What is Require Authentication?
Require Authentication is an enrollment setting that allows administrators to force user authentication through an identity provider (IdP) before proceeding with device enrollment. Administrators can match the authenticated IdP user to a user in their IdP and assign the matched user to the device record automatically.
How Require Authentication Works
After configuring a Single Sign-On (SSO) connection in Kandji and assigning it to an Automated Device Enrollment Library Item or Blueprint on the Enrollment page, users will need to authenticate through an IdP in order to enroll their devices with Kandji. Kandji admins can opt to automatically assign users to device records based on email matches.
For Automated Device Enrollment configurations that require authentication, admins can prefill and lock account details during setup.
Prerequisites
A working SSO configuration in Settings > Access.
Configuring Require Authentication with Automated Device Enrollment
Navigate to Library in the left-hand navigation bar.
Click Add New on the top-right, and choose Accessory & Storage Access.
Click Add & Configure.
Give the new Automated Device Enrollment Library Item a Name.
Assign to your desired Assignment Maps or Classic Blueprints.
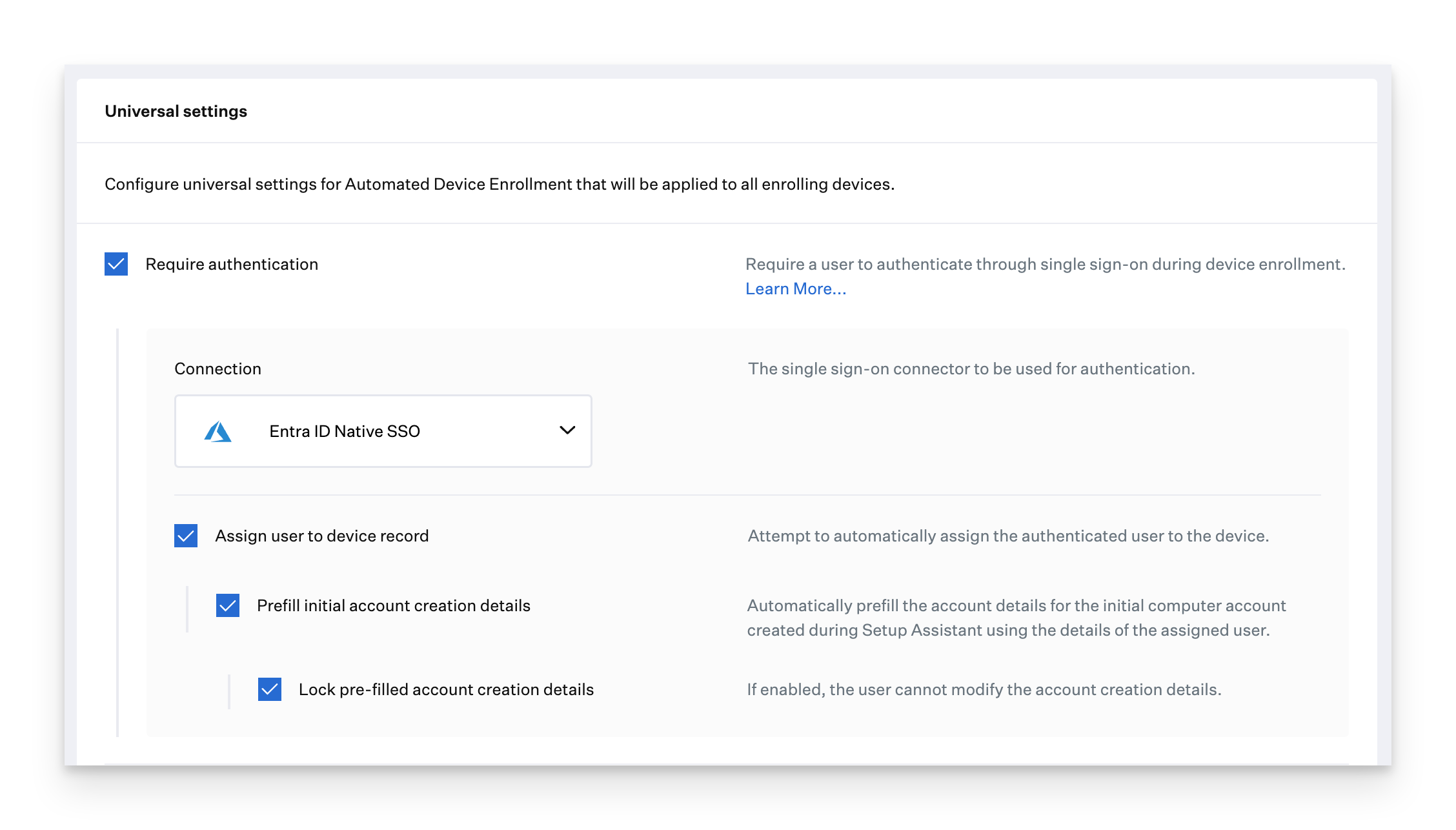
Check the box for Require Authentication.
Select an SSO Connection.
Optionally, Assign user to device record.
Enabling this option will attempt to match the user authenticated by the identity provider to a user that exists in your user directory integration(s). If the authenticated IdP user's email address matches the email address in your integrated directory, the user will be assigned to the device.
To prepopulate your user's initial account information to match your IdP, select Prefill primary account details.
To ensure that your user cannot change their initial account information, select Lock primary account details.
Configure the rest of your Automated Device Enrollment Library Item as desired, and click Save.
Configuring Require Authentication with Manual Enrollment
Select Enrollment in the navigation bar.
Navigate to the Manual Enrollment tab.
Scroll down to your desired Blueprint and check the box for Require Authentication.
If desired, check the box to Assign user to device record.
Enabling this option will attempt to match the user authenticated by the identity provider to a user that exists in your user directory integration(s). If the authenticated IdP user's email address matches the email address in your integrated directory, the user will be assigned to the device.
.png)
Considerations
If you are also deploying Passport, you must deselect the Prefill initial account creation details and Lock prefilled account creation details options. Using the prefill and lock settings while skipping account creation, as recommended with Passport, will cause account creation conflict and result in a Setup Assistant error that requires the Mac to be erased.
If requiring authentication and using Google Workspace as your identity provider, the Single Sign-On entry must be created using Custom SAML, as the built-in Google Workspace integration will result in a 403 error upon enrollment.
An SSO connection does not need to be Active in Settings > Access to Require Authentication within Automated Device Enrollment or Manual Enrollment. A connection should only be Active in settings if you want to authenticate Kandji administrators to the web app with that connection.
The selected authentication connection is the SSO connection used to authenticate the user. Any user assigned to the "Application" within the Identity Provider can complete the enrollment.
You can use the same connection (generally referred to as an application within the identity provider) that you use for your Kandji Team Members to authenticate into your Kandji tenant or configure an entirely new connection/application within Kandji and your identity provider specifically for device enrollment.
If you elect to use the same connection/application, please note that your end users may see the Kandji application within your identity provider's application catalog. Assigning users to the application will not grant them administrative rights in Kandji.
