Note: Microsoft Entra ID is the new name for Azure AD (Azure Active Directory)
Because client secrets have a maximum life of 24 months, we recommend that you configure SAML based Single Sign-On instead of using the method described in this document.
Create a Microsoft Entra ID Application
Sign in to the Microsoft Entra admin center.
In the left navigation bar, click Applications.
Click App Registrations
Click New Registration to register a new application.
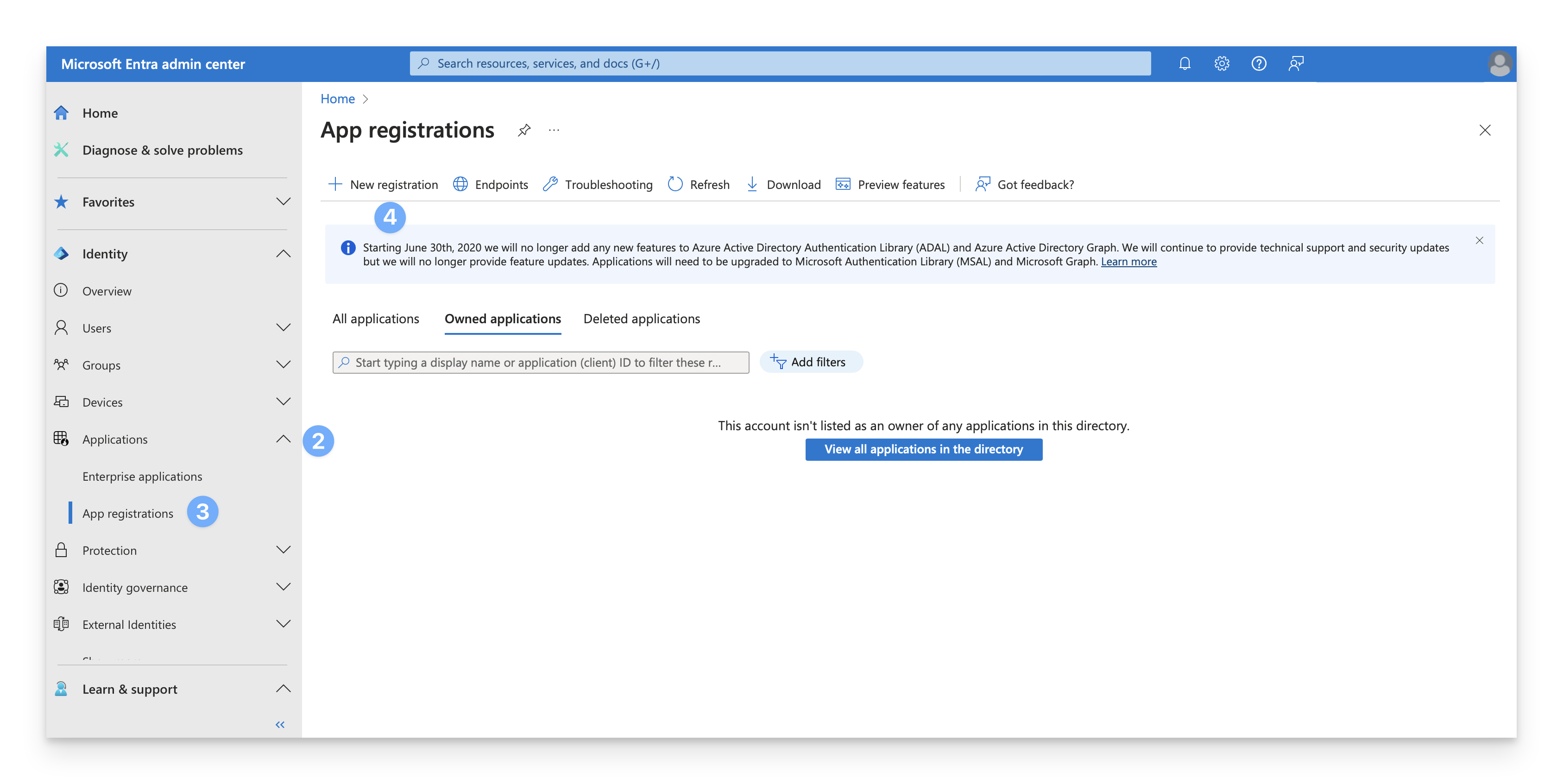
In the Name field, specify a name for the application (such as "Kandji Native SSO").
For "Supported account types," select Accounts in this organizational directory only.
In the Redirect URI field, select Web from the dropdown menu, and enter one of the following values, depending on where your Kandji tenant is hosted.
If your tenant is hosted in the US, use the following URI:
If your tenant is hosted in the EU, use the following URI:
Click Register.
