This integration pushes event data to your specified S3 bucket using cross-account access via a Kandji-provided IAM role, enabling centralized activity collection and analysis.
What is the Amazon S3 Activity Log Integration?
The Amazon S3 Activity Log Integration enables organizations to send tenant activity events to a self-hosted S3 bucket to share with SIEM services. This integration provides a straightforward way to collect and store Kandji activity log events without manual intervention.
Once configured, it automatically captures Kandji tenant activity events and delivers them to your specified bucket, where you can access them for monitoring, compliance, or analysis purposes. Refer to our activity log API documentation for a list of logged events.
How does the Amazon S3 Activity Log Integration Work?
Once configured, event data is sent to your designated S3 bucket using cross-account access through a Kandji-provided IAM role, allowing for centralized collection and analysis of activity logs.
The first log collection after the Integration is connected only includes the previous hour of activity. Subsequent activity log collection will occur hourly.
Prerequisites
Before configuring this integration, ensure the following:
You have an active AWS account.
You have permissions to create a new S3 bucket.
You have permissions to create an IAM Role with AssumeRole and S3 write permissions.
Steps to Configure AWS Access
Kandji Integration
Navigate to Integrations in the left-hand navigation bar.
Click Discover integrations in the upper-right of the Integrations page.
Under Security integrations, click Add and configure under Amazon S3 Activity Log Integration.
Copy the value for KANDJI_IAM_ROLE and store the value in a secure location.
Copy the value for KANDJI_AWS_ACCOUNT_ID and store the value in a secure location.
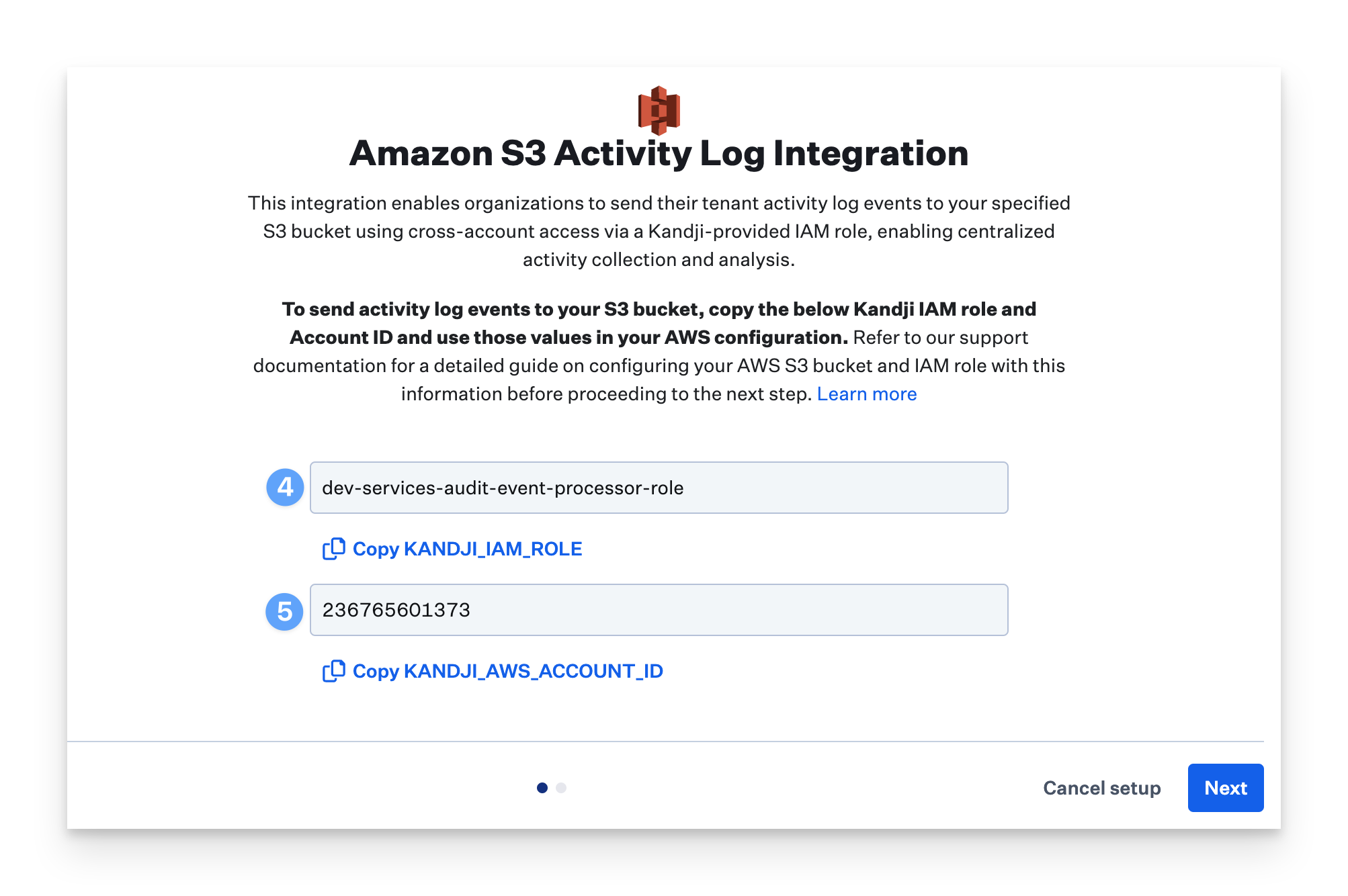
These values will be used as part of your IAM role permissions in the next section.
Create S3 Bucket
You must create a new S3 Bucket to use the Amazon S3 Activity Log Integration.
Log in to AWS.
Navigate to Amazon S3 > Buckets.
Click Create bucket.
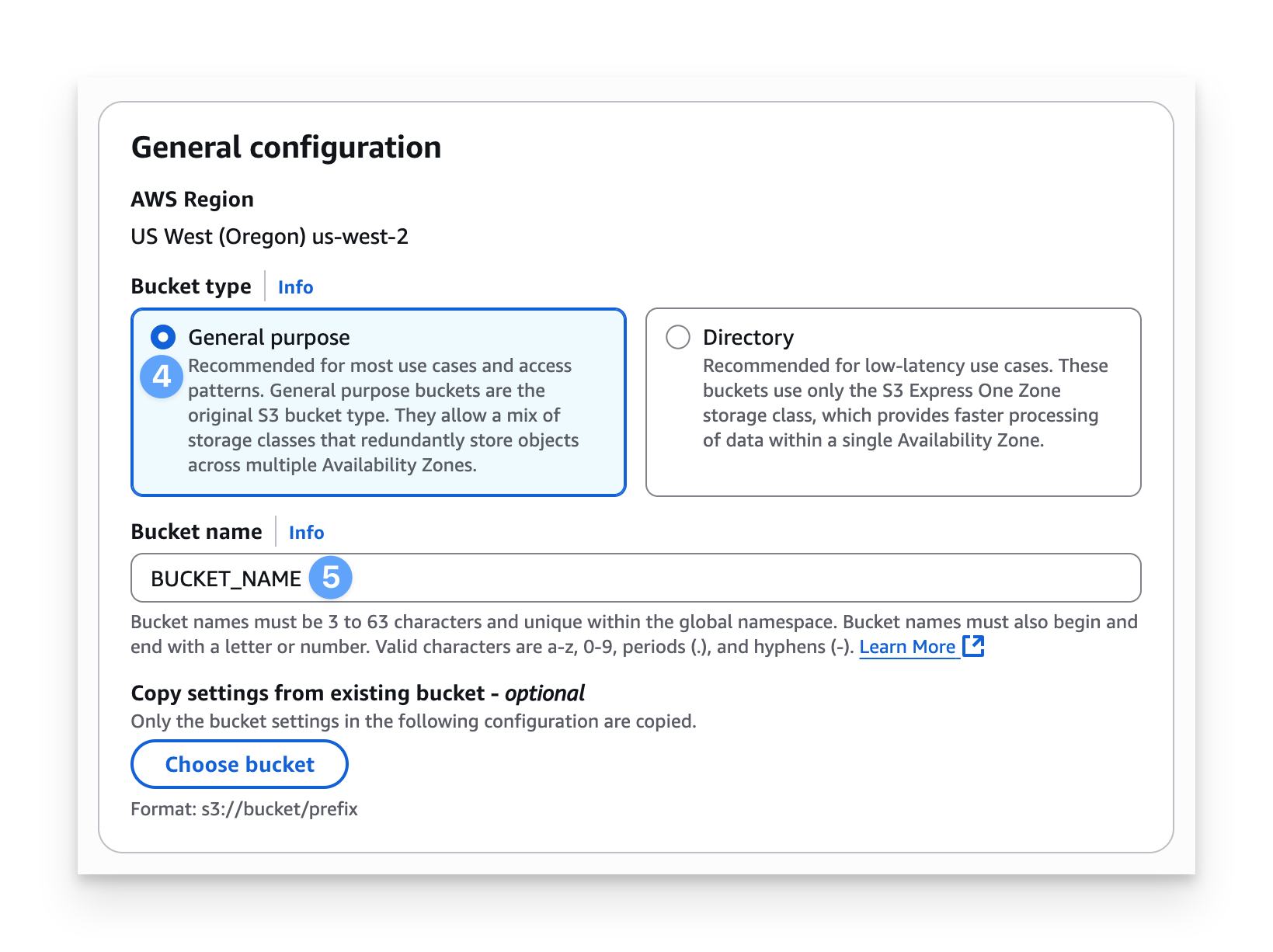
Choose the General purpose bucket type.
