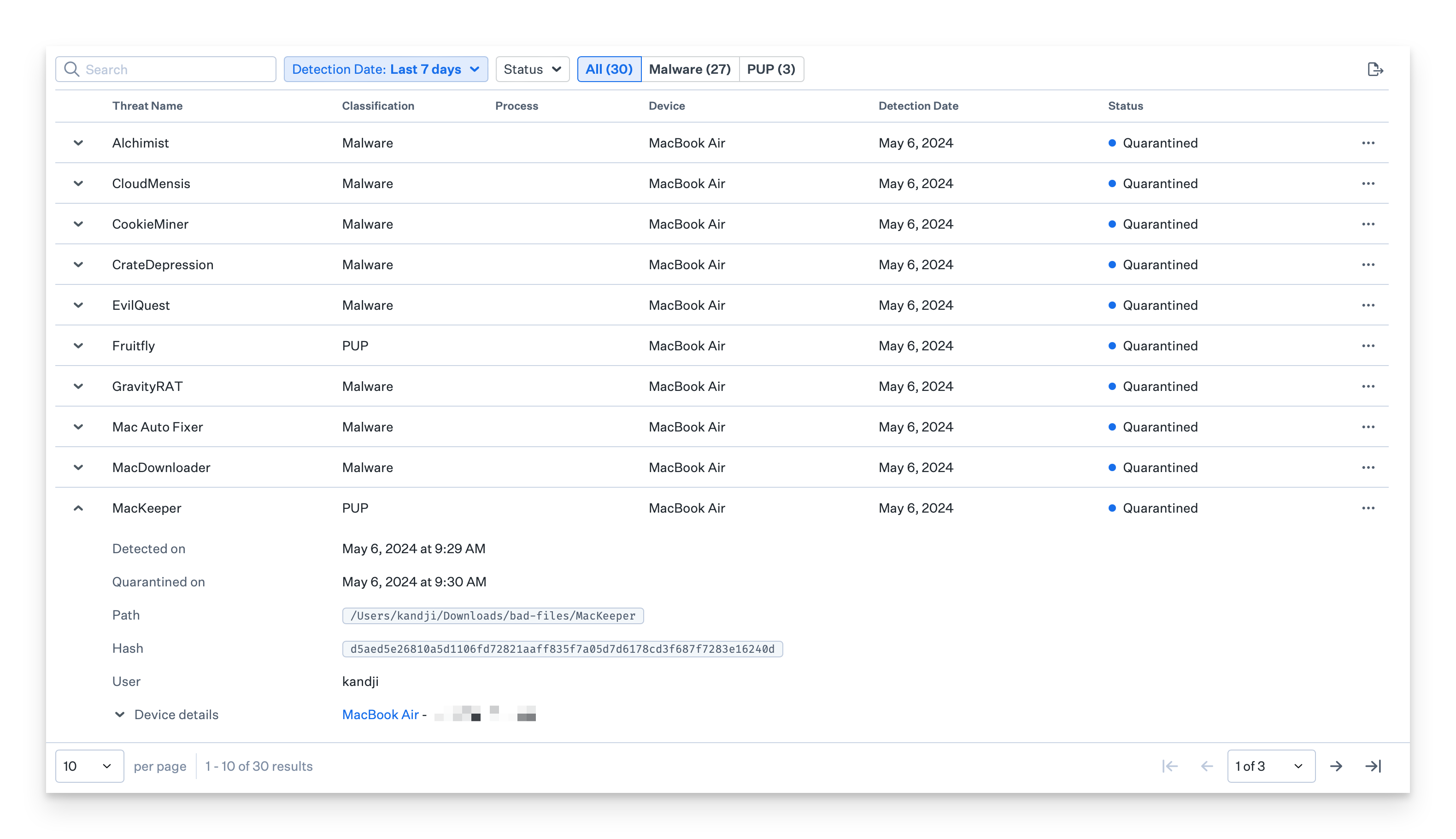
Device Record Page
The device record page provides a total count of detected threat events on the device. To view the detected threat events, click the Threats tab.