Create a SAML Connection
In Kandji, navigate to the Settings page.
Click the Access tab.
Find the Authentication section and click the Add button on the bottom left.
In the new pane, click Custom SAML.
Click Next.
Click Show Advanced Details.
Copy the Assertion Consumer Services URL into a text document for later use.
Copy the Entity ID into a text document for later use.
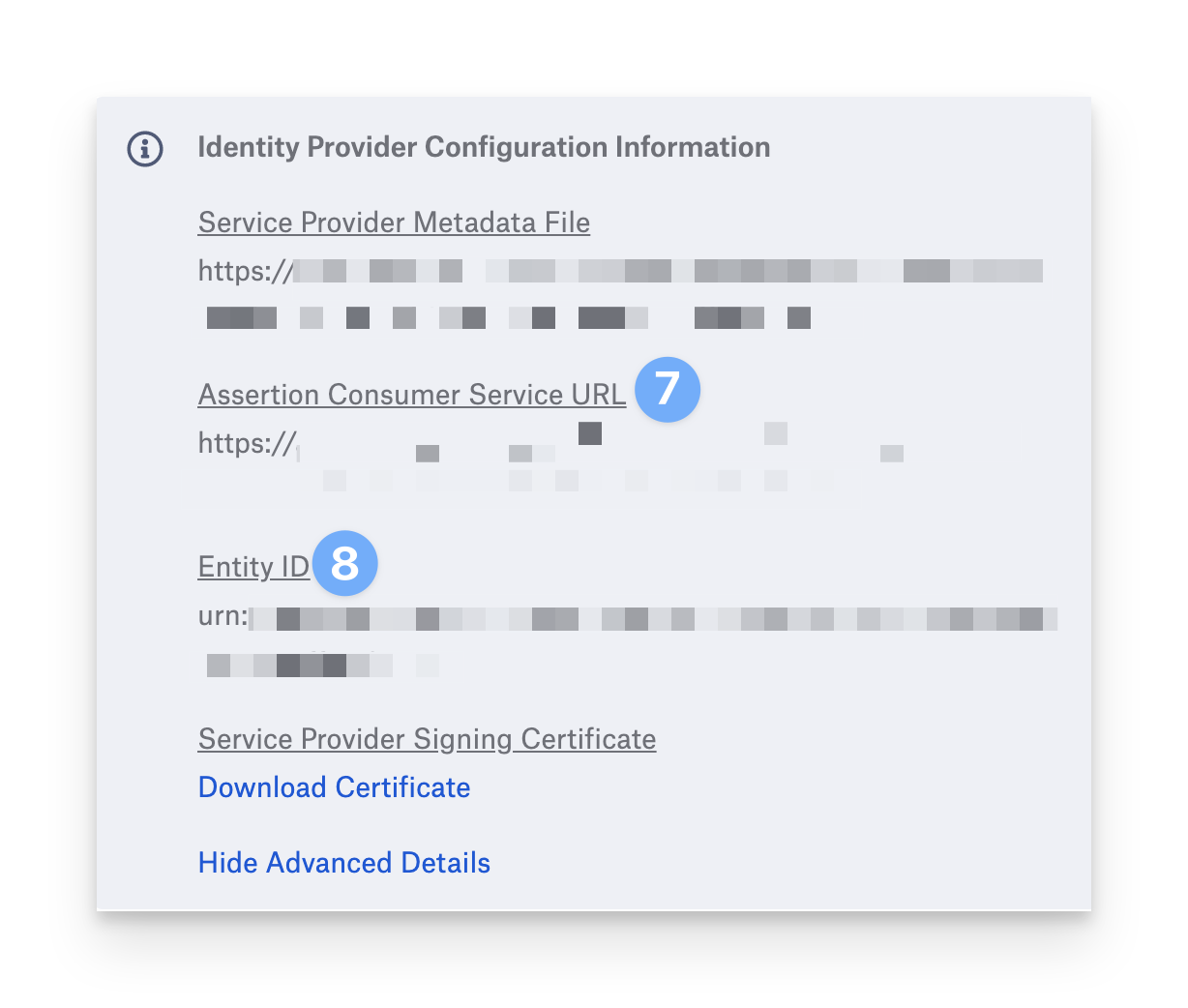
Leaving this tab open, continue to the Google Workspace Admin console following the instructions below.