Enter a memorable Bucket name.
This name will be referenced in policies.
Under Block Public Access settings for this bucket, ensure that the Block all public access option is selected.
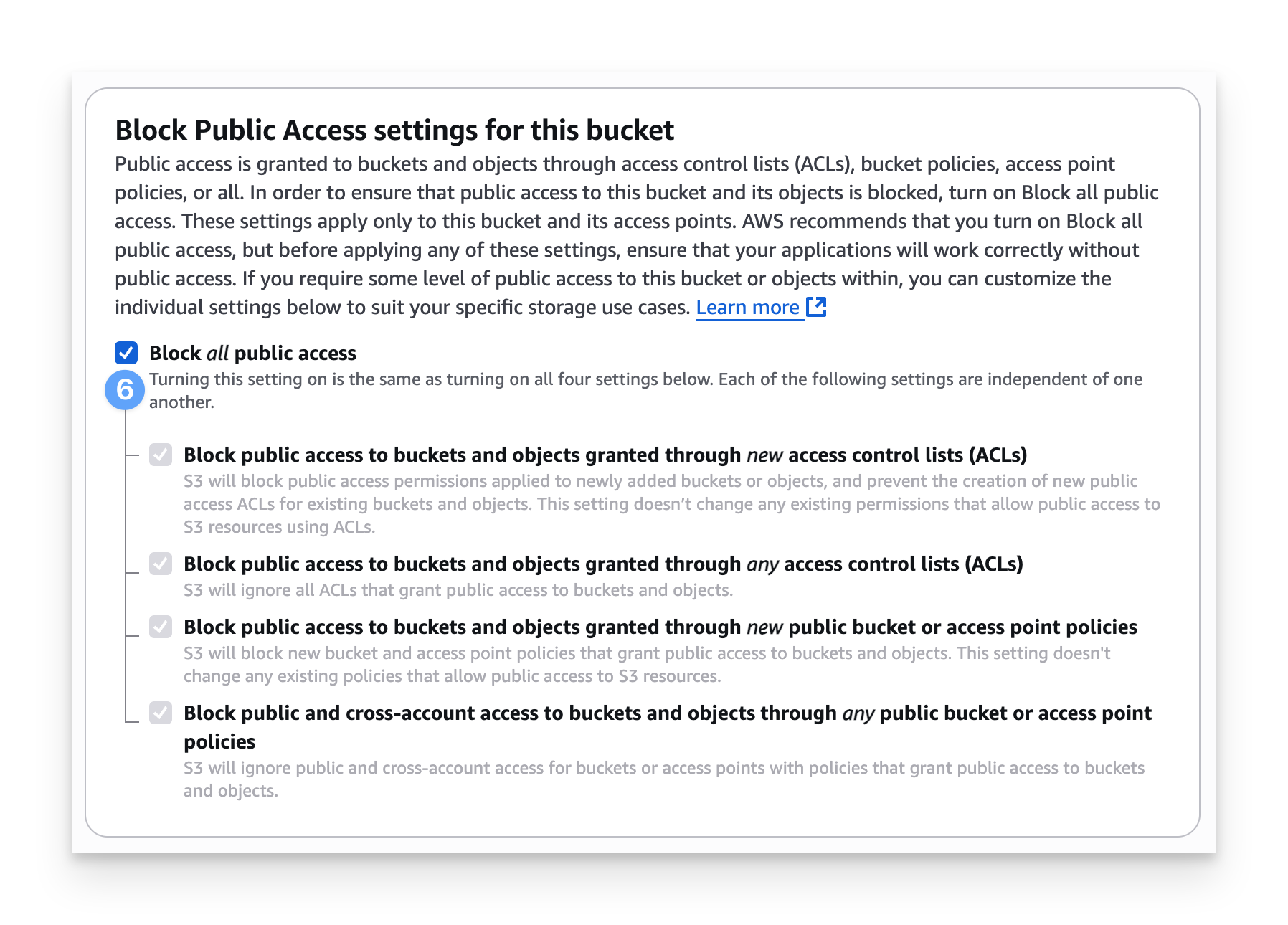
