The Endpoint Detection and Response add-on is required to use the Accessory & Storage Access Library Item. However, you do not need to assign the Avert Library Item to the Blueprint in order to deploy the Accessory & Storage Access Library Item.
What is Kandji EDR?
Kandji EDR is a security tool that monitors Mac computers for malware and potentially unwanted programs (PUPs) using file-based and behavioral detection mechanisms. It's integrated into the Kandji platform and managed through the same web app you use for device management.
How Does EDR Work?
EDR runs on enrolled Mac computers using Apple's Endpoint Security framework. It analyzes files and processes against threat intelligence and detection models to identify suspicious activity. EDR uses Apple's native frameworks for monitoring without significant performance impact.
EDR is deployed as a library item called Avert in Kandji Blueprints. Once you enable it in a Blueprint, it deploys and activates automatically on enrolled devices.When EDR detects a threat, it can terminate the process and quarantine the file. You can configure these response actions and create custom allow/block lists based on file hashes or paths.
Admins can detected threats, quarantine actions, and security events in the Kandji web app's Threats page.
Threats Page
You can access the Threats page by clicking Threats in the left-hand navigation bar of the Kandji web app. This page lists the total number of Threat events affecting your Mac computers across the designated Blueprints containing the Avert Library Item, along with information such as device impacted, threat name, classification, the process responsible for the Threat event, detection date, and threat status. Kandji EDR categorizes file detections as malware, PUPs, benign, or unknown and behavioral detections as malicious or suspicious.