Add the Kandji application to Google Workspace
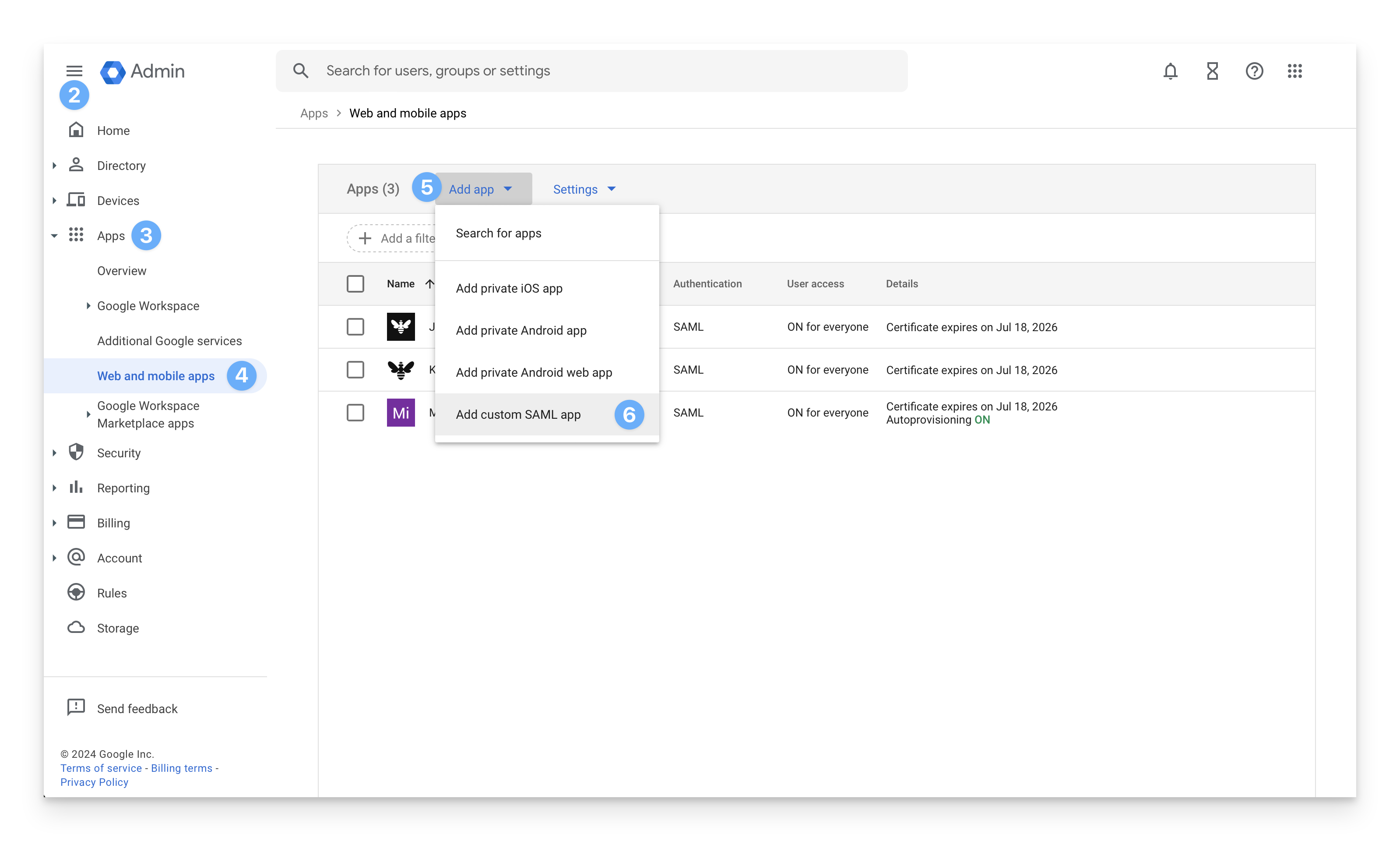
In a new browser tab, log in to admin.google.com with a Google Workspace admin account.
Click the menu symbol at the top left.
Select Apps.
Select Web and mobile apps.
Click the Add App dropdown.
Select Add custom SAML app.