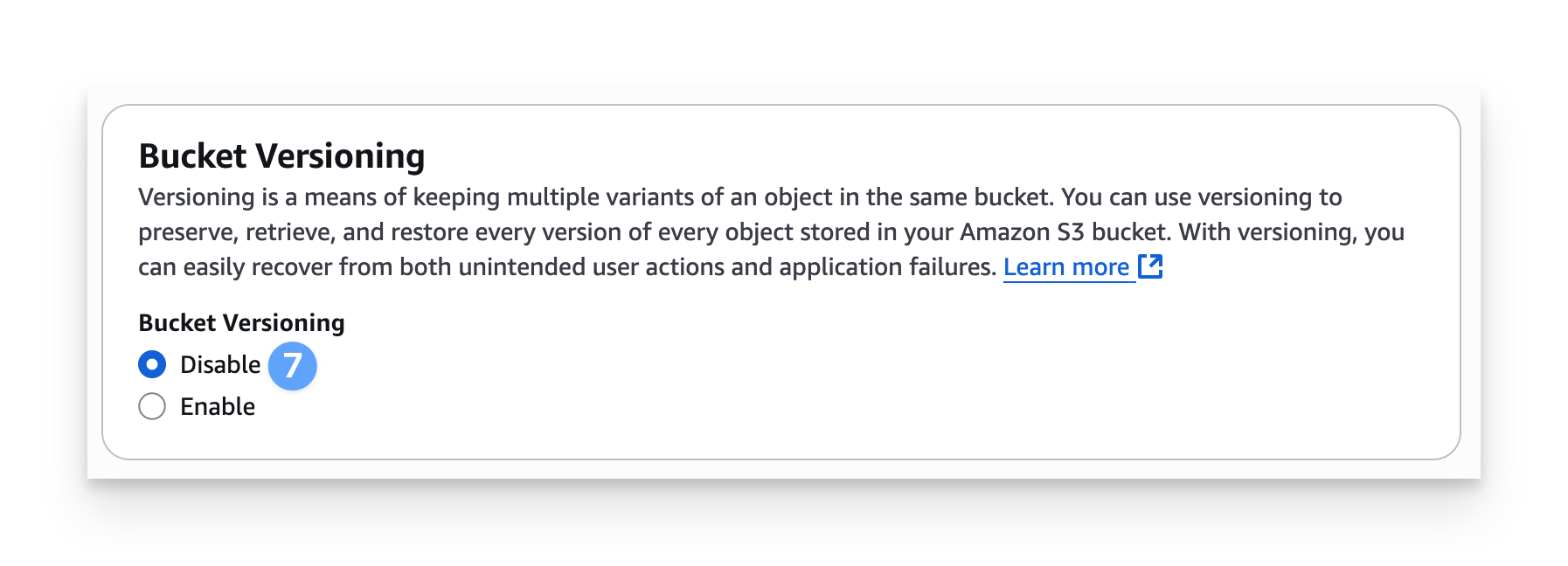
Under Bucket Versioning, keep the Disable option selected.
Under Encryption type, select Server side encryption with Amazon S3 managed Keys (SSE-S3).