Threats over time
The Threats over Time graph displays a chronological overview of security threats detected by Kandji EDR within a specified timeframe. By default, the graph shows data for the past 30 days, but you can adjust this period using the dropdown menu above the graph to view anywhere from 24 hours up to 90 days. For more specific analysis, you can select a custom date range.
If you choose a date range exceeding 90 days, the system will automatically limit the display to 90 days.
The graph also offers three visualization options to control the level of detail displayed:
Granular - Shows every individual threat detection, providing the most detailed view
Smooth - Displays general trends and patterns, offering a high-level overview
Balanced - The default setting that provides a middle ground between detailed detection data and trend visualization
These granularity options allow you to customize the graph based on whether you need to examine specific incidents or understand broader threat patterns over time.
Devices Under Threat
The Devices under threat metric shows how many devices currently have active security threats. If a device has any threats detected (whether file-based or behavioral) it gets counted here. You can adjust the timeframe for this data using the date filter, just like with other dashboard elements. This data is refreshed every time the page is refreshed.
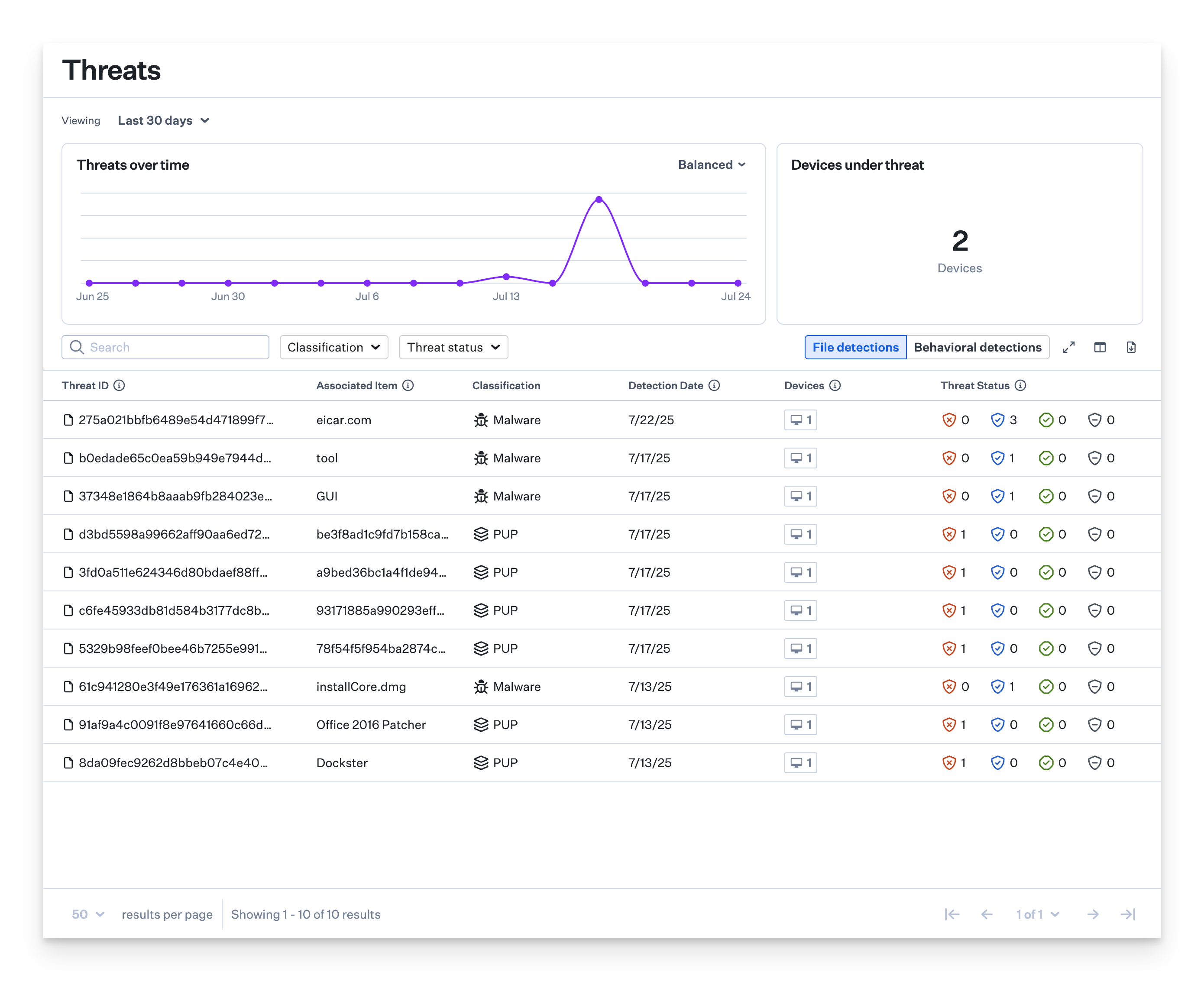
The Threats page also provides quick filters by classification and threat status.
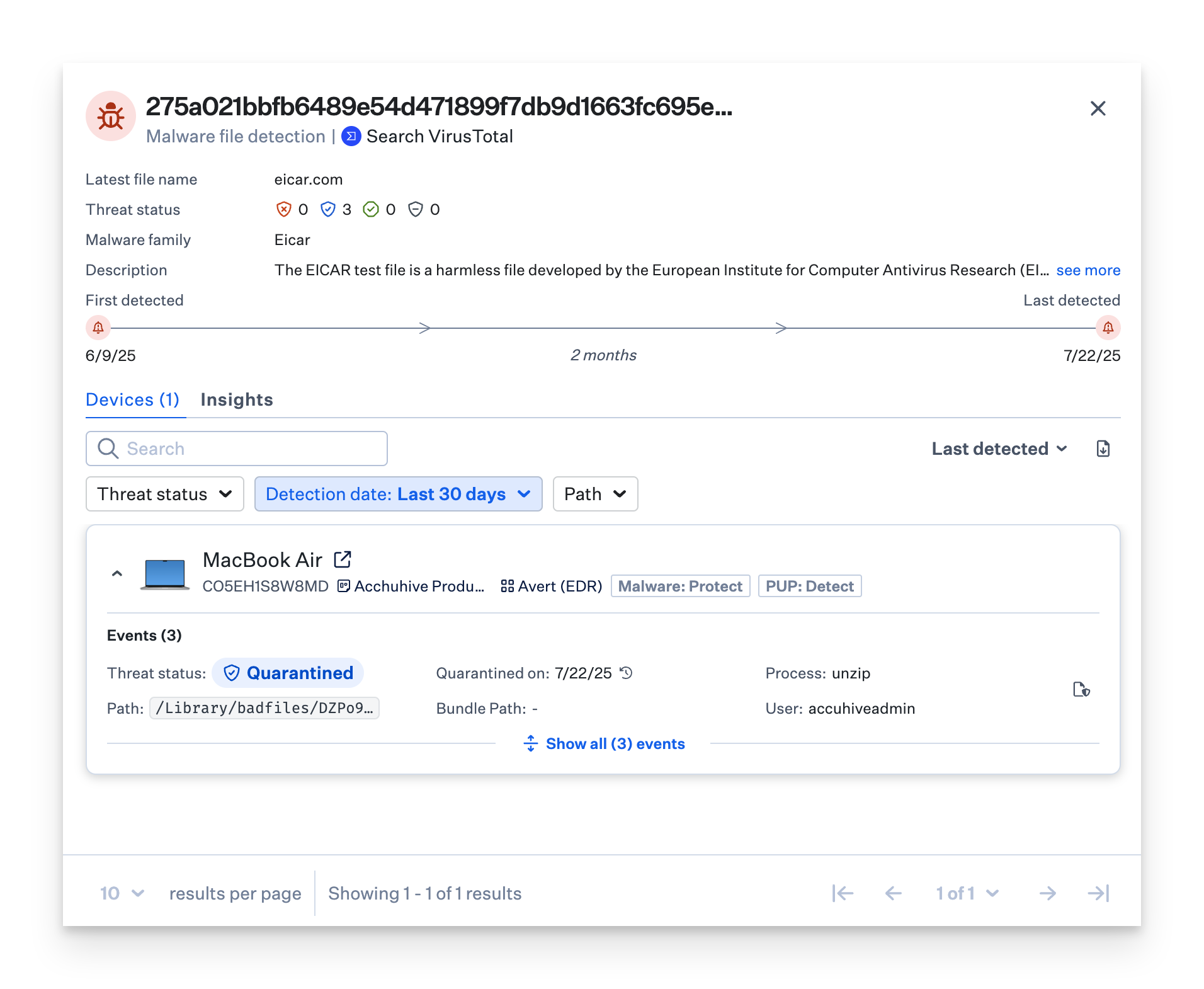
Threat Detail View
Click on any Threat event to reveal additional information, including detection and quarantined dates, path, file hash, and user information. Similar data is available on the device record page for individual devices.