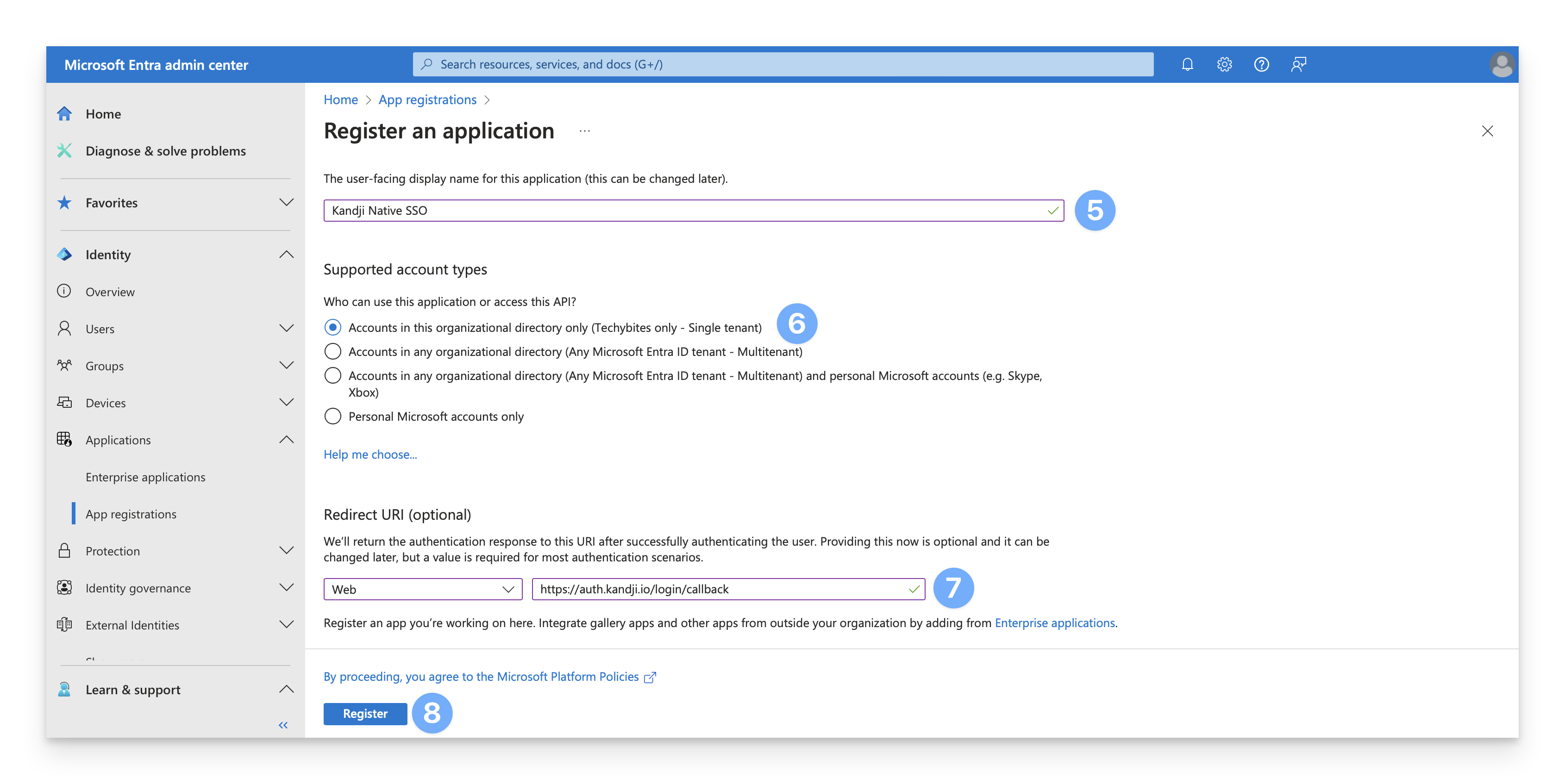
On the new page, copy the Client ID and save this for later.