Under Bucket Key, select Enabled.
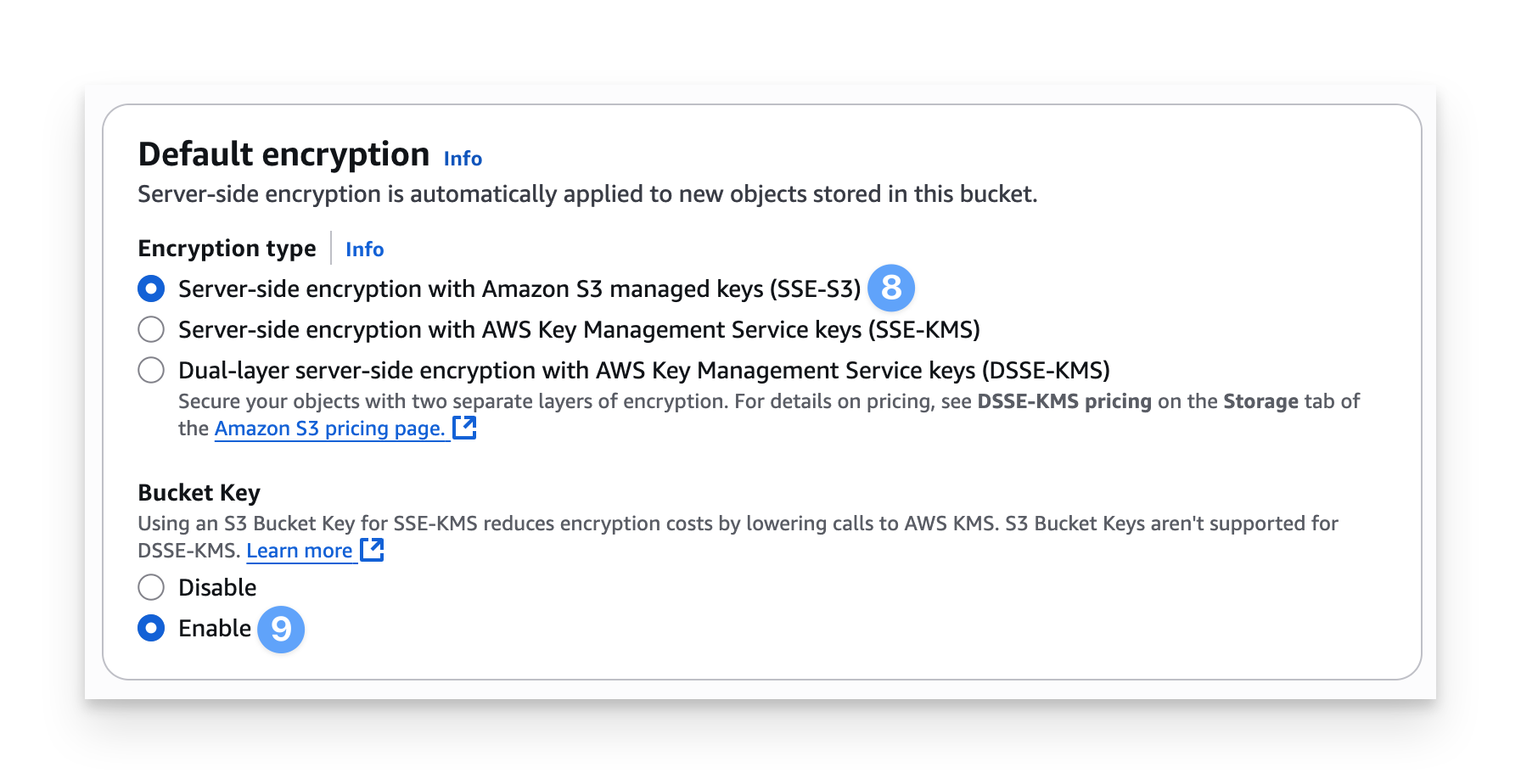
Kandji currently only supports the default encryption options defined above.
Click Create bucket.
Select the bucket you just created.
Click the Permissions tab.
Under Bucket policy, click Edit.
Add the following bucket policy to the role permissions. Click Save changes.