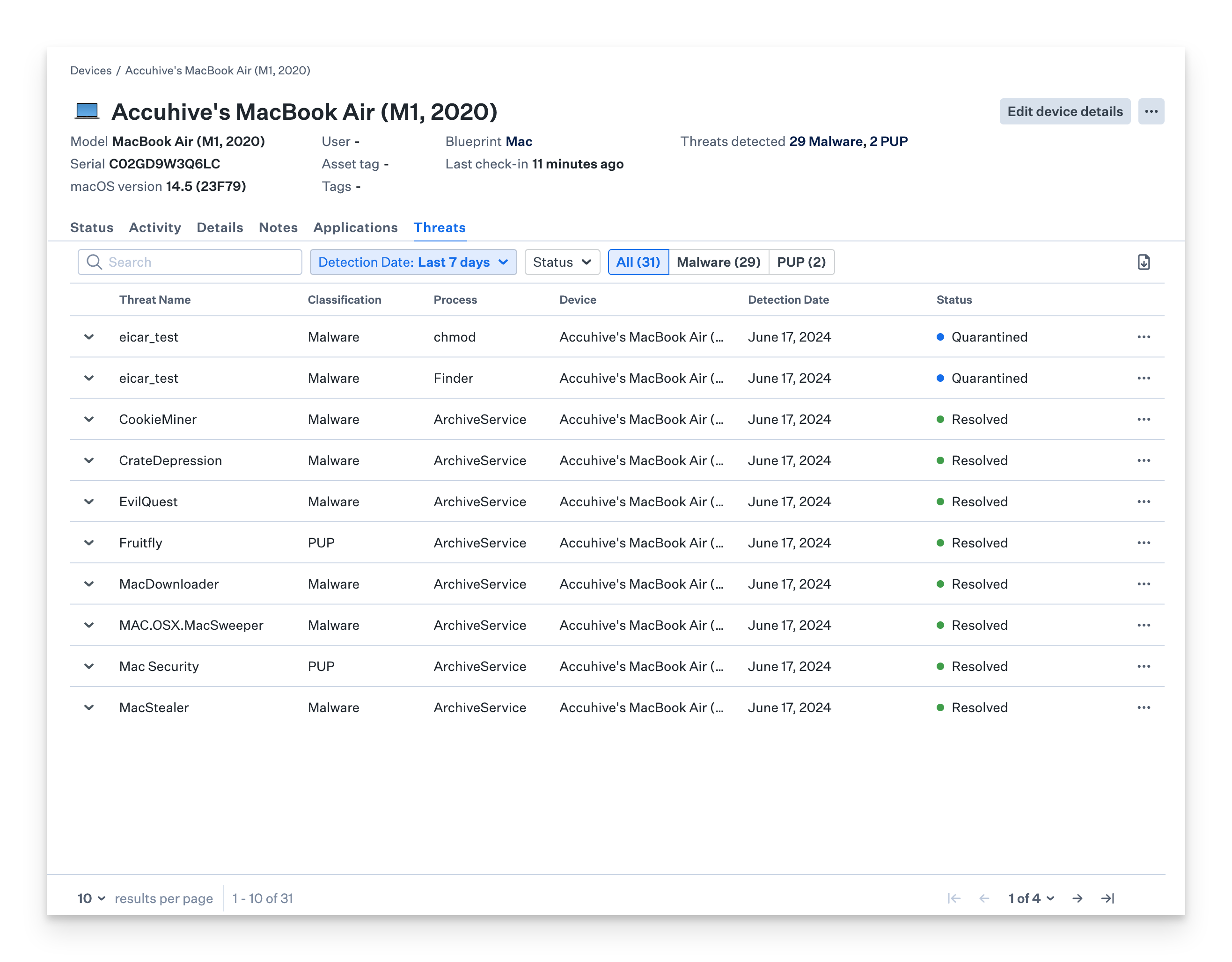
Click the disclosure triangle to the left of a Threat event in the Threats tab to reveal additional information, including detection and