What is SCIM?
SCIM, or the System for Cross-domain Identity Management, is a protocol designed to make managing user identities across different systems simpler and more efficient. It's particularly useful when you're using multiple cloud-based applications, as it helps automate the process of adding and removing users.
How SCIM Works
SCIM involves two main roles:
Client - This is usually an identity provider or identity access management system, like Microsoft Entra ID or Okta, that manages core identity data.
Service Provider - A software-as-a-service (SaaS) application, like Kandji, that uses identity data to manage user access and permissions.
SCIM supports several operations, including provisioning, synchronization, and de-provisioning. This one-way sync allows you to automatically create user accounts in Kandji, keep user attributes up-to-date between your MDM and IdP, and automatically remove or disable user accounts when they are no longer needed.
Configuring SCIM in Kandji
To configure a SCIM integration between your Identity Provider (IdP) and Kandji, you will need to:
Create a new SCIM Directory Integration in Kandji
Obtain the SCIM API URL and API token from Kandji to use with your IdP.
Access your IdP to create an app integration, map SCIM attributes, and push desired user groups.
Create a New SCIM Directory Integration
Navigate to Integrations in the left-hand navigation bar.
Click Discover integrations in the upper-right of the Integrations page.
On the SCIM protocol tile, click Add and configure.
Click Get started.
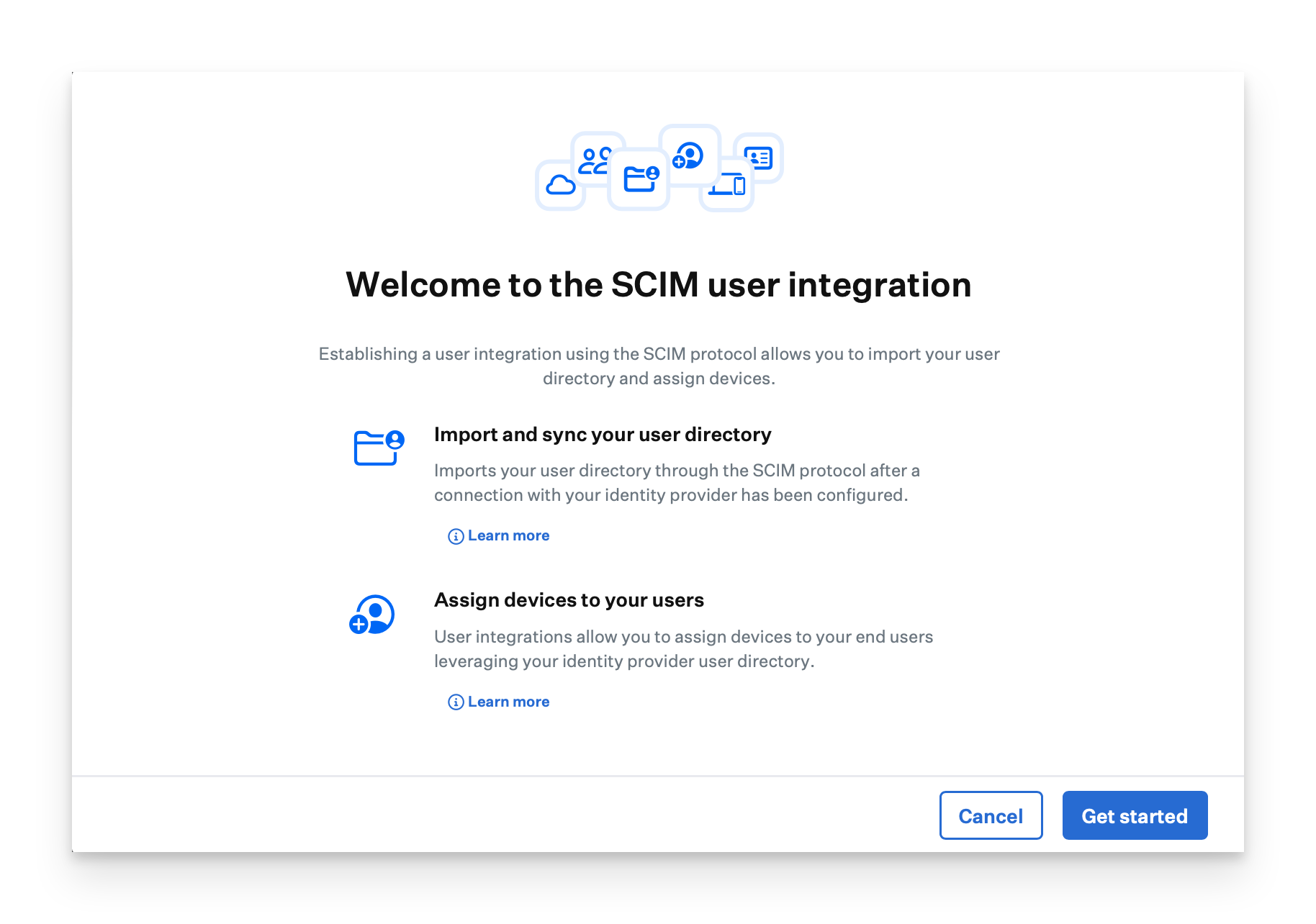
Enter a unique name for the SCIM integration.