Replace all reference to BUCKET_NAME with the name of the bucket you just created.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowSSLRequestsOnly", "Effect": "Deny", "Principal": "*", "Action": "s3:*", "Resource": [ "arn:aws:s3:::BUCKET_NAME/*", "arn:aws:s3:::BUCKET_NAME" ], "Condition": { "Bool": { "aws:SecureTransport": "false" } } } ] }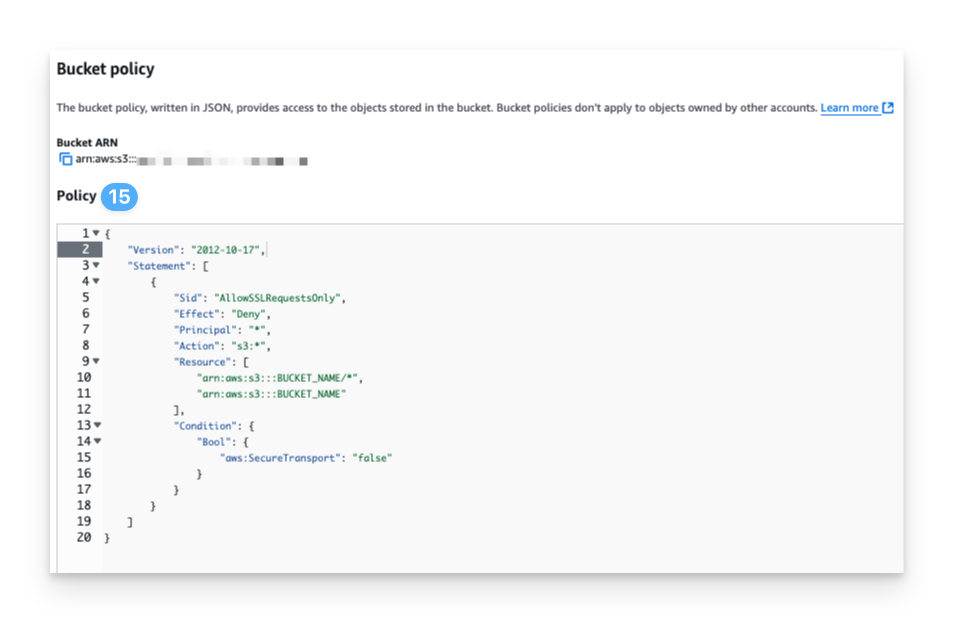
In AWS, navigate to IAM > Roles.
Click Create role.
Select Custom trust policy.
Add the Custom trust policy below to allow Kandji to assume this role when writing to your S3 bucket.
Replace the KANDJI_AWS_ACCOUNT_ID and KANDJI_IAM_ROLE text with the values you made a note of at the beginning of the article.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::KANDJI_AWS_ACCOUNT_ID:role/KANDJI_IAM_ROLE" }, "Action": "sts:AssumeRole" } ] }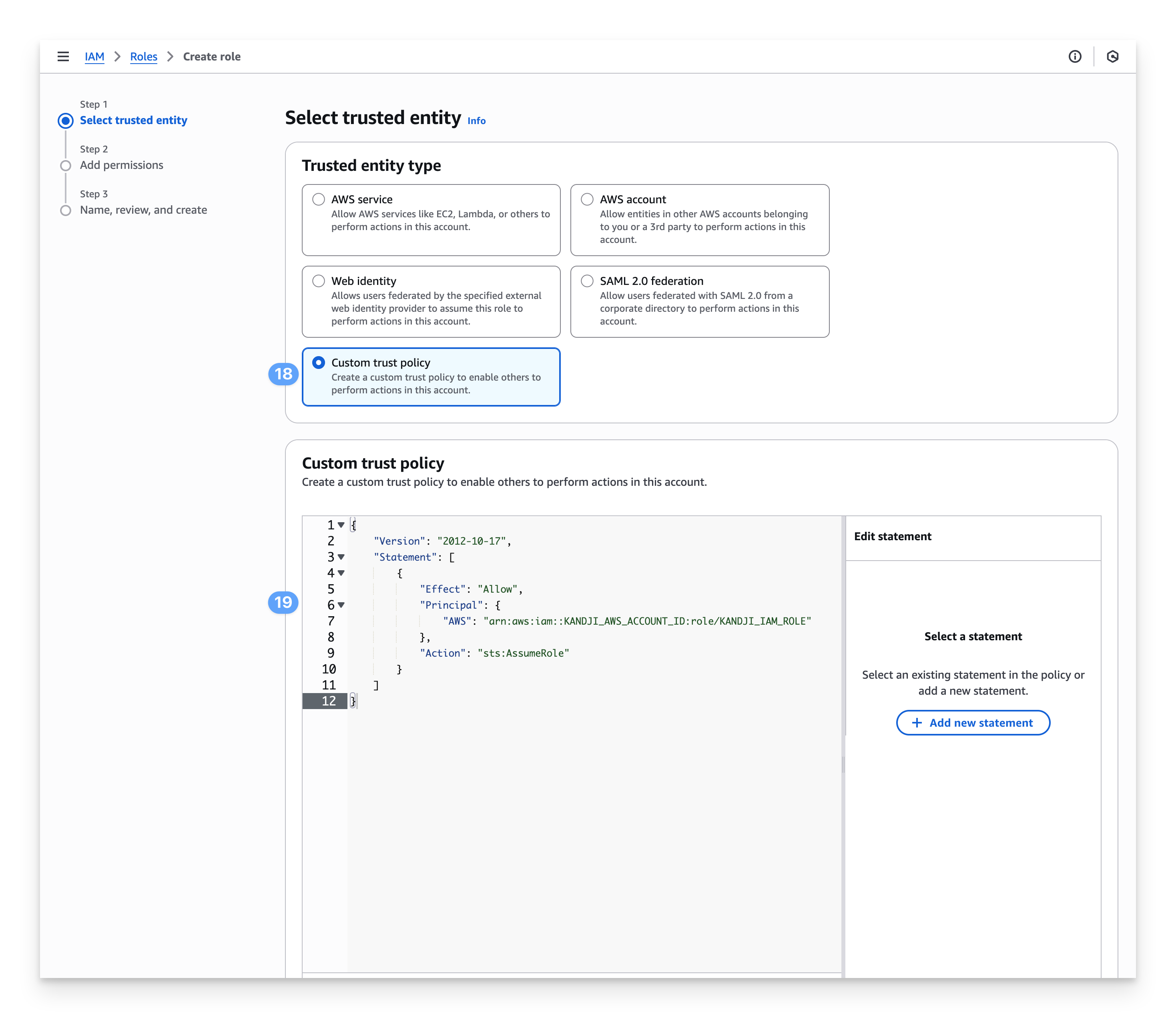
Click Next.
On the Add permissions screen, select Next without selecting any of the listed Permissions policies.
Add a Role name and Description.
.png)
Click Create role.
Select the IAM Role you just created.
Click on the Permissions tab.
Click Add permissions.
Click Create inline policy.
Click the JSON tab.
Enter the following for the inline policy:
Replace BUCKET_NAME - replace this with the name of the bucket you created that Kandji will place the activity log files in.
{ "Version": "2012-10-17", "Statement": [ { "Action": "s3:ListBucket", "Effect": "Allow", "Resource": "arn:aws:s3:::BUCKET_NAME" }, { "Action": "s3:*", "Effect": "Allow", "Resource": "arn:aws:s3:::BUCKET_NAME/*" } ] }
Click Next.
Enter a Policy name.
Click Create policy.
Steps to Set up the Amazon S3 Activity Log Integration in Kandji
Once the above is configured in your AWS account, you can proceed to setting up the integration in your Kandji account.
Navigate to Integrations in the left-hand navigation bar.
Click Discover integrations in the upper-right of the Integrations page.
Under Security integrations, click Add and configure under Amazon S3 Activity Log Integration.

Click Next.
Enter the AWS Account ID.
Enter the S3 Bucket Name for the bucket that was created earlier in this guide.
Optionally, enter a Destination Path.
Enter the IAM Role ARN for the IAM Role that was created earlier in this guide.
Enter the AWS Region.
Click Connect to S3.
