What are Identity Certificates?
In 802.1X authentication, identity certificates play a crucial role in ensuring security. They are particularly significant in the EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) method. EAP-TLS utilizes digital certificates to authenticate both the client (supplicant) and the server (authentication server). This mutual authentication guarantees that both parties trust each other's identity before establishing a secure connection.
Identity certificates can be used in both the Wi-Fi Library Item and Ethernet Library Item.
Configure an Identity Certificate
Certain types of authentication require or allow you to specify an identity certificate to verify the device’s identity. These certificates can come from various sources. For network authentication, make sure the identity certificates include the Client Authentication entitlement in their Extended Key Usage (EKU). Work with your network administrator to ensure the certificate service and templates are properly configured for your network.
Obtain an Identity using AD CS
You can obtain identity certificates using Microsoft Active Directory Certificate Services (AD CS).
To deploy AD CS certificates via Kandji, the AD CS Integration must first be configured.
If you wish to have the client device acquire an identity certificate from AD CS, choose AD CS Certificate for Identity certificate.
Click Configure AD CS Certificate. A drawer opens to allow you to configure AD CS options.
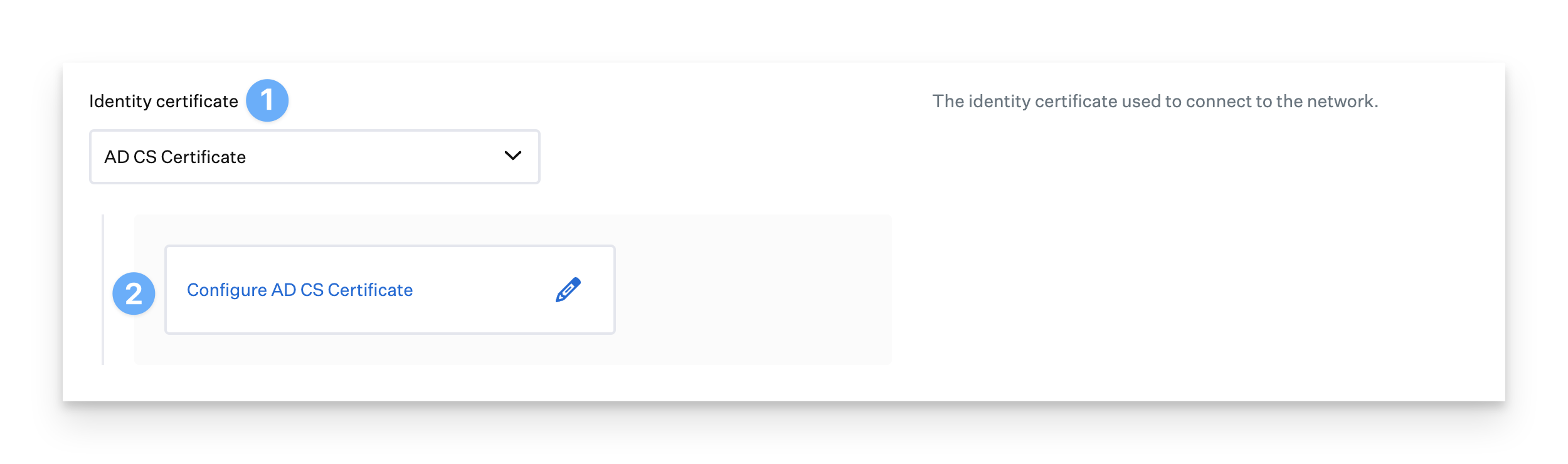
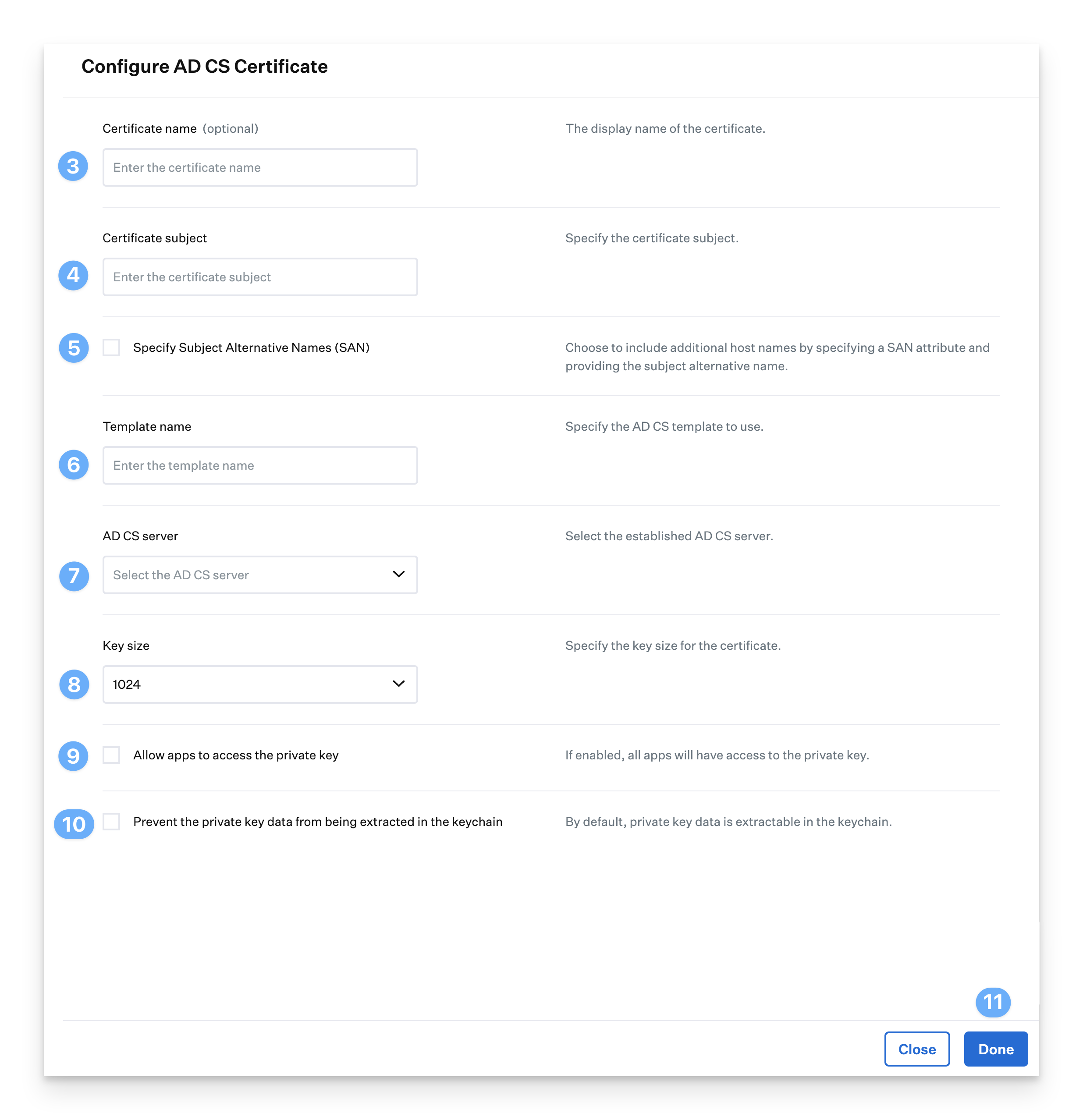
Enter a Certificate name. This will appear on the configuration profile shown in System Preferences.
Enter a Certificate subject. The Certificate subject is typically used to identify the device within the Certificate Authority. It can be anything you like, such as the global variable $SERIAL_NUMBER. The device serial number will be inserted into the profile before being sent to the device using the $ SERIAL_NUMBER global variable.
Optionally, if your environment requires it, you can Specify additional Subject Alternative Names (SAN) to be sent in the request.
Enter a Template name. This is the name of the AD CS computer certificate template used to generate AD CS certificates.