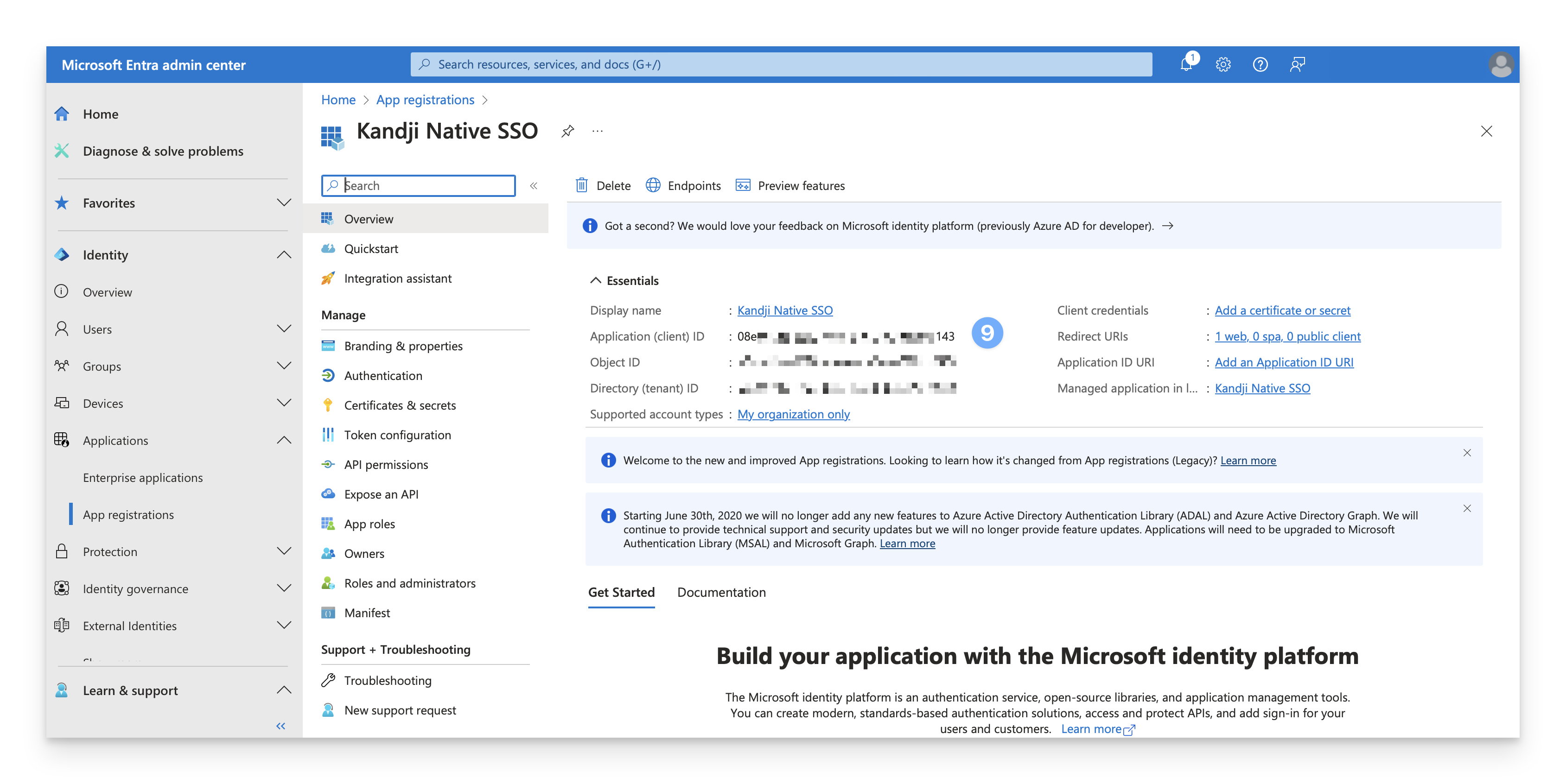
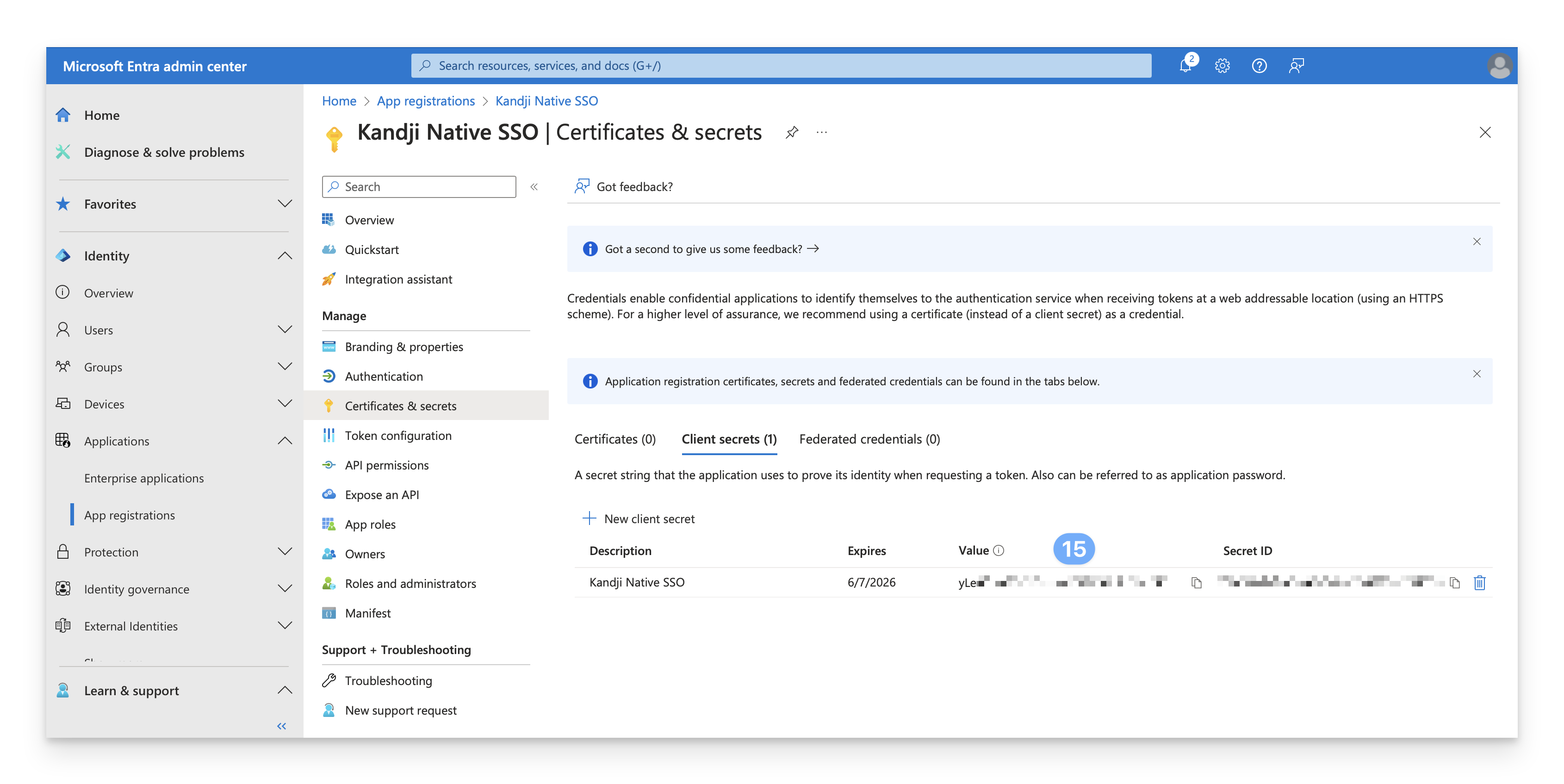
Click Certificates and Secrets.