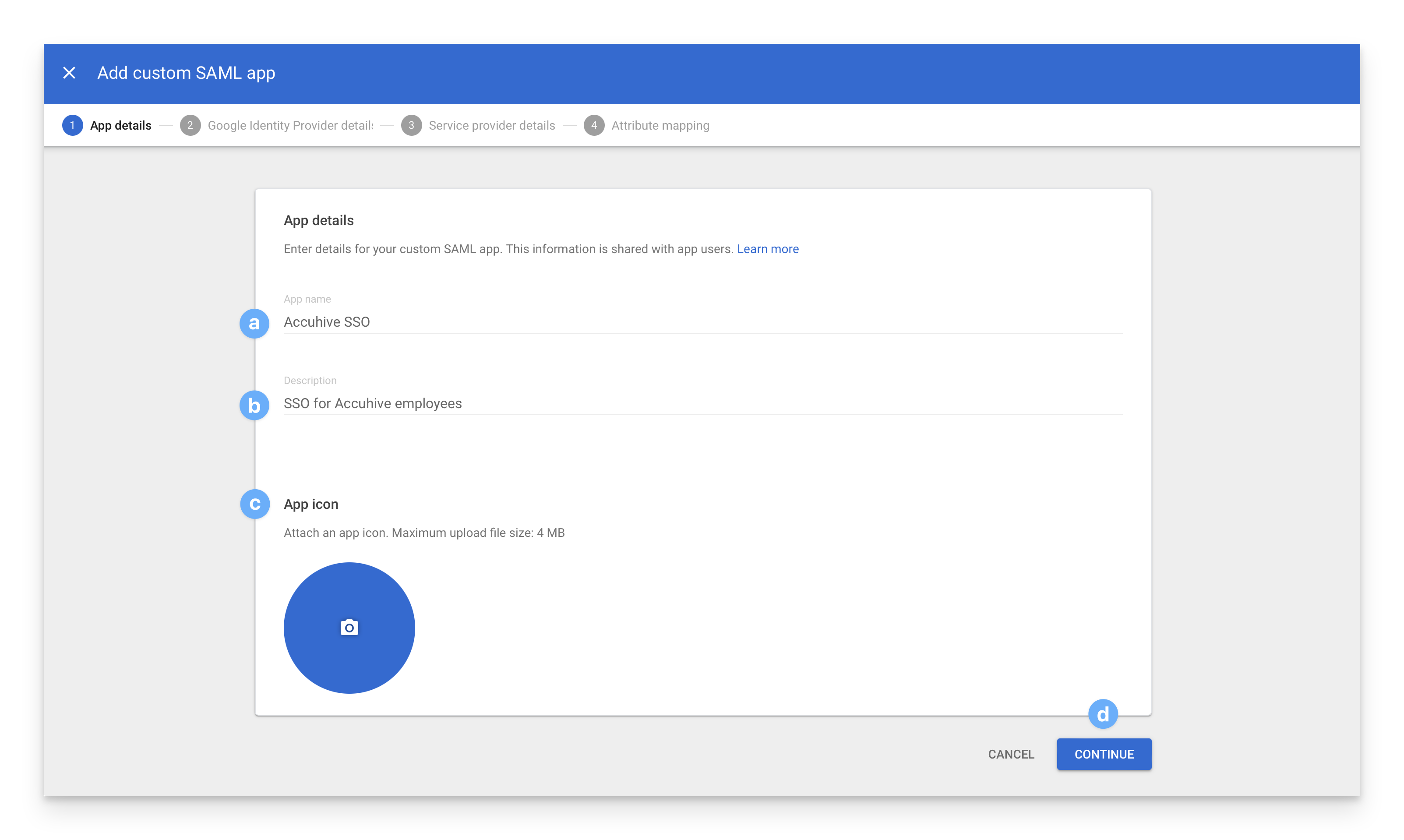
On the App details page:
Set an App name.
Optionally, add a Description.
Upload an optional App icon.
Click Continue.
On the Google Identity Provider Details page, use Option 2: Copy the SSO URL, entity ID, and certificate.
Copy the SSO URL and save it to a text document for later use.
Download the Certificate and save it.
Click Continue.