Select an AD CS server from the drop-down menu. AD CS servers are added during the setup of the AD CS integration.
Select a Key size for the certificate.
Select Allow apps to access the private key if you want to automatically allow all apps to access and use the certificate identity’s private key.
Select Prevent the private key data from being extracted from the keychain to prevent the certificate and keys from being exported out of the keychain on the device.
Click Done.
Obtain an Identity using SCEP
Using the Simple Certificate Enrollment Protocol (SCEP), you can obtain identity certificates.
If you wish to have the client device acquire an identity certificate from a SCEP service, choose SCEP for an Identity certificate.
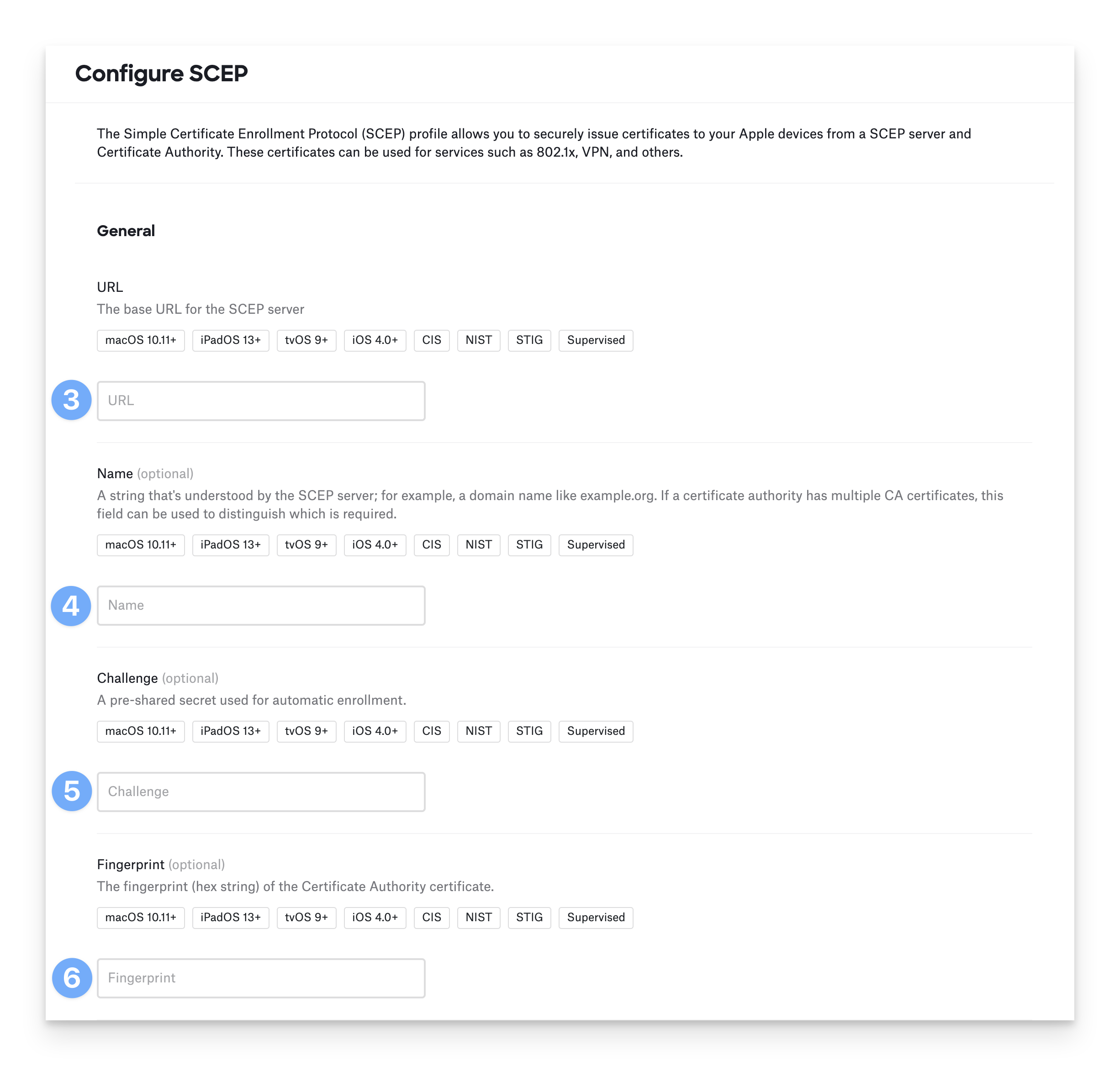
Click Configure SCEP Certificate. A drawer opens to allow you to configure SCEP options.