Click "New client secret."
Give the client secret a name such as "Kandji Native SSO."
Set the expiration to 24 months.
Click Add.
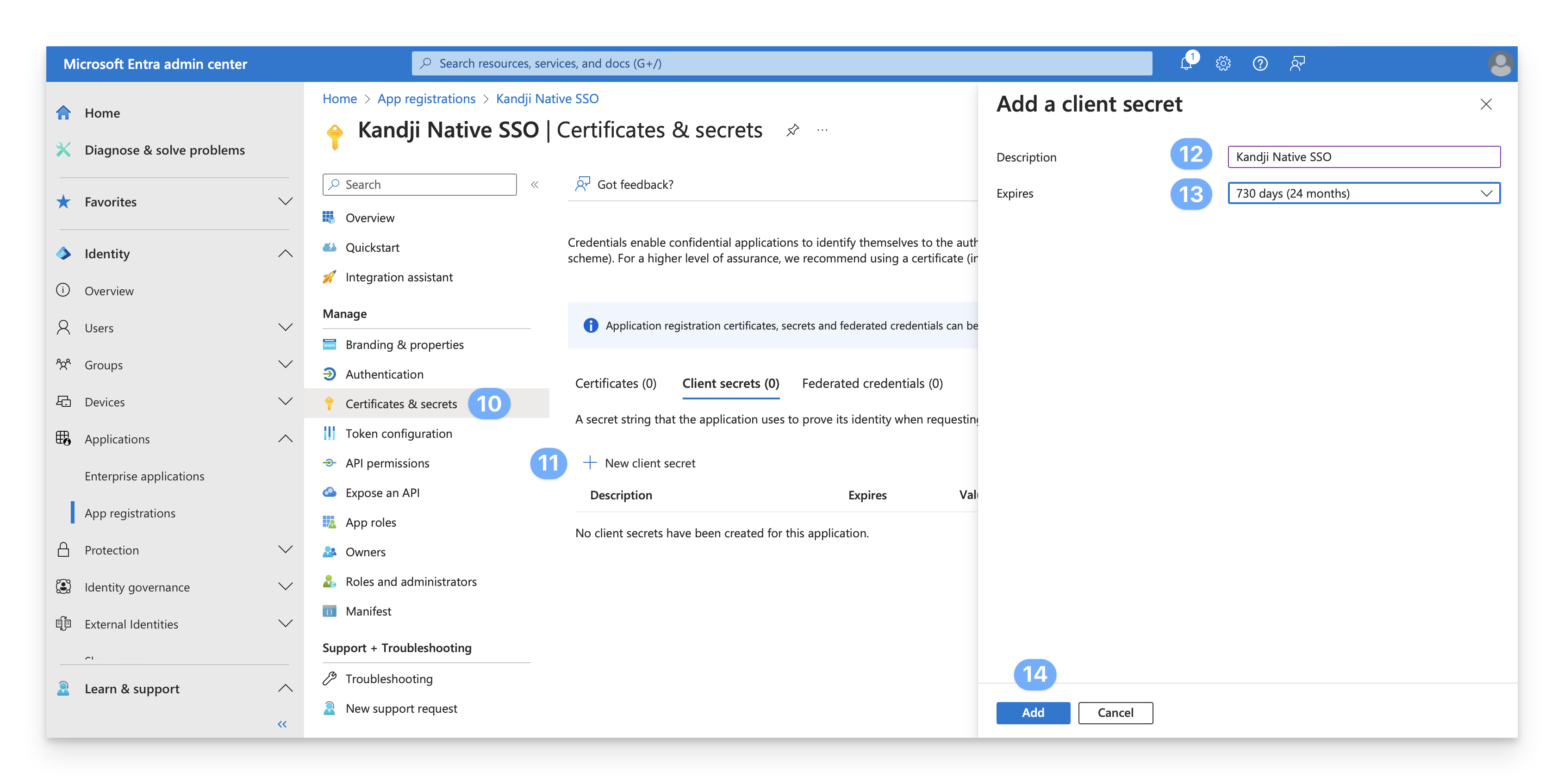
Copy the Value of the client secret, and save this for later. Note that the client secret Value is distinct from the client secret ID.