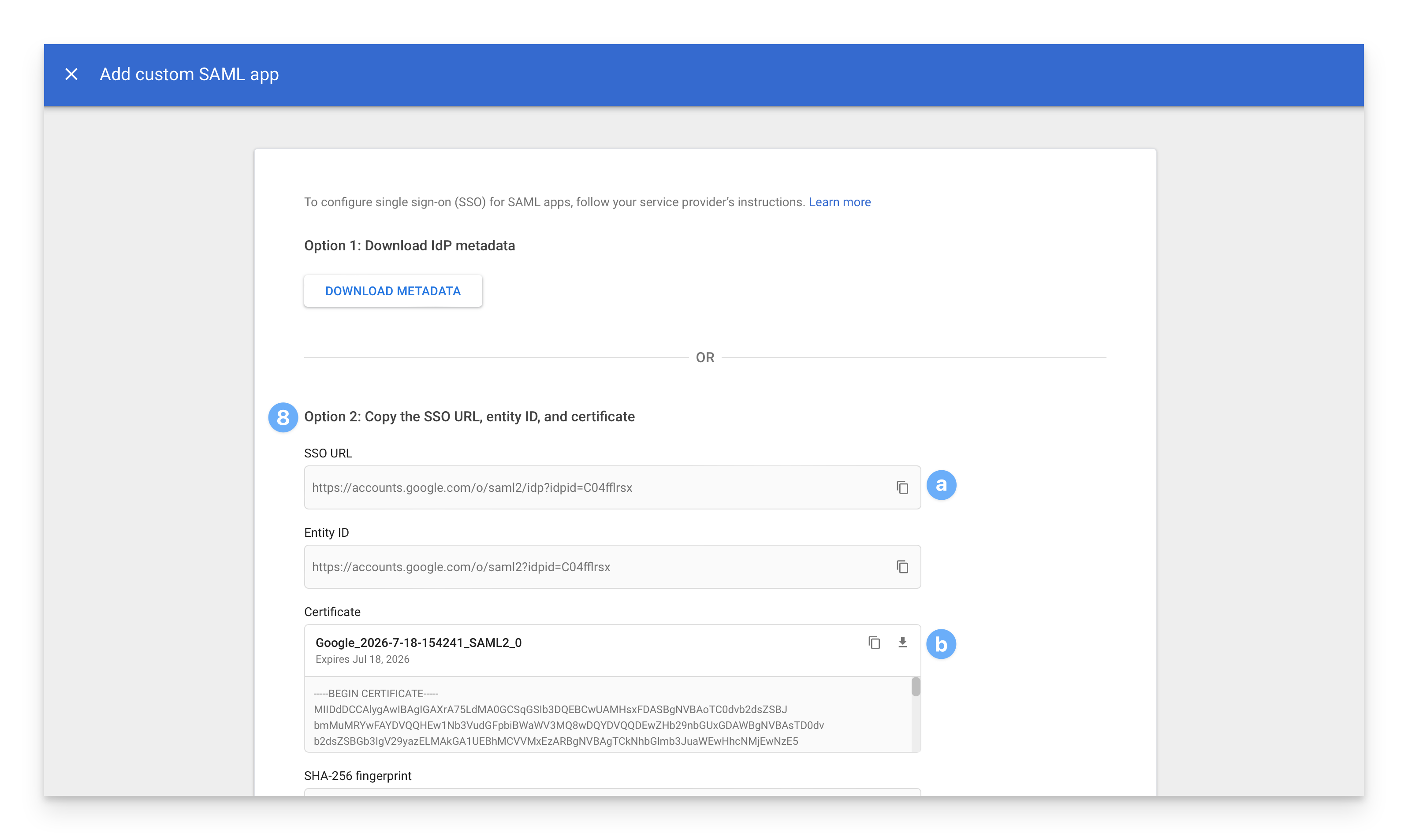
On the Service Provider Details page:
In the ACS URL field, paste the Kandji Assertion Consumer Service URL you copied earlier.
Paste the Kandji Entity ID you copied earlier in the Entity ID field.
Make sure that the Signed response option is checked.
Set the Name ID Format to UNSPECIFIED.
For NameID, make sure that Basic Information > Primary email is selected.
Click Continue.
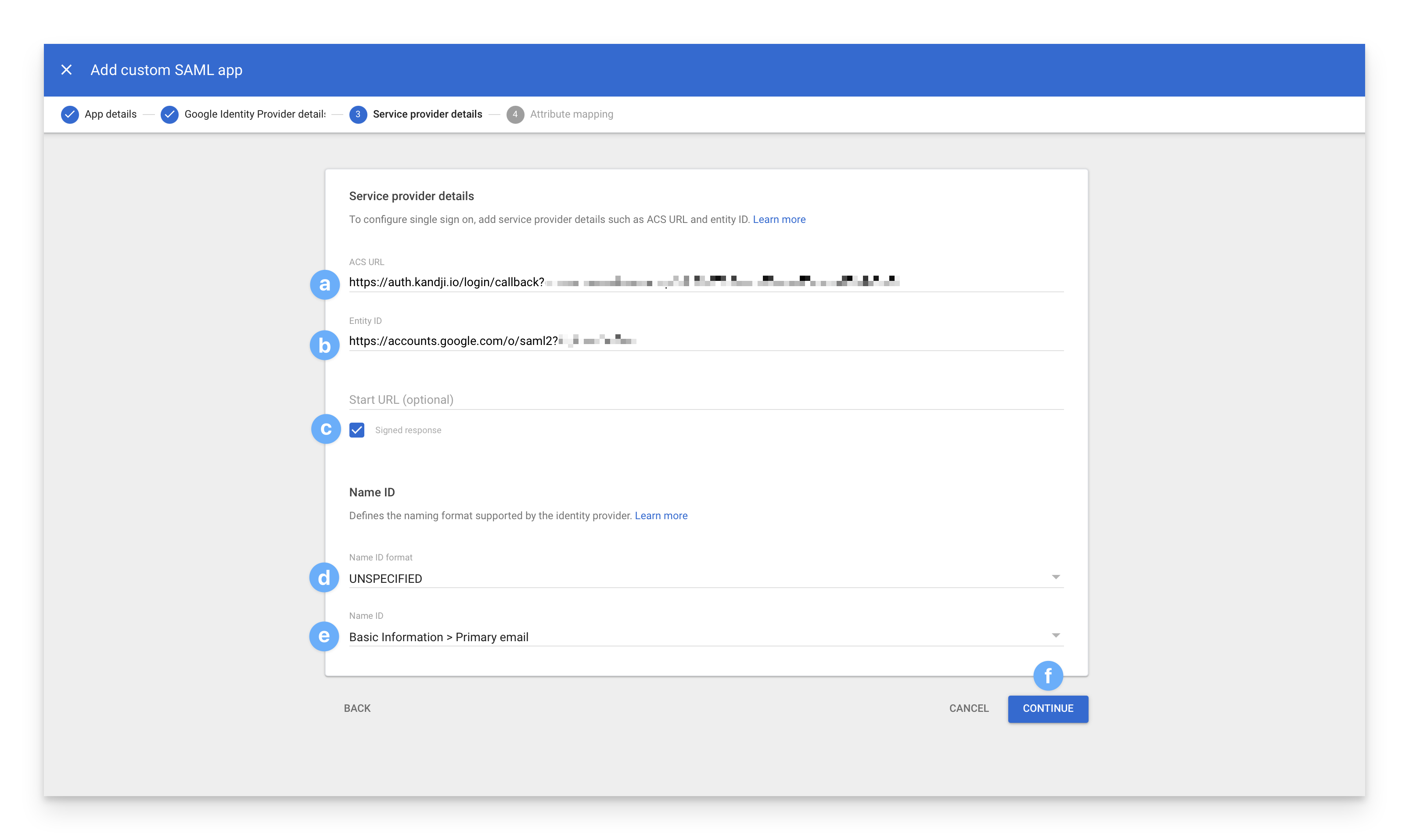
On the Attribute Mapping page:
Click on Add Mapping twice so that you can add the following two mappings:
Find the First name attribute in the dropdown menu and paste the following string:
schemas.xmlsoap.org/ws/2005/05/identity/claims/givennameFind the Last name attribute in the dropdown menu and paste the following string:
schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Click Finish.
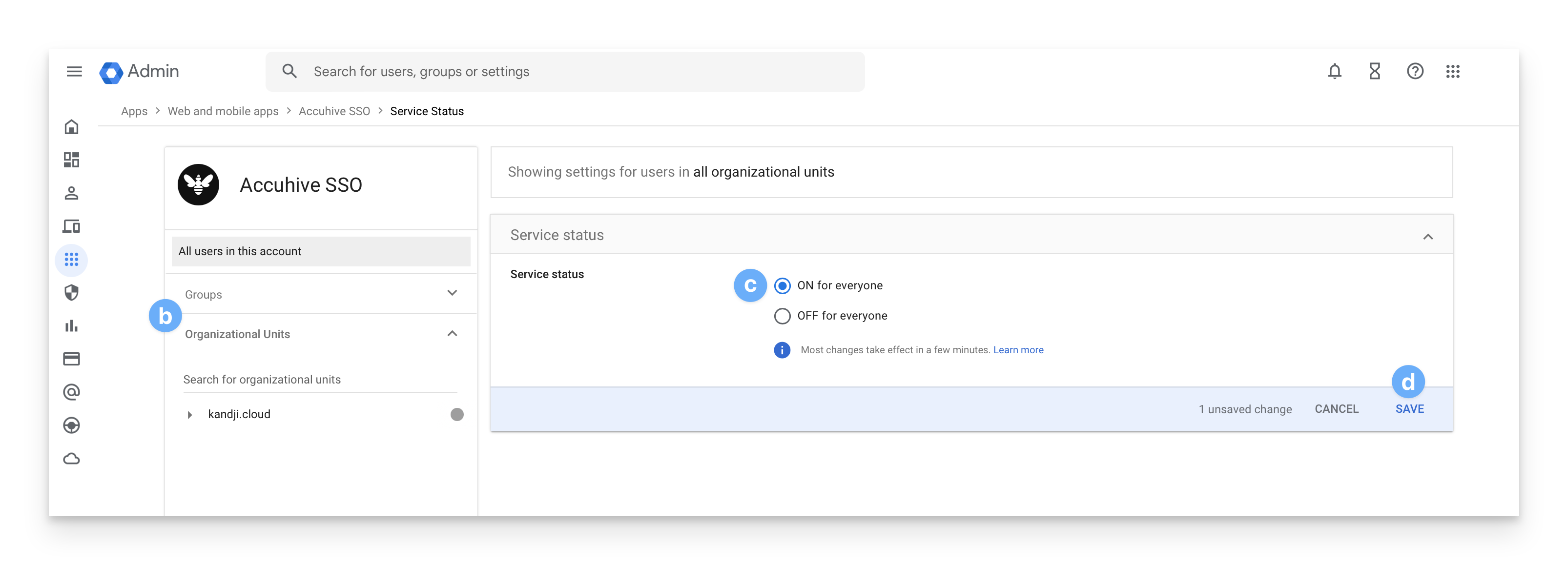
On the resulting app page, check under User Access to ensure that the service is turned on and that either a user group or organizational unit is selected.