Click Generate token. The SCIM user directory integration uses an HTTP authorization header with a Bearer Token as the authentication method.
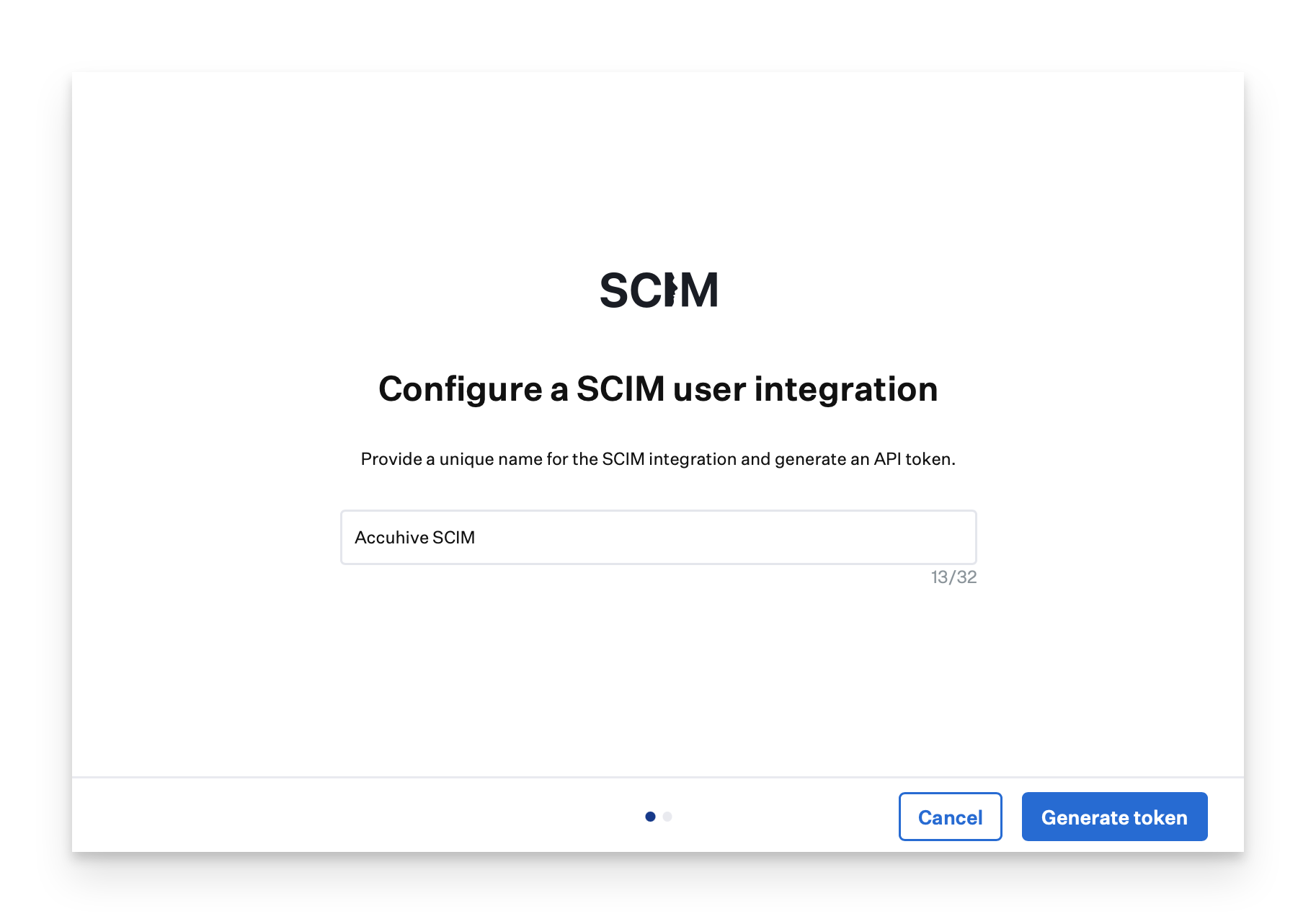
Click Copy token.
Confirm that you have copied the token and know you will need to change it if you want to see the token details again.
Click Done. You will return to the Integrations page.