Create a Microsoft Entra ID Directory Connection
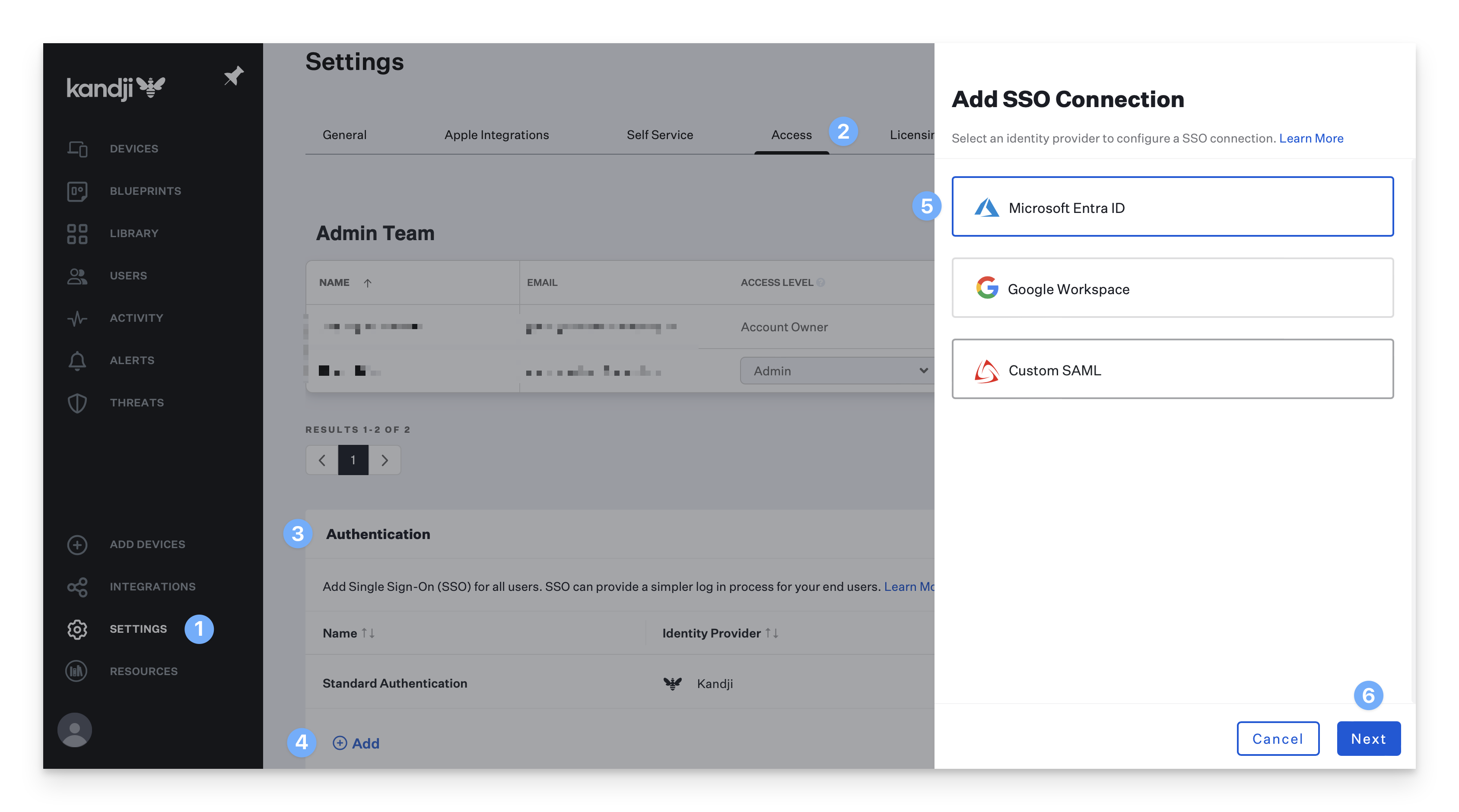
Navigate to the Settings page.
Click the Access tab.
Find the Authentication section. If that section does not currently exist, SSO is not enabled for your tenant.
Click the Add button on the bottom left of the authentication table.
In the new blade, click on the Microsoft Entra ID connection option.
Click Next.
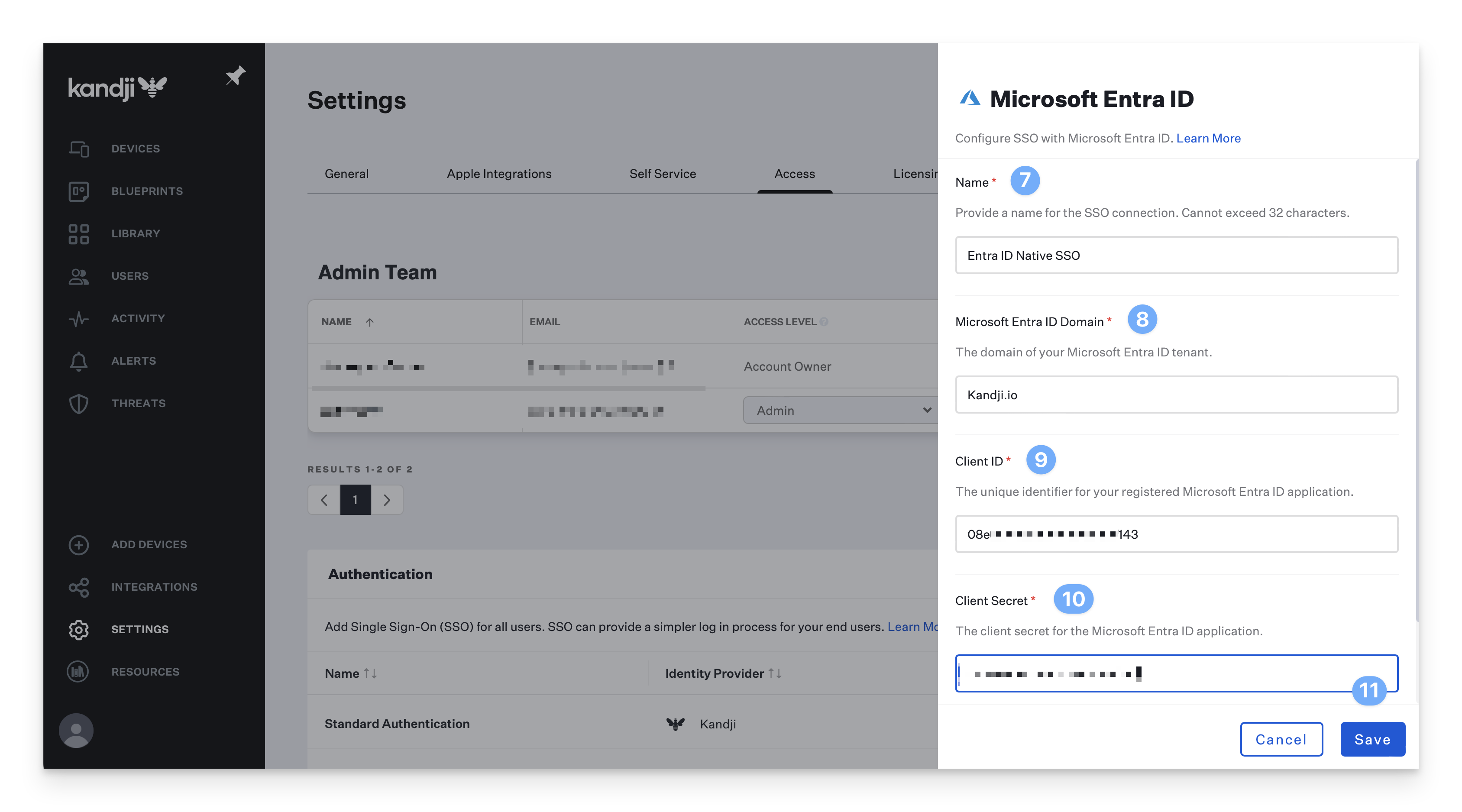
Customize or use the default Name for the Entra connection (this will be shown on the login page).