If it displays OFF for everyone, click on the disclosure triangle in the user access panel to assign a user group or organizational unit to the app.
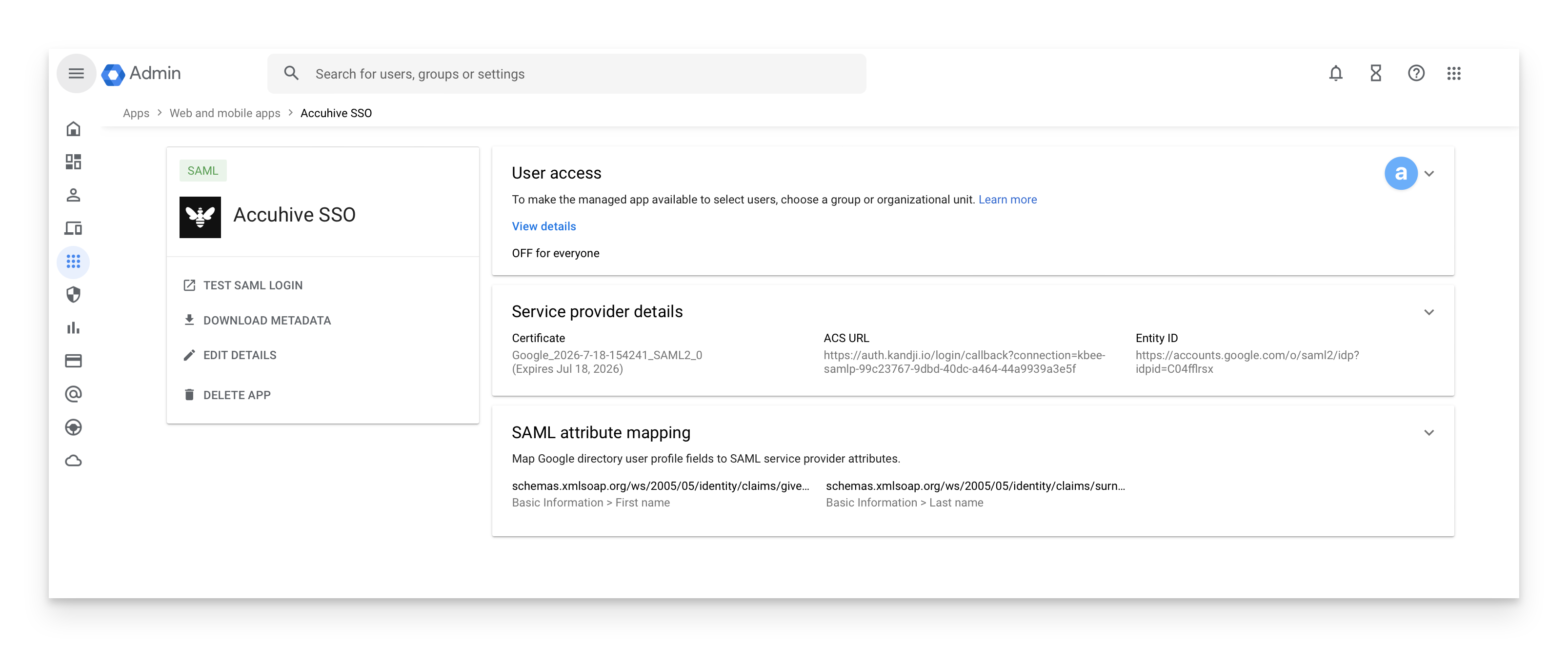
Optionally, please select a group or organizational unit to enable the service (by default, it will display all organizational units).
Set service status to ON for everyone.
Click Save.
The Required Claim Attributes section of the SAML-based Single Sign-on knowledge base article provides more about Kandji attribute mappings.
Configure the SAML Connection in Kandji
Go back to the Custom SAML modal in Kandji.