quarantined dates, path, hash, and user information.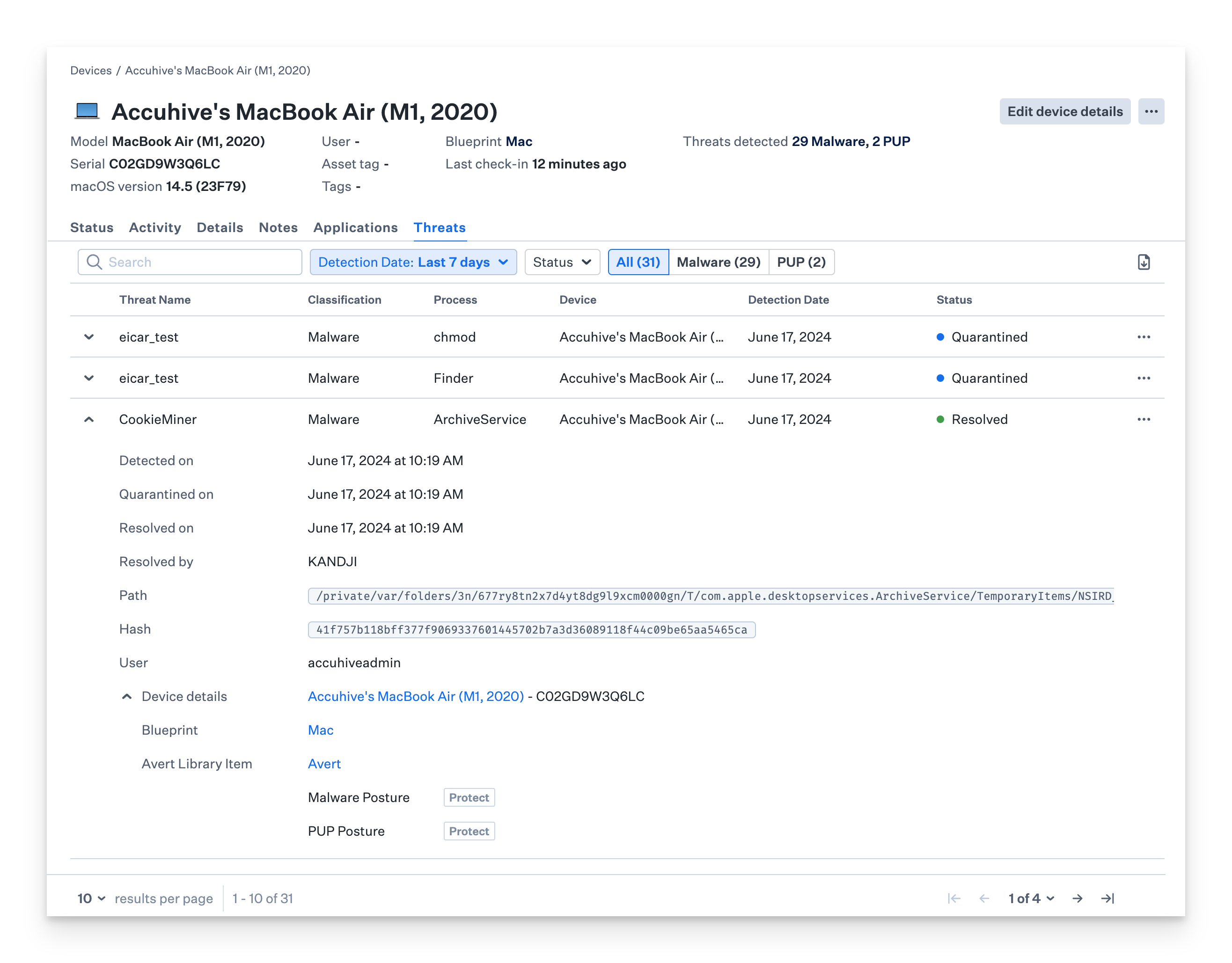
Next Steps
Please see the - Understanding Threat Events support article to learn more about Threat events.