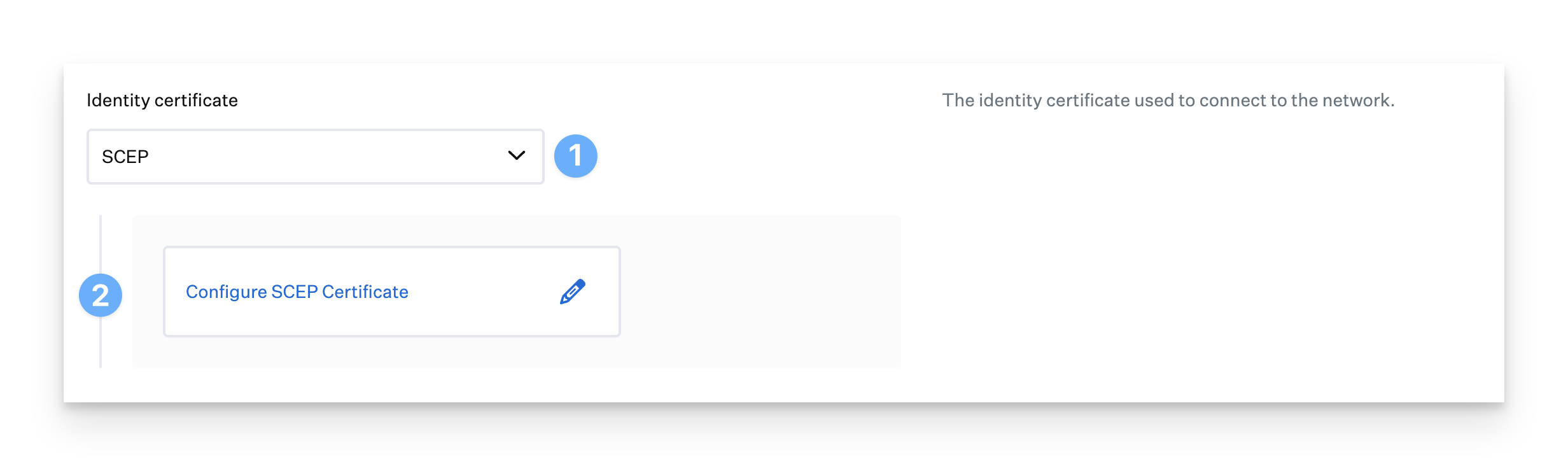
Enter the URL for the SCEP server for URL.
Optionally, specify a Name as needed by your SCEP server — usually the name of the CA where the SCEP service is requesting a certificate.
Optionally, enter the pre-shared key as the Challenge the SCEP server expects.
Optionally, enter the expected Fingerprint of the certificate authority’s certificate.
Optionally, provide the name you want to appear as the certificate identity’s Subject. You can use a static value or a global variable, such as CN=$EMAIL.
Select Specify Subject Alternative Names (SAN)if you want to provide SANs for the certificate identity.
For each SAN you would like to provide, click Add SAN Type
Select the SAN type you want to add: DNS Name, RFC 822 Name, Uniform Resource Identifier, or NT Principal Name.
Enter the associated value you would like to add for each SAN type. You can use a static value or use a global variable.
Choose the Key size. Work with your network administrator to ensure you choose a compatible key size — longer keys provide increased security.