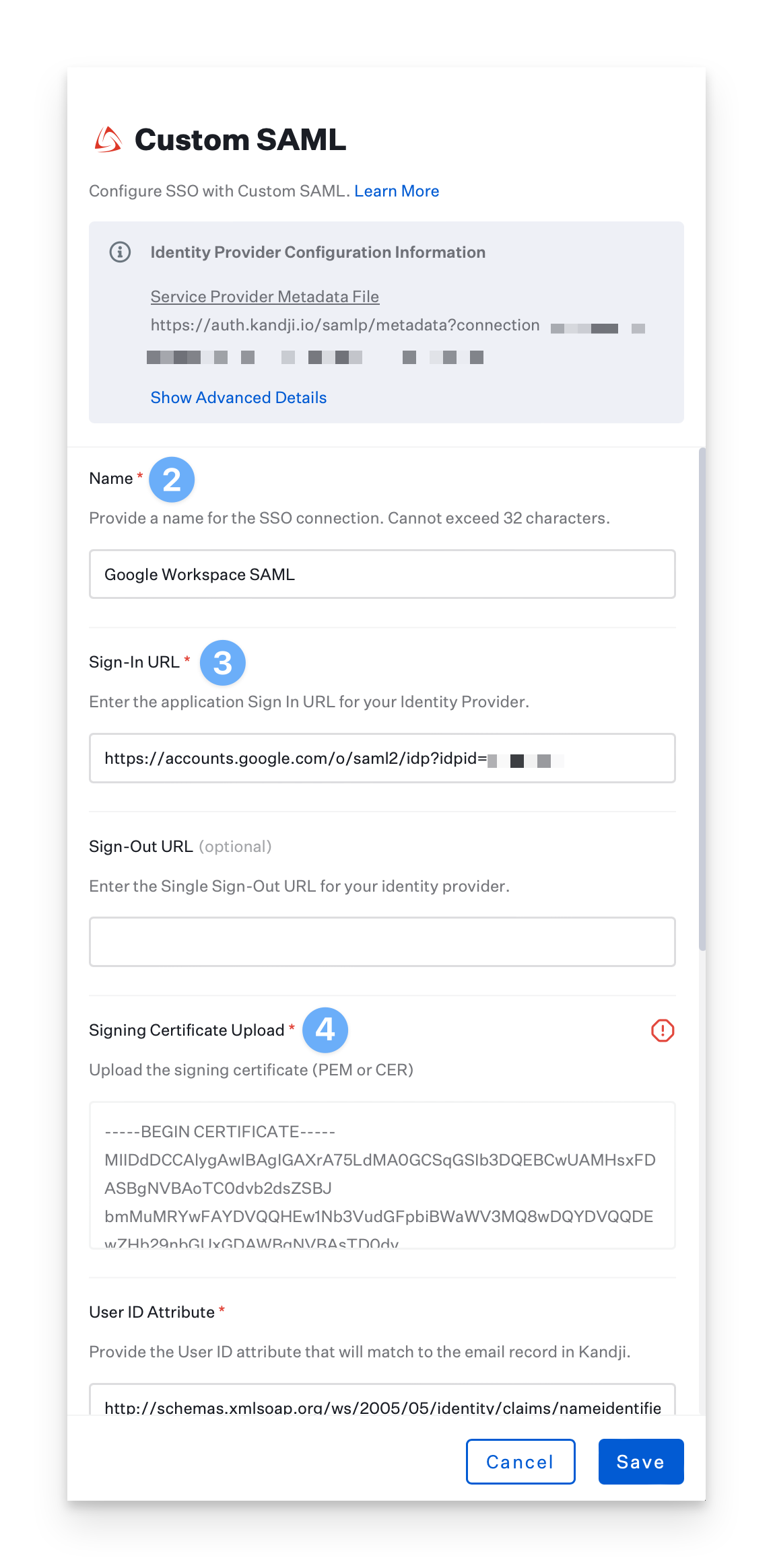
Give the connection a Name.
Paste in the Sign-in URL you copied from Google Workspace.
Upload the certificate you downloaded from Google Workspace.