Enter the Entra ID Directory Domain that the application was registered within. Please refer to Microsoft's documentation to locate your directory domain name.
Enter the Client ID you previously copied from the Entra admin center.
Enter the Client Secret you previously copied from the Entra admin center.
Click Save.
After saving, a new dialogue box will appear with a link to authorize your connection. A Microsoft Entra ID administrator for your domain will need to click the link and complete this process to authorize the application. This box will not go away after authorization is completed.
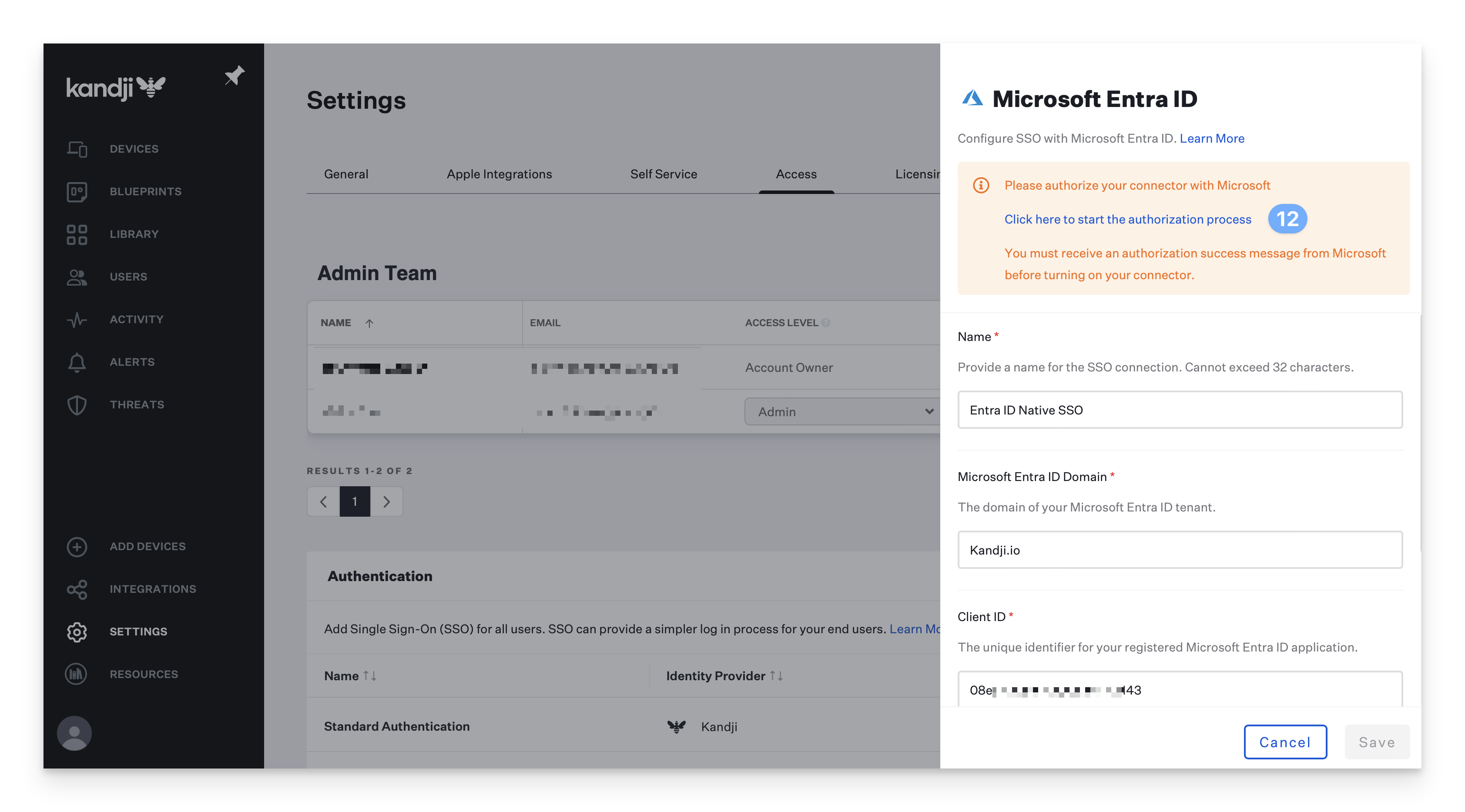
In the new window that launches, sign in and click accept.