Device Record Page
The device record page shows the total number of threat events found on a specific device. To see the actual threat events, select the Threats tab.
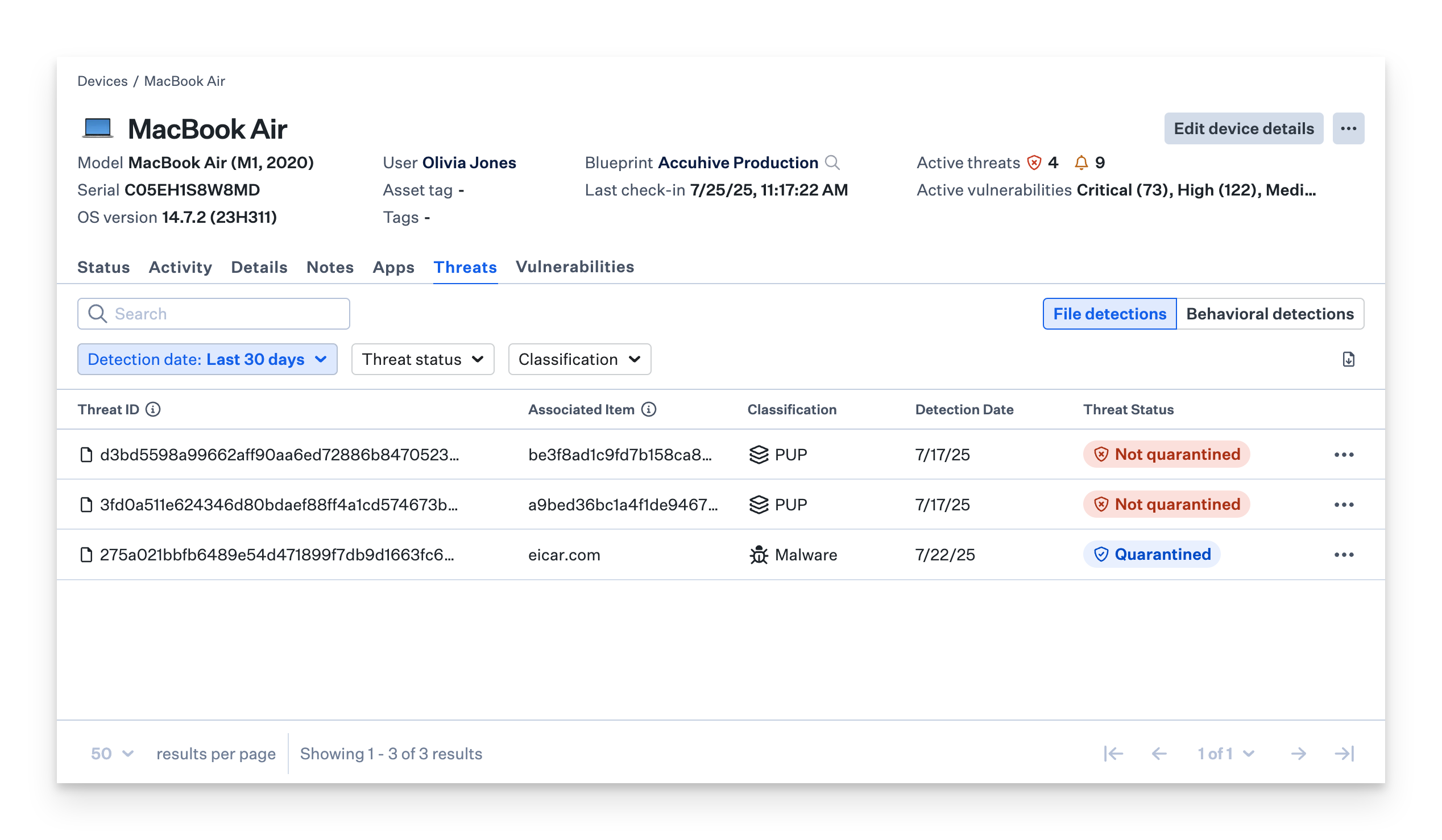
Select any threat entry to display comprehensive details including detection timestamp, quarantine date, file location, cryptographic hash, and related user account information.
.png)
For more details about how device views work, check out the Device Views Overview support article.