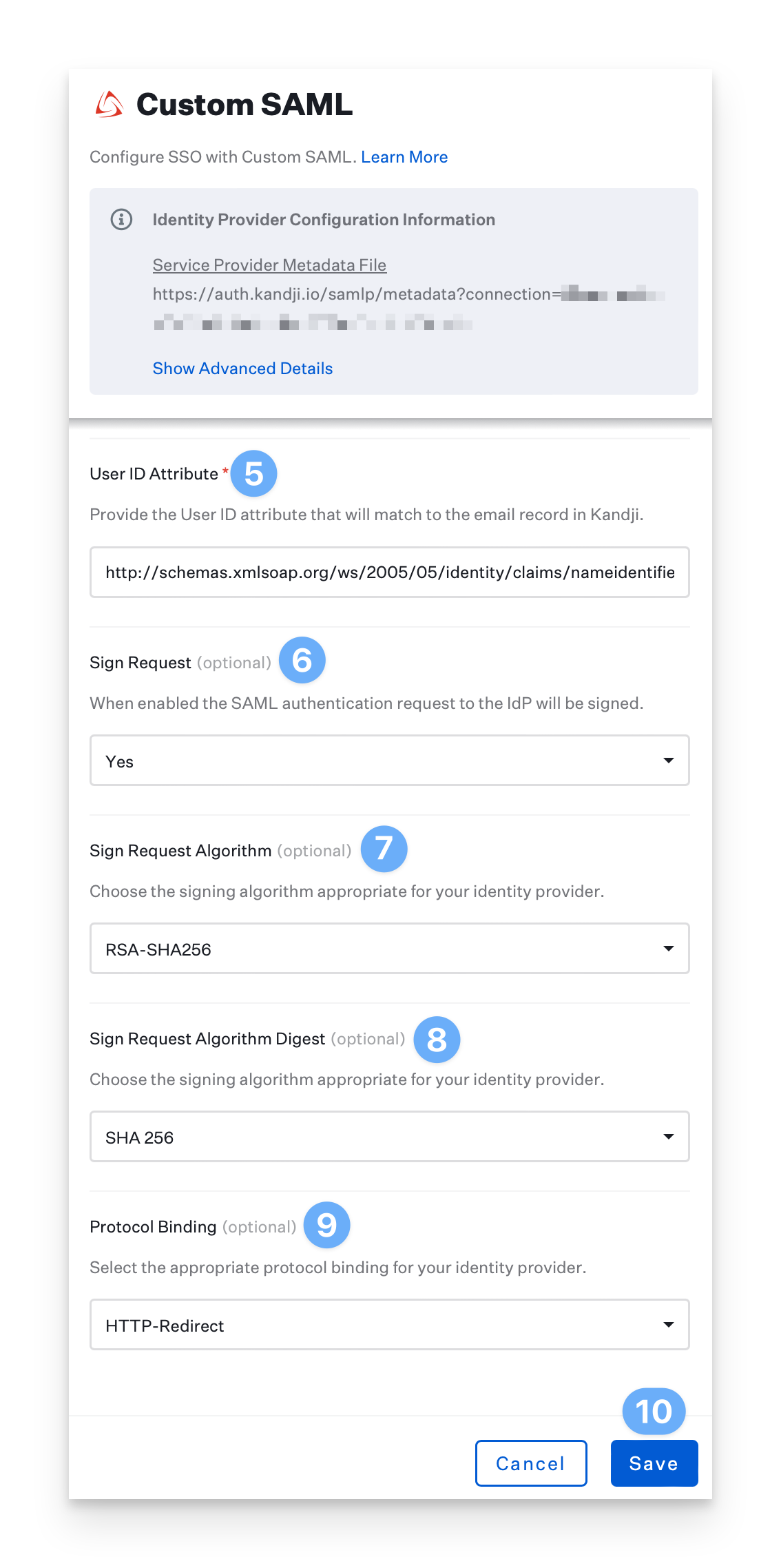
Ensure that the User ID Attribute is set to the default value of
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifierEnsure that Sign Request is set to Yes.
Ensure that Request Algorithm is set to RSA-SHA256.
Ensure that Sign Request Algorithm Digest is set to SHA 256.
Set the Protocol Binding to HTTP-POST.
Click Save and then click Cancel to exit the configuration.
Enable the SAML Connection
Once you have configured the SAML connection in Kandji and your identity provider, you can enable it. For step-by-step instructions, please refer to the Enable and Manage a Connection section of our Single Sign-on support article.
Enforce Single Sign-on
Once you have configured at least one Single Sign-on connection, you can disable the standard authentication connection. Disabling Kandji standard authentication will disable the ability for Kandji administrators in your tenant to authenticate via email/password, Google Sign-in, or Office 365 Sign-in. Please refer to our Single Sign-on support article for step-by-step instructions.
Add a User to Kandji
Add a user to the Admin Team in Kandji by clicking New User.
Fill in all of the corresponding user information. This user must exist in Google Workspace and must be assigned to the Kandji SSO app in your Google Workspace tenant.
Click Submit.
.png)
Once the invite is submitted, close the Invite User window.
Refresh the Access page in Kandji. You should see the user you just added.
Check the user’s email to accept the invitation and log into Kandji with the new SAML SSO connection.