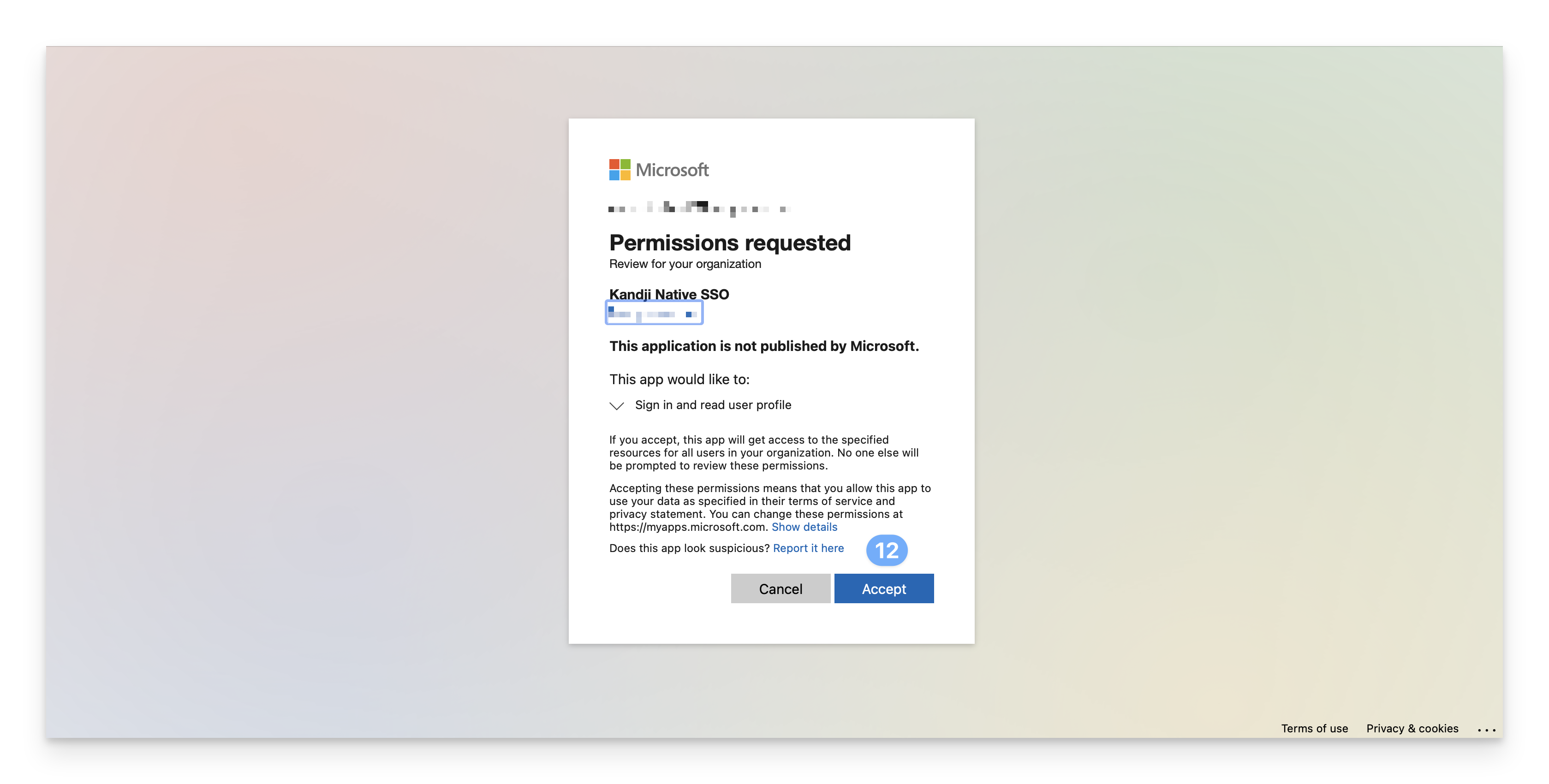
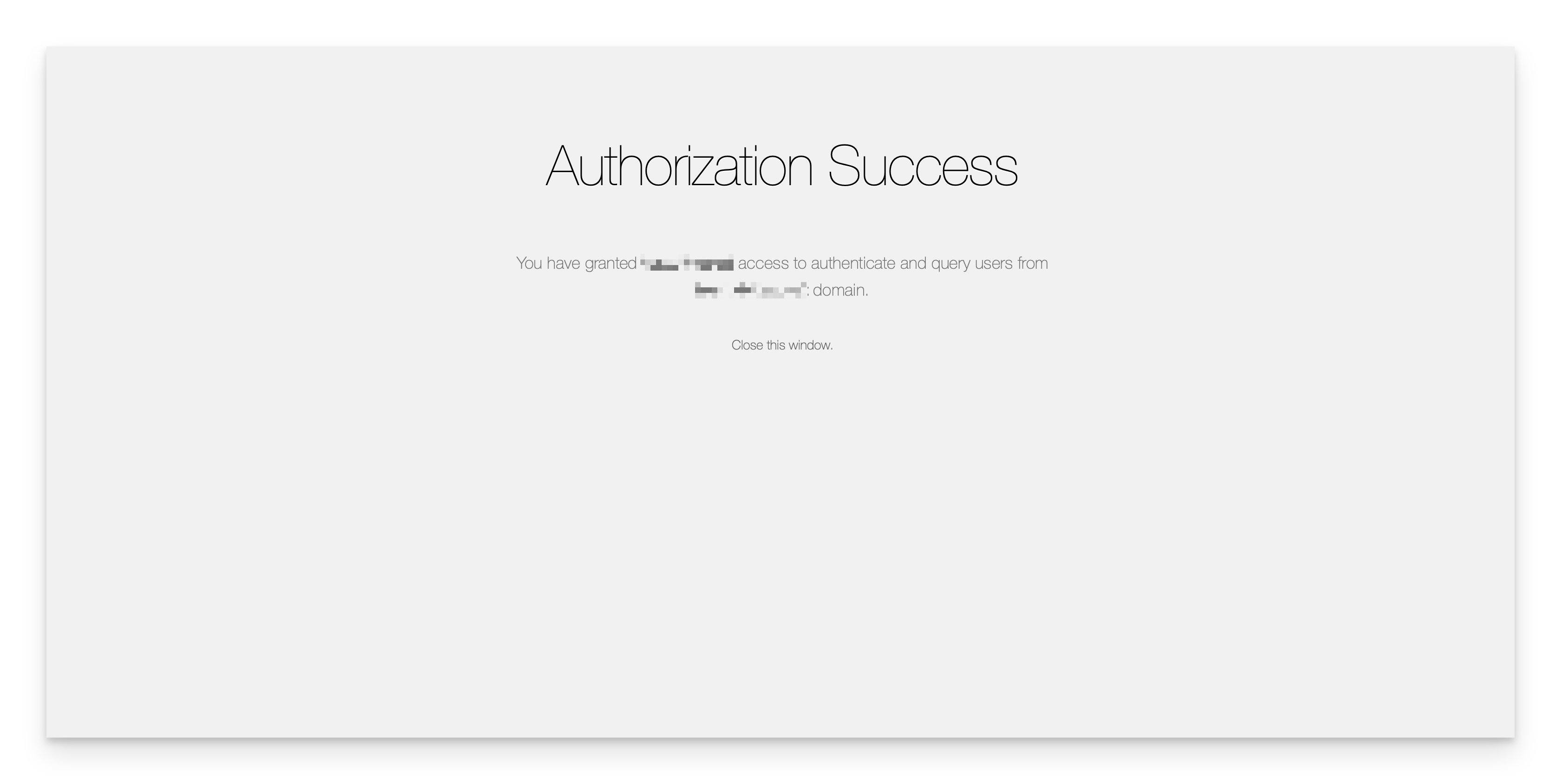
After clicking Accept, you will be brought to an authorization success page.
Your connection has now been successfully configured and may be enabled and tested.
If you encounter the error "Failed to obtain access token," it may be because the secret ID was used instead of the correct value.
Enable the SAML Connection
Once you have configured the SAML connection in Kandji and your identity provider, you can enable it. For step-by-step instructions, please refer to our Single Sign-On support article.
Enforcing Single Sign-On
Once you have configured at least one Single Sign-On connection, you can disable the Standard Authentication connection. Disabling Kandji standard authentication will disable the ability for Kandji administrators in your tenant to authentication via Email/Password, Google Sign in, or Office 365 Sign in. Please refer to our Single Sign-On support article for step-by-step instructions.
Renewing the Client Secret
Follow steps 9-14 in the Create a Microsoft Entra ID Application section of this article to create a new client secret and copy the value as shown in step 14.
In the Kandji web app, navigate to the Settings page.
Click the Access tab.
Find the Authentication section.
Click on the ellipsis next to the SSO integration that was created earlier in this article, and choose Configure.
Replace the Client Secret with the client secret value that was copied earlier.
Click Save.
Be sure to test the configuration by signing into the Kandji web app and choosing the Native SSO login option that was created. You'll want to test this with a private browser window/incognito window and verify that you are able to sign in to the Kandji web app. You can then optionally delete the previous client secret from the App registration in Entra ID.