For Key usage, choose whether to allow the keys to be used for Signing, Encryption, Both signing and encryption, or None. Work with your network administrator to determine which entitlements are necessary.
If you want the device to retry obtaining a certificate if the first attempt fails automatically, select Retries, then enter the number of retries to attempt — the default is 3.
If you want to introduce a delay between retries, select Retry delay and specify the number of seconds between retries. The default is a 10 seconds delay between retries.
Select Don’t allow key to be extracted to prevent exporting the certificate identity’s private key from the macOS Keychain.
Select Allow access to all apps if you want to automatically allow all apps to access and use the certificate identity’s private key.
Select Certificate expiration notification and specify the number of days before the certificate expires to start notifying the user. The default is to notify the user 14 days before expiration.
Select Automatic profile redistribution to automatically renew the certificate the specified number of days before it expires. The default is to automatically renew the certificate 30 days before expiration.
Click Done.
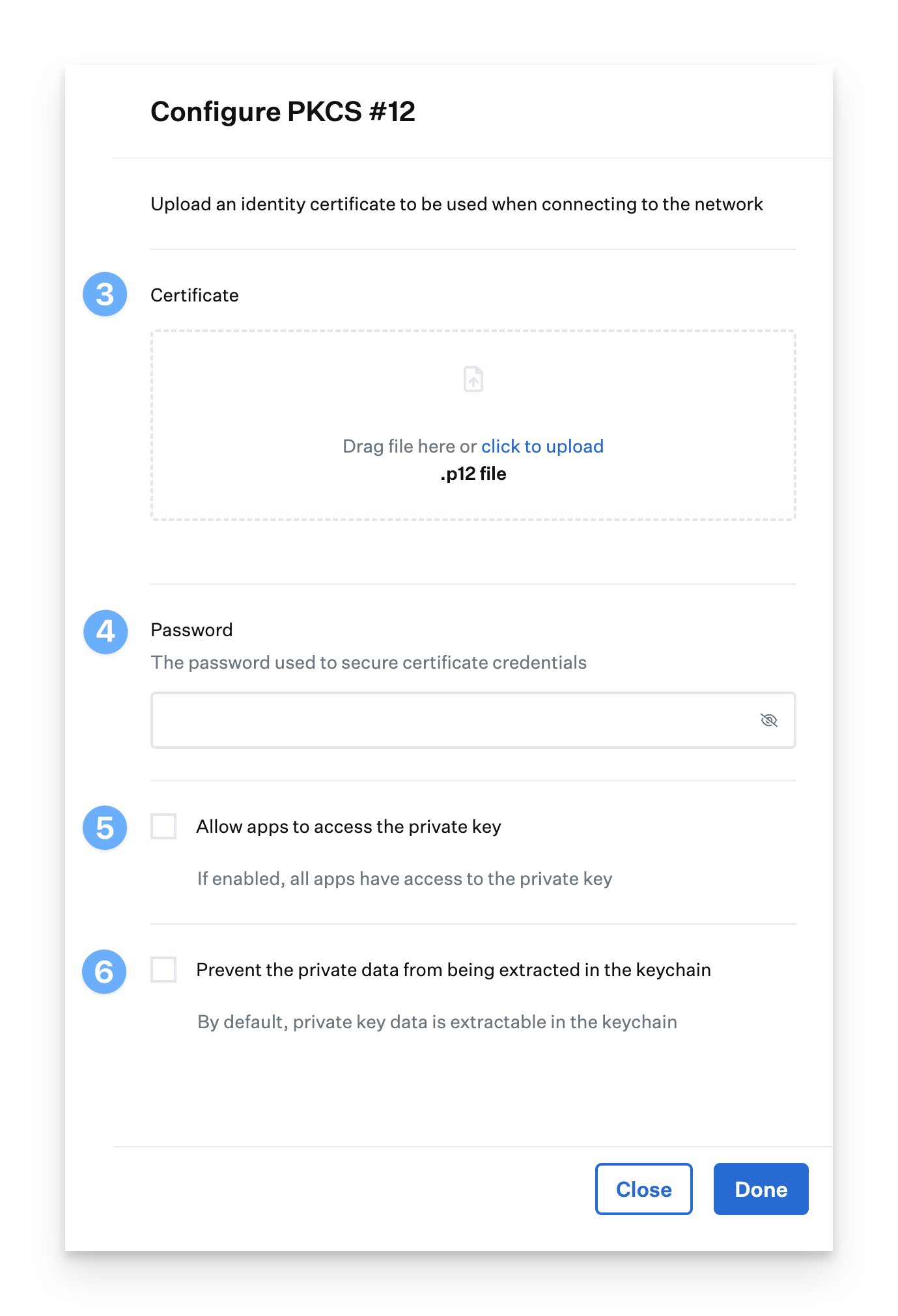
Import a PKCS #12 File
You can provide a single identity certificate for all configured devices by uploading a PKCS #12 formatted file. This means all devices will use the same certificate, making it harder for network administrators to identify individual devices by their login. However, it also means that if the certificate is compromised, it can be used to access the network. Revoking this certificate will block all configured devices from accessing the network.