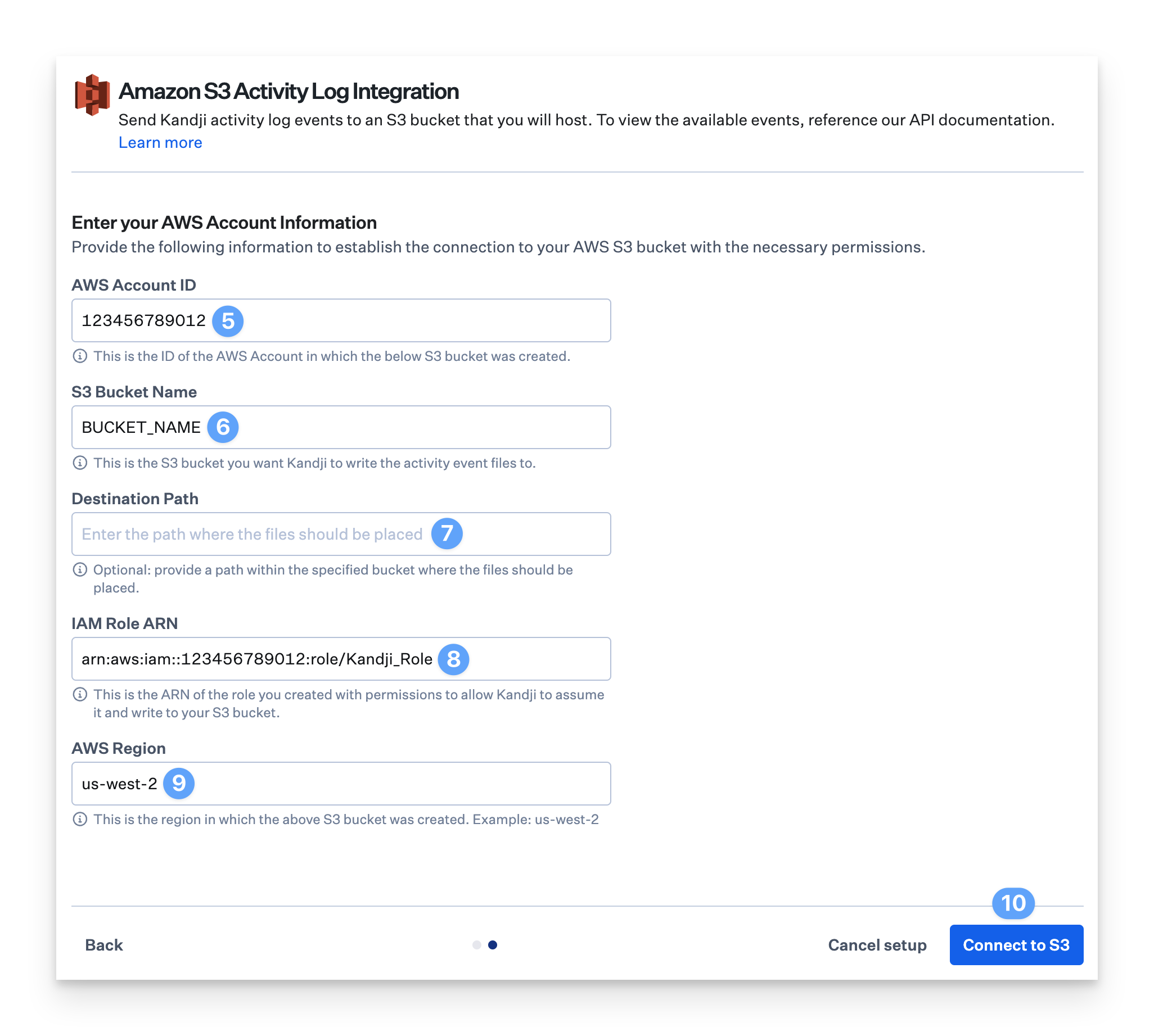
Kandji will attempt to upload and delete a test file in the provided S3 bucket. If Kandji is unable to successfully integrate to your S3 bucket, you will not be able to save and will need to follow the error messages surfaced in the UI to fix the connection.
Verify Event Data in the S3 Bucket.
Check your S3 bucket to confirm that Kandji is pushing event data. This will take a maximum of two hours, provided that activity events have been generated.
Considerations
Activity log events are updated hourly.
The IAM role must have the necessary permissions to allow Kandji to assume that role.
You may need to adjust the S3 Bucket policy to allow Kandji to write objects to the bucket.