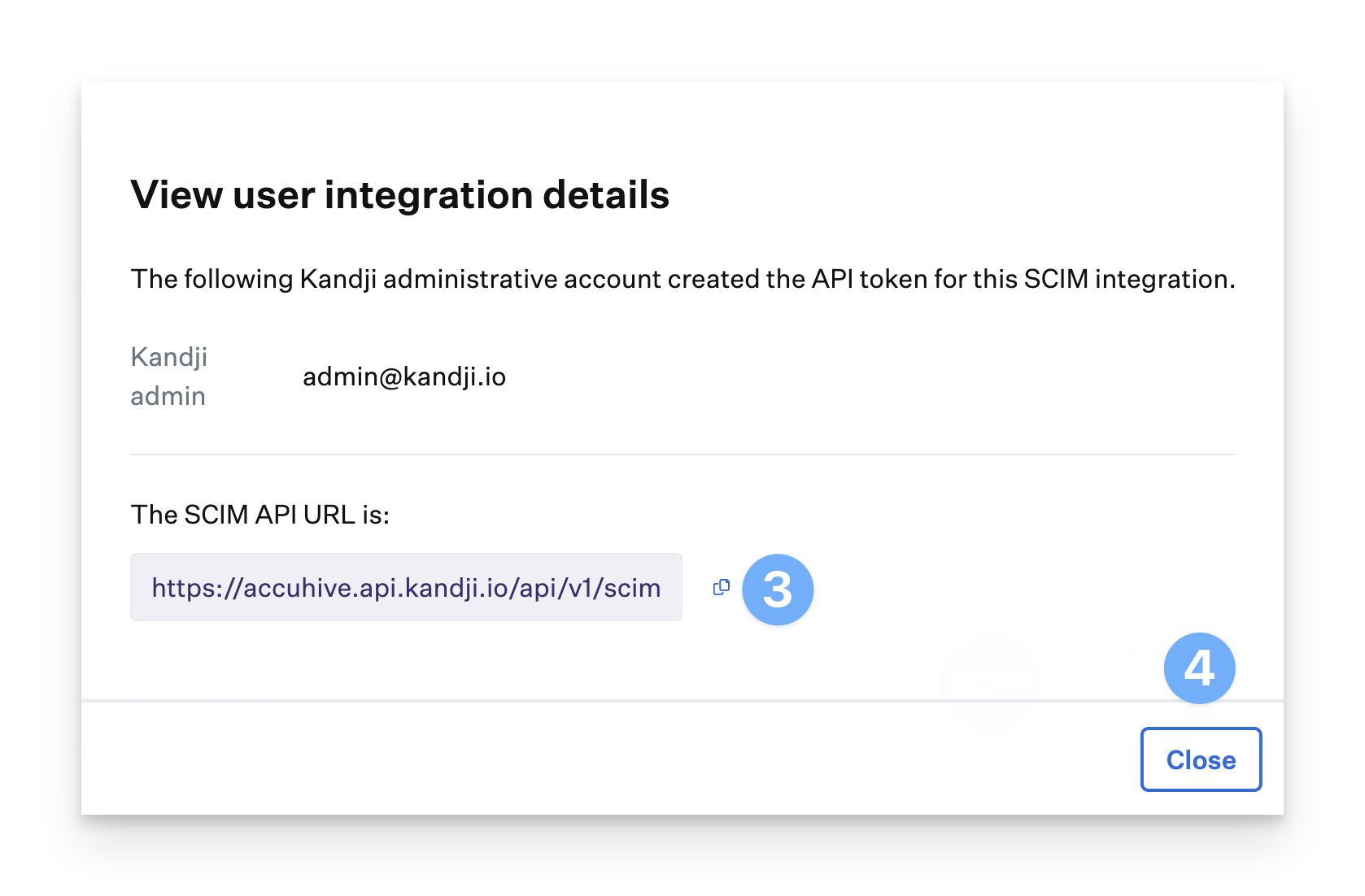
Obtain the SCIM API URL
Your SCIM API URL will be in the format of https://subdomain.api..io/api/v1/scim
Click the ellipse on the SCIM directory integration you just created.
Select View Details.
Copy the SCIM API URL; your identity provider will require this.
Click Close.
SCIM schema and supported attributes
Kandji supports the following SCIM attributes. Refer to these attributes when mapping your SCIM application in your IdP.
Kandji does not use any attributes that are not in the list below. To limit the attributes sent, please modify the attributes configured in the SCIM app in your IdP.
User attributes
Attribute | Description | Required |
|---|---|---|
userName | Unique identifier for the user, used to authenticate to the service provider | Yes |
name.formatted | The user's full name (for example, "John Doe"). This attribute or the displayName attribute is required | No |
displayName | The user's full name (for example, "John Doe"). This attribute or the name.formatted attribute is required | Yes |
title | The user's title, such as "Vice President." | No |
active | The user's status within the identity provider. This attribute is automatically added by the Identity Provider. | Yes |
emails.value | The user's email address as a subattribute of emails. Kandji only stores the first email in the list. | Yes |
department | Identifies the name of a department. | No |
Group attributes
Attribute | Description | Required |
|---|---|---|
displayName | A human-readable name for the Group. | Yes |
members | A list of members in the Group. | Yes |
When using SCIM to sync users from a directory, the SCIM app automatically sends new information to Kandji, so there is no need for a Sync Now button that you would see when using the native Entra ID or Google Workspace directory integrations. Each cloud IdP has its own standard for syncing SCIM data.
Please check with your identity provider's documentation to understand how SCIM sync is configured.
Next Steps
After completing the steps in this article, refer to the IdP-specific article for information on configuring SCIM within your IdP. Below are the currently available IdP support articles. Kandji's SCIM implementation follows the SCIMv2 specification.