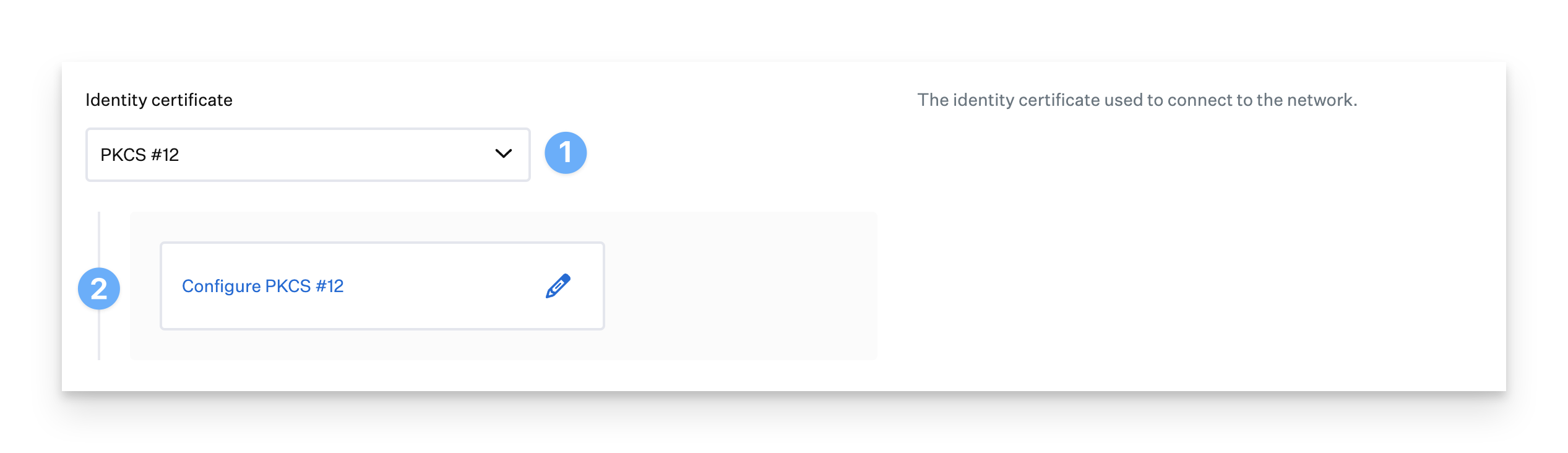
If you wish to provide a certificate in PKCS #12 format, choose PKCS #12 for the Identity certificate.
Click Configure PKCS #12 to open the Configure PKCS #12 drawer.
Upload the PKCS #12 encoded certificate for the Certificate.
In the Password field, provide the password to the PKCS #12 file.
If you want apps to access the private key of the certificate, select Allow apps to access the private key.
If you do not want the user to be able to export the private key using the keychain, select Prevent the private data from being extracted in the keychain.
Click Done.